Attack surface management (ASM) and vulnerability management (VM) are usually puzzled, and even though they overlap, they are not the exact same. The key variance concerning attack floor management and vulnerability management is in their scope: vulnerability administration checks a record of regarded property, even though attack surface management assumes you have unfamiliar property and so begins with discovery. Let us look at equally in extra detail.
What is vulnerability management?
Vulnerability management is, at the most basic level, the use of automated equipment to identify, prioritize and report on security issues and vulnerabilities in your electronic infrastructure.
Vulnerability administration takes advantage of automatic scanners to run normal, scheduled scans on belongings in just a known IP range to detect recognized and new vulnerabilities, so you can apply patches, clear away vulnerabilities or mitigate any opportunity challenges. These vulnerabilities are likely to use a risk score or scale – these types of as CVSS – and risk calculations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Vulnerability scanners frequently have lots of hundreds of automated checks at their disposal, and by probing and collecting information and facts about your units, they can recognize security gaps which could be made use of by attackers to steal sensitive facts, gain unauthorized access to your devices, or disrupt your company. Armed with this information, you can guard your firm and protect against probable attacks.
 A screenshot of the Intruder vulnerability management system, which is developed to carry out 1000’s of security checks, figuring out vulnerabilities in web applications, APIs, cloud methods, and past.
A screenshot of the Intruder vulnerability management system, which is developed to carry out 1000’s of security checks, figuring out vulnerabilities in web applications, APIs, cloud methods, and past.
What is the vulnerability administration course of action?
What is attack area administration?
The most important big difference among vulnerability administration and attack floor management is the scope. Attack surface area management (ASM) contains asset discovery – helping you to discover all your digital belongings and providers and then minimizing or reducing their exposure to avoid hackers from exploiting them.
With ASM, all identified or unidentified assets (on-premises, cloud, subsidiary, 3rd-party, or partner environments) are detected from the attacker’s point of view from outside the organization. If you do not know what you’ve obtained, how can you protect it?
