The banking trojan regarded as Mispadu has expanded its concentration outside of Latin The usa (LATAM) and Spanish-talking folks to goal users in Italy, Poland, and Sweden.
Targets of the ongoing marketing campaign include entities spanning finance, services, motor automobile manufacturing, legislation corporations, and business services, according to Morphisec.
“Irrespective of the geographic growth, Mexico stays the principal concentrate on,” security researcher Arnold Osipov mentioned in a report printed past 7 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The campaign has resulted in thousands of stolen credentials, with data dating again to April 2023. The risk actor leverages these qualifications to orchestrate malicious phishing e-mail, posing a important danger to recipients.”
Mispadu, also known as URSA, arrived to light in 2019, when it was observed carrying out credential theft actions aimed at economical institutions in Brazil and Mexico by exhibiting bogus pop-up windows. The Delphi-based malware is also able of having screenshots and capturing keystrokes.
Typically dispersed by way of spam email messages, modern attack chains have leveraged a now-patched Windows SmartScreen security bypass flaw (CVE-2023-36025, CVSS score: 8.8) to compromise users in Mexico.

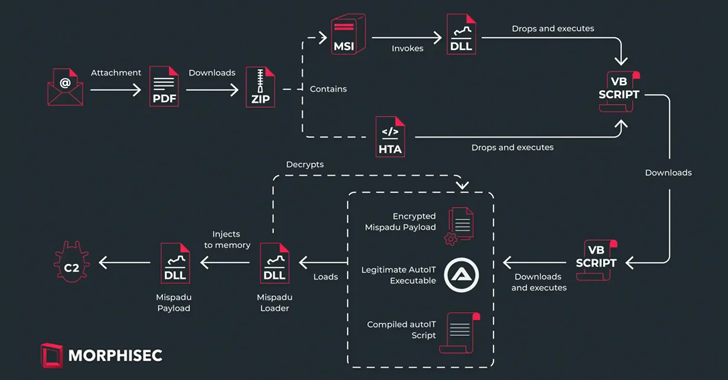
The an infection sequence analyzed by Morphisec is a multi-stage approach that commences with a PDF attachment existing in bill-themed email messages that, when opened, prompts the receiver to click on on a booby-trapped backlink to obtain the finish invoice, resulting in the down load of a ZIP archive.
The ZIP comes with both an MSI installer or an HTA script that is responsible for retrieving and executing a Visual Essential Script (VBScript) from a distant server, which, in transform, downloads a 2nd VBScript that ultimately downloads and launches the Mispadu payload utilizing an AutoIT script but right after it is really decrypted and injected into memory by indicates of a loader.
“This [second] script is heavily obfuscated and employs the very same decryption algorithm as talked about in the DLL,” Osipov mentioned.
“Prior to downloading and invoking the up coming stage, the script conducts many Anti-VM checks, such as querying the computer’s product, company, and BIOS variation, and evaluating them to these related with digital devices.”
The Mispadu attacks are also characterized by the use of two unique command-and-regulate (C2) servers, one particular for fetching the intermediate and ultimate-stage payloads and a further for exfiltrating the stolen qualifications from around 200 services. There are now a lot more than 60,000 information in the server.
The growth comes as the DFIR Report in depth a February 2023 intrusion that entailed the abuse of malicious Microsoft OneNote information to drop IcedID, employing it to fall Cobalt Strike, AnyDesk, and the Nokoyawa ransomware.
Microsoft, accurately a yr in the past, announced that it would start off blocking 120 extensions embedded inside of OneNote files to stop its abuse for malware delivery.
YouTube Films for Video game Cracks Provide Malware
The conclusions also come as enterprise security business Proofpoint stated several YouTube channels selling cracked and pirated online video video games are performing as a conduit to supply data stealers these types of as Lumma Stealer, Stealc, and Vidar by incorporating destructive back links to video descriptions.

“The movies purport to present an close person how to do items like obtain software program or update online video game titles for cost-free, but the connection in the video clip descriptions potential customers to malware,” security researcher Isaac Shaughnessy said in an analysis revealed nowadays.
There is evidence to recommend that this sort of videos are posted from compromised accounts, but there is also the possibility that the risk actors behind the operation have produced quick-lived accounts for dissemination reasons.
All the films incorporate Discord and MediaFire URLs that position to password-safeguarded archives that in the end lead to the deployment of the stealer malware.
Proofpoint said it determined multiple distinctive activity clusters propagating stealers via YouTube with an aim to one out non-enterprise end users. The campaign has not been attributed to a single danger actor or group.
“The procedures utilised are related, on the other hand, like the use of video descriptions to host URLs leading to malicious payloads and supplying instructions on disabling antivirus, and working with equivalent file sizes with bloating to attempt to bypass detections,” Shaughnessy reported.
Located this article fascinating? Stick to us on Twitter and LinkedIn to read through more special articles we put up.
Some elements of this article are sourced from:
thehackernews.com

 Critical Security Flaw Found in Popular LayerSlider WordPress Plugin
Critical Security Flaw Found in Popular LayerSlider WordPress Plugin