Google on Tuesday claimed it truly is piloting a new feature in Chrome known as Product Certain Session Credentials (DBSC) to enable shield end users from session cookie theft by malware.
The prototype – presently tested in opposition to “some” Google Account end users operating Chrome Beta – is constructed with an aim to make it an open web normal, the tech giant’s Chromium group reported.
“By binding authentication classes to the machine, DBSC aims to disrupt the cookie theft marketplace due to the fact exfiltrating these cookies will no for a longer time have any price,” the business mentioned.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“We think this will significantly minimize the achievement price of cookie theft malware. Attackers would be forced to act locally on the system, which makes on-gadget detection and cleanup a lot more helpful, both of those for anti-virus software program as properly as for organization managed equipment.”
The development comes on the back again of experiences that off-the-shelf info stealing malware are finding ways to steal cookies in a fashion that makes it possible for threat actors to bypass multi-factor authentication (MFA) defense and attain unauthorized entry to on line accounts.

These kinds of session hijacking strategies are not new. In Oct 2021, Google’s Threat Analysis Group (TAG) thorough a phishing marketing campaign that targeted YouTube articles creators with cookie thieving malware to hijack their accounts and monetize the obtain for perpetrating cryptocurrency cons.
Earlier this January, CloudSEK revealed that info stealers like Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake have up to date their abilities to hijack user sessions and enable ongoing entry to Google expert services even following a password reset.
Google informed The Hacker News at the time that “attacks involving malware that steal cookies and tokens are not new we routinely update our defenses in opposition to these kinds of strategies and to safe customers who drop target to malware.”
It further more recommended end users to enable Improved Safe Browsing in the Chrome web browser to protect against phishing and malware downloads.
DBSC aims to slash down on these types of destructive efforts by introducing a cryptographic strategy that ties together the sessions to the product such that it helps make it more challenging for the adversaries to abuse the stolen cookies and hijack the accounts.
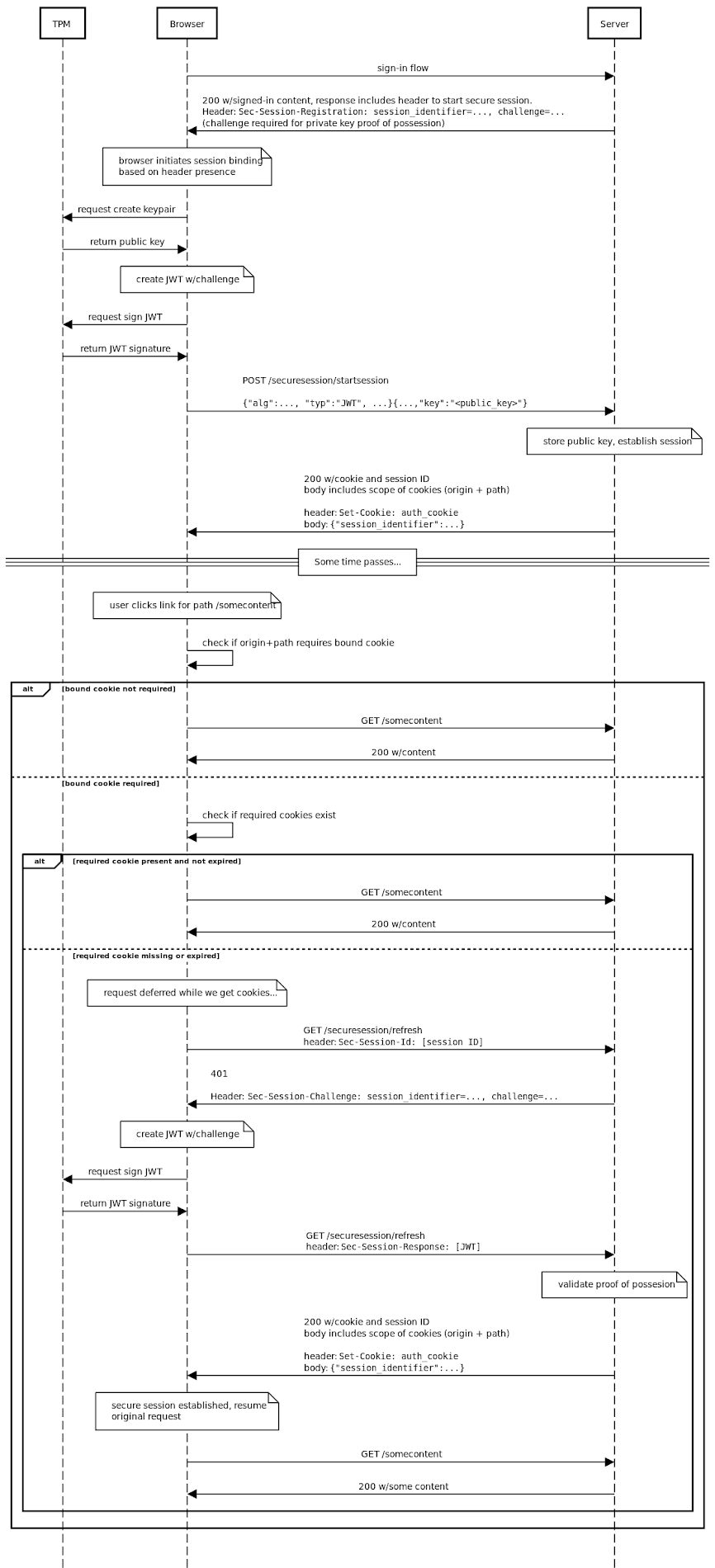
Available by way of an API, the new element achieves this by permitting a server to affiliate a session with a public vital made by the browser as section of a public/non-public crucial pair when a new session is introduced.
It is worth noting that the essential pair is stored domestically on the gadget working with Trustworthy Platform Modules (TPMs). In addition, the DBSCI API permits the server to confirm evidence-of-possession of the personal crucial during the session life span to make certain the session is energetic on the similar product.
“DBSC offers an API for web sites to command the life span of these keys, powering the abstraction of a session, and a protocol for periodically and mechanically proving possession of people keys to the website’s servers,” Google’s Kristian Monsen and Arnar Birgisson reported.
“There is a separate key for each session, and it should really not be possible to detect that two diverse session keys are from just one gadget. By machine-binding the non-public essential and with appropriate intervals of the proofs, the browser can limit malware’s skill to offload its abuse off of the user’s gadget, substantially increasing the prospect that both the browser or server can detect and mitigate cookie theft.”

