A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract sensitive details from databases, this sort of as password hashes.
The flaw, selected as CVE-2024-2879, carries a CVSS score of 9.8 out of a most of 10.. It has been described as a situation of SQL injection impacting versions from 7.9.11 via 7.10..
The issue has been resolved in variation 7.10.1 launched on March 27, 2024, adhering to responsible disclosure on March 25. “This update includes vital security fixes,” the maintainers of LayerSlider reported in their launch notes.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
LayerSlider is a visual web content material editor, a graphic style and design application, and a digital visual effects that allows buyers to produce animations and prosperous information for their websites. According to its personal site, the plugin is employed by “hundreds of thousands of customers globally.”

The flaw found out in the device stems from a situation of inadequate escaping of consumer supplied parameters and the absence of wpdb::prepare(), enabling unauthenticated attackers to append added SQL queries and glean sensitive info, Wordfence claimed.
The enhancement follows the discovery of an unauthenticated stored cross-internet site scripting (XSS) flaw in the WP-Members Membership Plugin (CVE-2024-1852, CVSS rating: 7.2) that could facilitate the execution of arbitrary JavaScript code. It has been solved in edition 3.4.9.3.
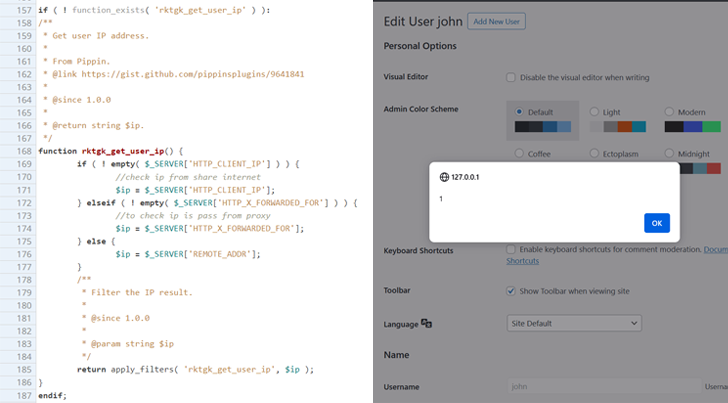
The vulnerability, owing to inadequate input sanitization and output escaping, “tends to make it attainable for unauthenticated attackers to inject arbitrary web scripts in web pages that will execute anytime a consumer accesses an injected website page which is the edit users webpage,” the WordPress security business explained.
Should the code be executed in the context of an administrator’s browser session, it can be applied to build rogue person accounts, redirect web page visitors to other malicious websites, and have out other attacks, it additional.
More than the previous handful of months, security vulnerabilities have also been disclosed in other WordPress plugins this kind of as Tutor LMS (CVE-2024-1751, CVSS score: 8.8) and Get hold of Sort Entries (CVE-2024-2030, CVSS rating: 6.4) that could be exploited for facts disclosure and inject arbitrary web scripts, respectively.
Discovered this short article appealing? Follow us on Twitter and LinkedIn to study much more distinctive content we article.
Some pieces of this posting are sourced from:
thehackernews.com


 Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution
Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution