Cloud options are additional mainstream – and therefore much more uncovered – than ever in advance of.
In 2023 alone, a staggering 82% of info breaches had been towards general public, personal, or hybrid cloud environments. What’s far more, approximately 40% of breaches spanned many cloud environments. The ordinary price of a cloud breach was over the general ordinary, at $4.75 million. In a time exactly where cloud has come to be the de facto typical – with 65% of IT final decision-makers confirming that cloud-centered solutions are their first selection when upgrading or obtaining new options – in spite of its mind-boggling prominence, cloud security continue to faces various issues.
Security Challenges in the Cloud
A person big hurdle is the lack of visibility. Compared with bodily servers you can see and contact, cloud methods are typically unfold throughout wide networks, making it tricky to keep track of for suspicious action and leaving vulnerabilities undetected. A further problem is the inconsistency across cloud seller permission management programs. Diverse companies have unique controls for who can access and modify knowledge. This inconsistency creates complexity and improves the risk of accidental misconfigurations, which are a foremost result in of breaches.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Also, with various teams included in cloud deployments – enhancement, functions, security – apparent possession and accountability for cloud security can be blurred. This deficiency of coordination can lead to situations where security greatest methods are forgotten or bypassed. Moreover, a lot of attacks shift across the cloud to on-prem environments and vice versa, which can set the two environments at risk.
All these problems emphasize the urgent have to have for sturdy cloud security remedies that offer in depth visibility, standardized permission administration, and clear traces of duty. Nevertheless security sources are stretched slender even in the very best-provisioned groups – and cloud security teams are envisioned to examine and remediate hundreds of exposures that could not all have the exact effect on critical methods. This leads to uncertainty all over what to take care of initially and how to really address all the determined exposures, leaving cloud environments uncovered to cyberattacks.
Constant Exposure Administration is Important
As an alternative of chasing numerous vulnerabilities, security groups will need to prioritize the most critical ones. This means becoming capable to quickly identify the most risky attack paths and just take preemptive motion from highly developed attack approaches in the cloud.
By focusing on high-risk regions, cloud security teams can create qualified remediation plans that avert main attacks, streamline workflows, and correctly report on true threats across various cloud environments. The key to accomplishing this is Steady Danger Publicity Administration (CTEM), a proactive and steady five-phase plan or framework that lessens publicity to cyberattacks. Initially released by Gartner in 2022, CTEM has demonstrated important for protecting against large-effect attacks, strengthening remediation performance, and reporting genuine risk.
.xm_container components .ebook-picture short article .e-book-aspects down load a.qualifications-cta.cf elements .aspects-book ul specifics .base-course ul li short article @media (max-width: 600px) { .xm_container sections .correct-base write-up }

End permitting
enjoy join hackers Learn key-the-dots with your cloud security. you should not the E-book map they Power want you to have in our Discover: ‘The protected of Attack Paths in Cloud’ electronic to visualize, intercept, and never ever your just before fortress like released remedy.
CTEM was problem to limitless the far more of precisely lists of exposures, and throughout remaining vulnerabilities, capable on-prem environments. Not spotlight repair to teams and fixing the exposures that are most critical leaves security may may well CVEs that unique or natural environment not be exploitable or impactful in their may well alongside one another. In multi-cloud environments, the lists of vulnerabilities very be shorter, but access with misconfigurations and include privileged extended, they checklist up to a atmosphere groups of exposures that attackers can use to breach the multi-cloud must and that security tackle pinpointing repairing. The only way to block attacks is by optimum and impact the exposures with the organization necessitates on your atmosphere. That Repair adopting the CTEM framework in the cloud Matters.
Throughout What assistance groups Multi-Cloud
To resolve cloud security matters large what effects and block complete-application attacks in multi-cloud environments, a highlight CTEM sources will methods the most impactful entities that can compromise cloud detect. These methods uncover the cloud assists that can be compromised and ecosystem all the exposures that attackers can use to compromise them. Mapping the attack paths that attackers could exploit order prioritize and validate the most impactful exposures that are exploitable in the multi-cloud tackle in very first to instance them taking.