1 important caveat is that DBSC banking institutions on user devices getting a protected way of signing problems though safeguarding personal keys from exfiltration by malware, necessitating that the web browser has obtain to the TPM.
Google said guidance for DBSC will be to begin with rolled out to about 50 % of Chrome’s desktop users centered on the hardware capabilities of their machines. The newest challenge is also predicted to be in sync with the firm’s broader plans to sunset 3rd-party cookies in the browser by the finish of the calendar year by using the Privacy Sandbox initiative.
“This is to make confident that DBSC does not grow to be a new tracking vector at the time third-party cookies are phased out, even though also making sure that these kinds of cookies can be completely guarded in the meantime,” it mentioned. “If the consumer entirely opts out of cookies, 3rd-party cookies, or cookies for a particular web page, this will disable DBSC in people scenarios as very well.”
The firm further observed that it really is engaging with quite a few server providers, id suppliers (IdPs), and browser sellers like Microsoft Edge and Okta, who have expressed fascination in DBSC. Origin trials for DBSC for all supported web-sites are established to begin by the stop of the yr.
Discovered this short article attention-grabbing? Comply with us on Twitter and LinkedIn to examine extra unique content we publish.
Some pieces of this write-up are sourced from:
thehackernews.com


 Attack Surface Management vs. Vulnerability Management
Attack Surface Management vs. Vulnerability Management