Threat actors affiliated with a ransomware strain acknowledged as Participate in are leveraging a under no circumstances-just before-noticed exploit chain that bypasses blocking guidelines for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution (RCE) by way of Outlook Web Obtain (OWA).
“The new exploit process bypasses URL rewrite mitigations for the Autodiscover endpoint,” CrowdStrike scientists Brian Pitchford, Erik Iker, and Nicolas Zilio stated in a complex publish-up revealed Tuesday.
Participate in ransomware, which 1st surfaced in June 2022, has been exposed to undertake several techniques employed by other ransomware households these as Hive and Nokoyawa, the latter of which upgraded to Rust in September 2022.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The cybersecurity company’s investigations into various Participate in ransomware intrusions located that initial access to the concentrate on environments was not obtained by immediately exploiting CVE-2022-41040, but instead by the OWA endpoint.
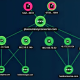
Dubbed OWASSRF, the system very likely will take edge of yet another critical flaw tracked as CVE-2022-41080 (CVSS rating: 8.8) to obtain privilege escalation, followed by abusing CVE-2022-41082 for remote code execution.
It really is truly worth noting that the two CVE-2022-41040 and CVE-2022-41080 stem from a scenario of server-aspect ask for forgery (SSRF), which permits an attacker to obtain unauthorized internal assets, in this case the PowerShell remoting service.
CrowdStrike stated the effective first access enabled the adversary to fall legit Plink and AnyDesk executables to keep persistent obtain as nicely as consider steps to purge Windows Occasion Logs on contaminated servers to conceal the malicious exercise.
All 3 vulnerabilities were resolved by Microsoft as element of its Patch Tuesday updates for November 2022. It can be, on the other hand, unclear if CVE-2022-41080 was actively exploited as a zero-day together with CVE-2022-41040 and CVE-2022-41082.
The Windows maker, for its part, has tagged CVE-2022-41080 with an “Exploitation A lot more Likely” assessment, implying it can be feasible for an attacker to develop exploit code that could be utilized to reliably weaponize the flaw.
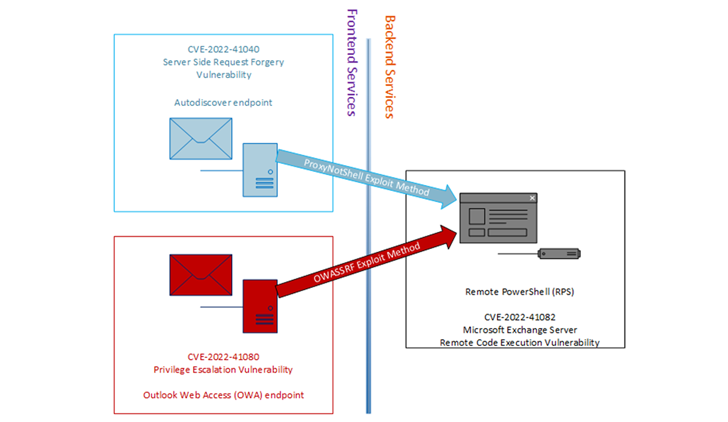
CrowdStrike further noted that a proof-of-notion (PoC) Python script uncovered and leaked by Huntress Labs researcher Dray Agha final 7 days may have been set to use by the Engage in ransomware actors for first access.
This is evidenced by the actuality that the execution of the Python script produced it attainable to “replicate the logs produced in the latest Participate in ransomware attacks.”
“Corporations really should apply the November 8, 2022 patches for Trade to stop exploitation considering that the URL rewrite mitigations for ProxyNotShell are not powerful versus this exploit process,” the researchers mentioned.
Located this report exciting? Comply with us on Twitter and LinkedIn to examine much more distinctive articles we article.
Some parts of this write-up are sourced from:
thehackernews.com

 Ukraine’s DELTA Military System Users Under Attack from Info Stealing Malware
Ukraine’s DELTA Military System Users Under Attack from Info Stealing Malware