The malicious code inserted into the open up-resource library XZ Utils, a commonly used bundle current in key Linux distributions, is also capable of facilitating remote code execution, a new evaluation has uncovered.
The audacious offer chain compromise, tracked as CVE-2024-3094 (CVSS score: 10.), arrived to light previous week when Microsoft engineer and PostgreSQL developer Andres Freund alerted to the presence of a backdoor in the details compression utility that presents distant attackers a way to sidestep protected shell authentication and acquire entire obtain to an afflicted process.
XZ Utils is a command-line resource for compressing and decompressing data in Linux and other Unix-like functioning programs.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The destructive code is reported to have been deliberately released by 1 of the task maintainers named Jia Tan (aka Jia Cheong Tan or JiaT75) in what appears to be a meticulous attack spanning several a long time. The GitHub person account was made in 2021. The identity of the actor(s) is presently mysterious.

“The danger actor started out contributing to the XZ challenge nearly two yrs back, bit by bit creating believability until eventually they were presented maintainer obligations,” Akamai explained in a report.
In a additional act of clever social engineering, sockpuppet accounts like Jigar Kumar and Dennis Ens are believed to have been utilised to ship characteristic requests and report a selection of issues in the software in order to drive the initial maintainer – Lasse Collin of the Tukaani Challenge – to incorporate a new co-maintainer to the repository.
Enter Jia Tan, who introduced a series of changes to XZ Utils in 2023, which eventually designed their way to launch variation 5.6. in February 2024. They also harbored a innovative backdoor.
 Source: Thomas Roccia
Source: Thomas Roccia
“As I have hinted in earlier e-mails, Jia Tan may well have a even bigger part in the task in the long term,” Collin mentioned in an exchange with Kumar in June 2022.
“He has been encouraging a ton off-checklist and is virtually a co-maintainer already. 🙂 I know that not a great deal has transpired in the git repository however but points transpire in modest steps. In any situation some transform in maintainership is already in development at the very least for XZ Utils.”
The backdoor affects XZ Utils 5.6. and 5.6.1 launch tarballs, the latter of which is made up of an enhanced variation of the exact same implant. Collins has because acknowledged the project’s breach, stating the two the tarballs were being created and signed by Jia Tan and that they had access only to the now-disabled GitHub repository.