Take the illustration of an admin interface like cPanel or a firewall administration web site – these may possibly be protected in opposition to all recognized latest attacks now, but a vulnerability could be discovered tomorrow – when it turns into a substantial risk. If you keep an eye on and minimize your attack surface, regardless of vulnerabilities, you turn out to be harder to attack.
So, a major section of attack area administration is decreasing exposure to probable foreseeable future vulnerabilities by removing needless providers and belongings from the internet. But to do this, initial you need to know what’s there.
What is the attack floor administration system?
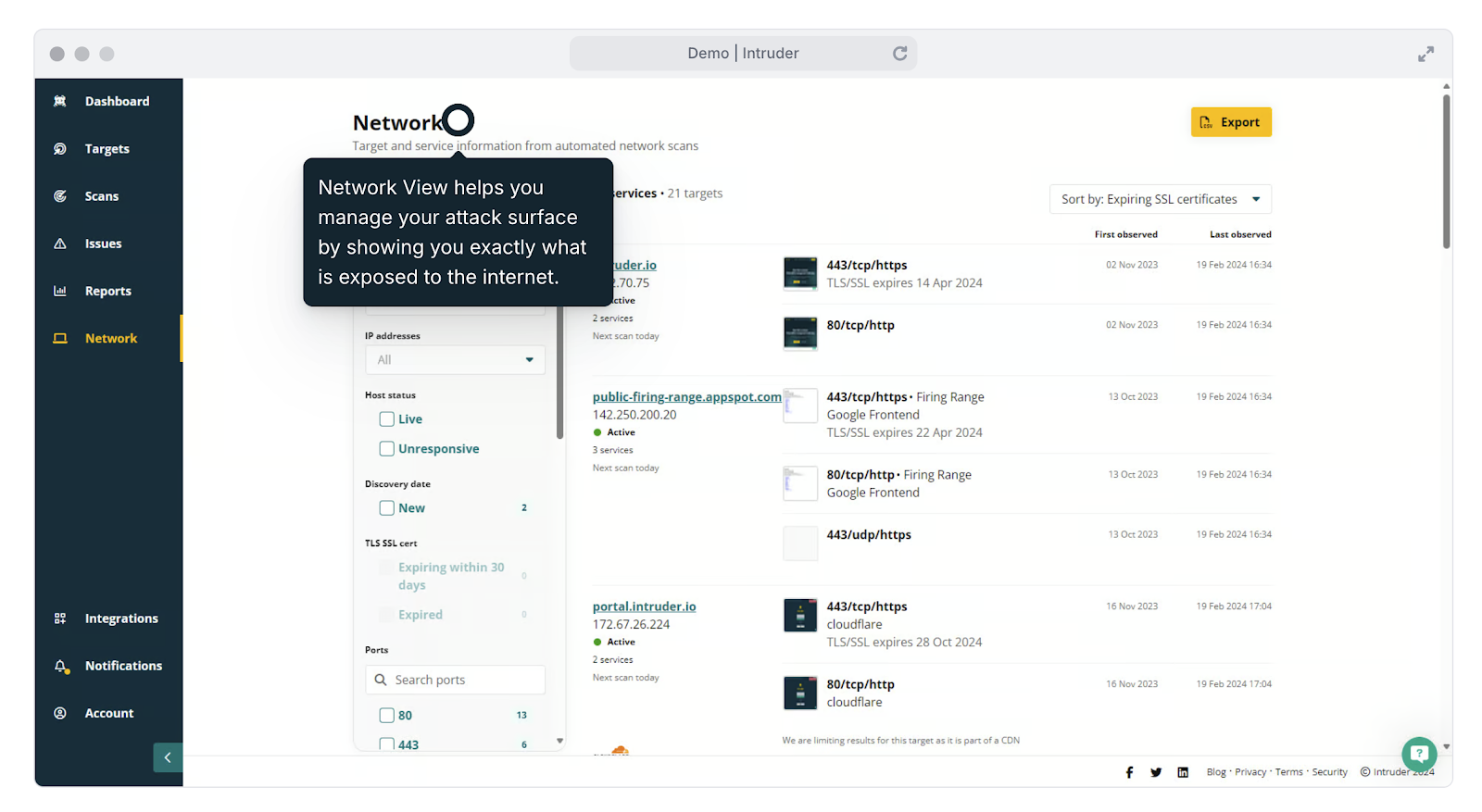 Intruder’s attack surface administration capabilities assistance you to keep on top of modifications in your atmosphere, such as not long ago opened ports and expert services.
Intruder’s attack surface administration capabilities assistance you to keep on top of modifications in your atmosphere, such as not long ago opened ports and expert services.
How does attack surface administration differ from vulnerability administration?
Vulnerability administration is the approach of determining and prioritizing vulnerabilities in your IT infrastructure and programs. Attack area administration goes a stage even further by pinpointing and examining your attack area – all the products, entry details and uncovered solutions that an attacker could perhaps use to obtain access to your devices or information.
Can you combine Attack Surface area Management and Vulnerability Management?
When ASM and VM could have distinct scopes and targets, they are not mutually exceptional. Made use of in mix, they create a much extra holistic, robust and comprehensive cyber security posture. By figuring out your assets and vulnerabilities, you can prioritize your security efforts and allocate assets extra efficiently – which will help you reduce the chance of a effective attack and any probable effects.
How Intruder can enable with ASM and VM
Eventually, you want to leave no stone unturned when it arrives to cyber security. Modern-day VM and ASM alternatives like Intruder can detect vulnerabilities affecting your business. It gives you bigger visibility and handle over your attack floor, displays network alterations and SSL/TLS certificate expiry dates, can help you stay on top of your cloud infrastructure, and permits you to pay only for lively targets. Why not see for on your own with a absolutely free 14-working day demo?
Discovered this report fascinating? This write-up is a contributed piece from just one of our valued companions. Adhere to us on Twitter and LinkedIn to read through additional unique material we submit.
Some elements of this post are sourced from:
thehackernews.com


 Mispadu Trojan Targets Europe, Thousands of Credentials Compromised
Mispadu Trojan Targets Europe, Thousands of Credentials Compromised