The Pc Unexpected emergency Reaction Staff of Ukraine (CERT-UA) this 7 days disclosed that consumers of the Delta situational recognition method received phishing email messages from a compromised email account belonging to the Ministry of Defense.
The attacks, which have been attributed to a risk cluster dubbed UAC-0142, aimed to infect devices with two parts of data-thieving malware referred to as FateGrab and StealDeal.
Delta is a cloud-based mostly operational situation exhibit procedure designed by Aerorozvidka that permits authentic-time monitoring of troops on the battlefield, earning it a worthwhile target for danger actors.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
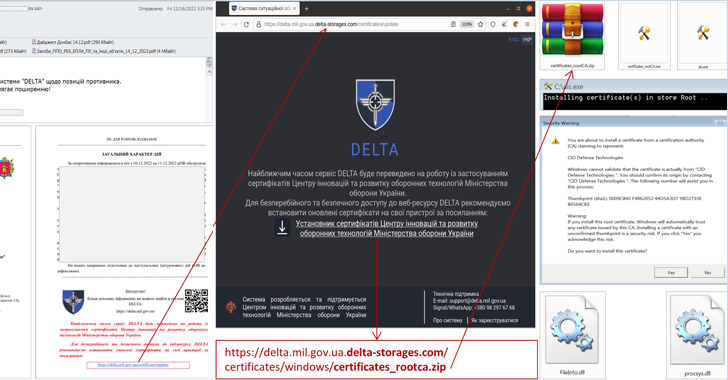
The lure messages, which occur with phony warnings to update root certificates in the Delta software program, have PDF documents containing hyperlinks to archive documents hosted on a fraudulent Delta area, in the long run dropping the malware on compromised techniques.

Even though FateGrab is mostly designed to exfiltrate documents with certain extensions as a result of File Transfer Protocol (FTP), StealDeal singles out web browsers to siphon passwords and other information.
The attack will come times following Ukraine offered the Delta process to the NATO Consultation, Command, and Command Corporation (NC3O). It also follows revelations that the Russia-linked Gamaredon team attempted to unsuccessfully infiltrate a substantial petroleum refining enterprise inside a NATO member state in late August 2022.
The Russo-Ukrainian war has prompted Moscow to intensify cyberattacks towards Ukraine, relying on a large array of wiper malware to disrupt critical infrastructure.
Ukrainian businesses, in latest months, have also been specific with RomCom RAT and Vidar stealer, the latter of which has been discovered to act as a conduit to fall a ransomware strain named Somnia.
Previously this thirty day period, CERT-UA mentioned that condition-owned businesses have been focused with phishing e-mails purporting to be from the Point out Crisis Assistance of Ukraine and that contains weaponzied RAR archives that are engineered to deploy a Delphi-primarily based backdoor named DolphinCape.
Discovered this report appealing? Abide by us on Twitter and LinkedIn to study much more unique information we post.
Some parts of this short article are sourced from:
thehackernews.com

 Organizations Warned of New Attack Vector in Amazon Web Services
Organizations Warned of New Attack Vector in Amazon Web Services