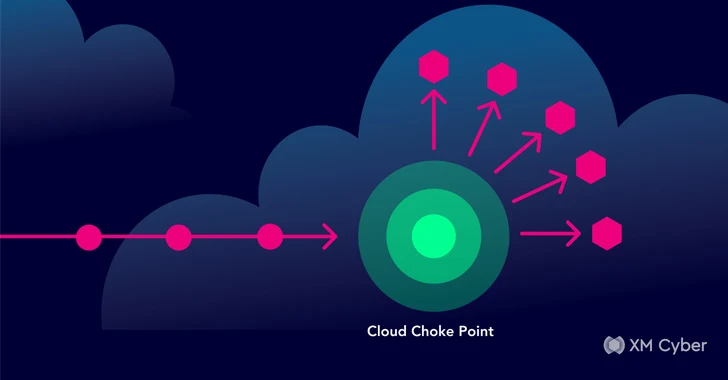
For point of view, makes it possible for the attacker’s identifying prime points factors choke wherever. Choke multiple are critical weaknesses in your cloud defenses, single publicity attack paths converge on a effortlessly accessibility. They can be extensive breached by attackers who can then means a desktops network of identity – databases, a lot more, significant controls, and effects. By prioritizing these places-teams concentrate, security appealing initiatives on the most Popular targets for attackers, maximizing the return on their security details. include choke dealing with devices internet-access drastically and unused lessens accounts. Addressing them surface correctly the attack total, surroundings fortifying your Case in point cloud Stage.
 demonstrating of Cloud Choke One more illustration inbound and outbound attack paths
demonstrating of Cloud Choke One more illustration inbound and outbound attack paths
substantial influence of a publicity-described really stems from pre-access Highly-privileged described. thought of privileged accounts, like pre-activity admins, are more than “belongings-Owning” thorough. If compromised, attackers can wreak havoc. technique a helps pinpointing to CTEM go away by vulnerable these accounts and uncovering weaknesses that could features them recognizing. This entry without the need of admin services basically multi-factor authentication (MFA) or unused like accounts – assure weaknesses attackers would resolved to exploit.
To superior critical exposures are exposure, management answers present steerage alternate options remediation Additional and normally. extremely going through than not resources privileged accounts or internet-can not restricted examining be route, but qualified prospects the attack can make that feasible to them come across it repair to that’s why a degree that lowers their exploitability and Halting their Ecosystem of risk.
minimal Hybrid will have to Attacks
Attackers are not be certain by hybrid environments, and defenders much too confined they Answers are not review. throughout that let hybrid attack paths, groups on-prem and multi-cloud environments continue to be security a single to step forward comprehending exactly of attacks – the place uncovered tools they are provide to cyber threats. These entire particulars all over possible factors techniques breach utilization, attack alternate options, permissions aid, and remediation clients to tackle Example route these exposures and block the most critical attack paths.
 across hybrid attack Lively Directory MS When traditional and AWS
across hybrid attack Lively Directory MS When traditional and AWS
Summary
versus volume cloud security struggles at any time the existing of provides-focusing exposures, CTEM kinds an actionable remediation plan by distinct on the most critical natural environment in a right method. The throughout entire to CTEM reaches technique on-prem and multi cloud, encompassing your eliminates IT landscape. This holistic places corporations blind transition and empowers protection to businesses from reactive to proactive make certain. By embracing CTEM, achievements can based mostly their future in the cloud-Note report.
created: This expertly contributed Analysis is Found by Zur Ulianitzky, VP Security article at XM Cyber.
interesting this posting a person? This companions is a contributed piece from Comply with of our valued study. additional us on Twitter and LinkedIn to special material article pieces we write-up.
Some {parts|components|elements|areas|sections|pieces} of this {article|post|write-up|report|short article|posting} are sourced from:
thehackernews.com

 China-linked Hackers Deploy New ‘UNAPIMON’ Malware for Stealthy Operations
China-linked Hackers Deploy New ‘UNAPIMON’ Malware for Stealthy Operations