“This is evidently a quite intricate point out-sponsored procedure with outstanding sophistication and multi-yr preparing,” firmware security company Binarly stated. “This kind of a advanced and skillfully created thorough implantation framework is not produced for a one-shot procedure.”
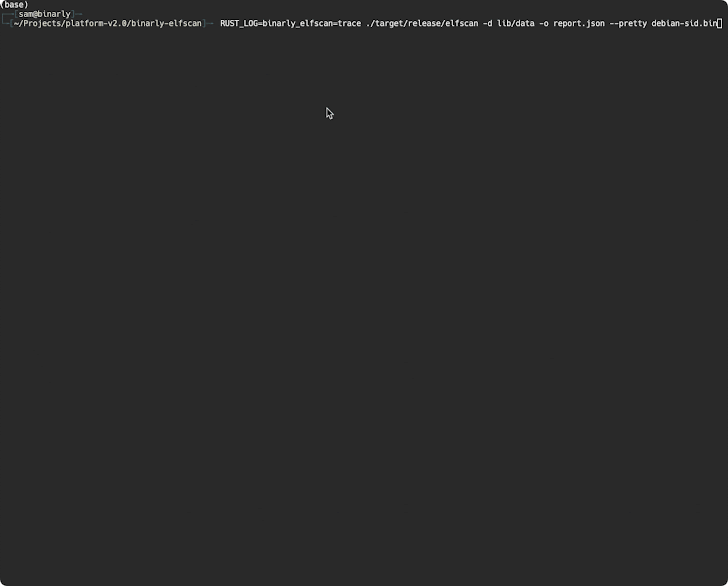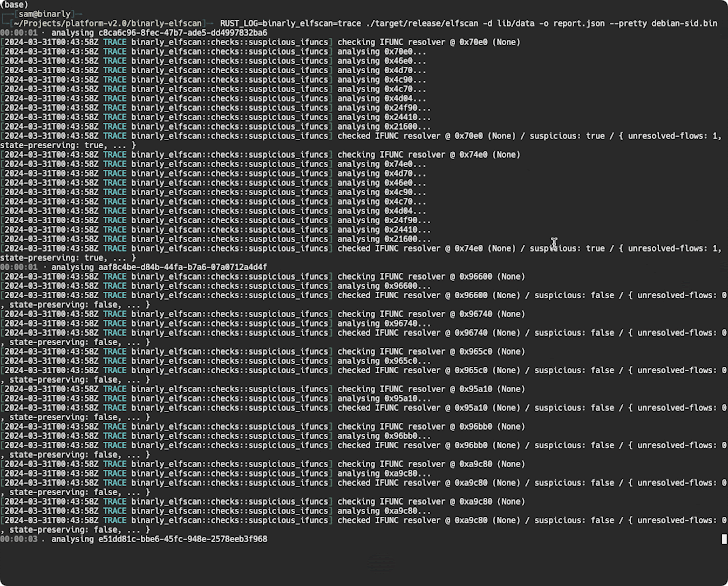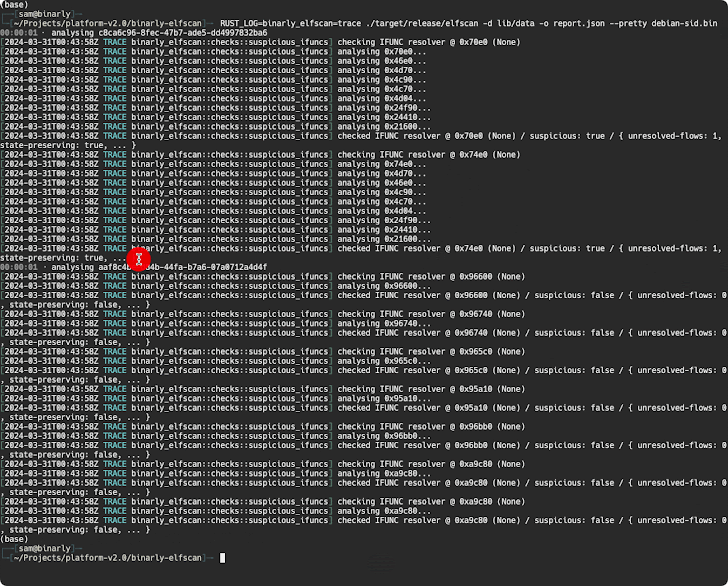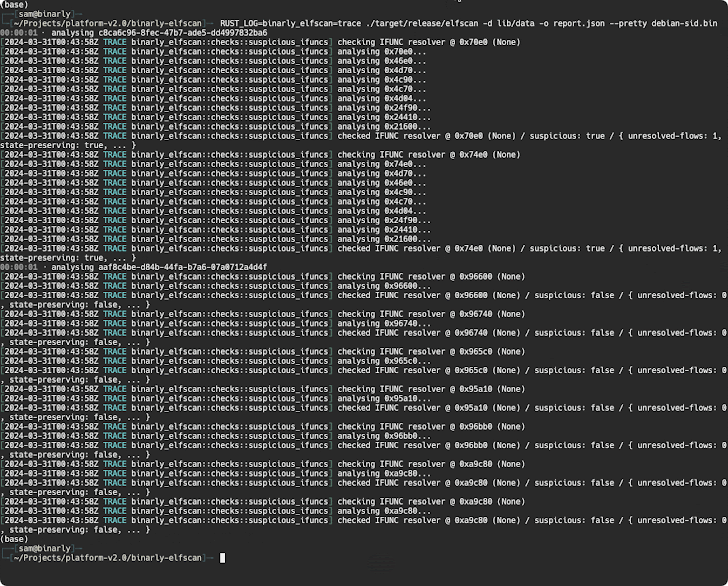
A further examination of the backdoor by open-source cryptographer Filippo Valsorda has also uncovered that the influenced variations make it possible for distinct distant attackers to deliver arbitrary payloads via an SSH certificate which will be executed in a fashion that circumvents authentication protocols, effectively seizing management more than the sufferer machine.
“It seems as though the backdoor is extra to the SSH daemon on the vulnerable machine, enabling a distant attacker to execute arbitrary code,” Akamai mentioned. “This usually means that any equipment with the vulnerable deal that exposes SSH to the internet is possibly vulnerable.”

Pointless to say, the accidental discovery by Freund is a single of the most considerable source chain attacks discovered to date and could have been a critical security disaster had the package deal been built-in into steady releases of Linux distributions.
“The most noteworthy portion of this supply chain attack is the extreme levels of devotion of the attacker, operating much more than two yrs to create on their own as a genuine maintainer, offering to choose up operate in different OSS tasks and committing code throughout multiple projects in purchase to avoid detection,” JFrog stated.
As with the case of Apache Log4j, the incident the moment all over again highlights the reliance on open up-source software and volunteer-run assignments, and the repercussions that could entail must they undergo a compromise or have a important vulnerability.
“The even bigger ‘fix’ is for organizations to adopt instruments and processes that permit them to detect indications of tampering and destructive functions within equally open up source and professional code made use of in their have development pipeline,” ReversingLabs said.
Observed this post intriguing? Stick to us on Twitter and LinkedIn to read far more unique articles we put up.
Some components of this article are sourced from:
thehackernews.com

 Harnessing the Power of CTEM for Cloud Security
Harnessing the Power of CTEM for Cloud Security