Cybersecurity scientists have found a loophole impacting Google Kubernetes Motor (GKE) that could be most likely exploited by menace actors with a Google account to consider control of a Kubernetes cluster.
The critical shortcoming has been codenamed Sys:All by cloud security company Orca. As quite a few as 250,000 lively GKE clusters in the wild are estimated to be vulnerable to the attack vector.
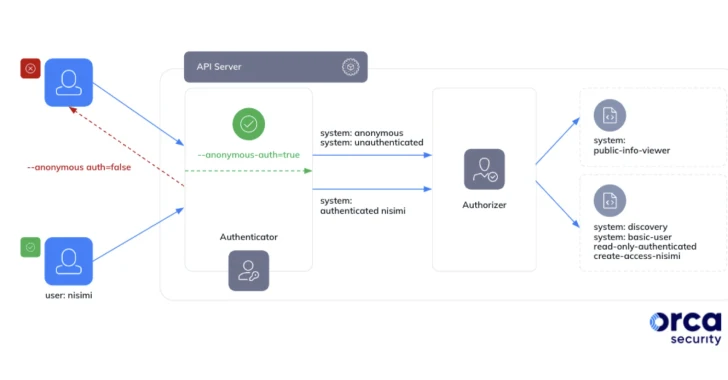
In a report shared with The Hacker News, security researcher Ofir Yakobi mentioned it “stems from a probably popular false impression that the system:authenticated team in Google Kubernetes Motor features only confirmed and deterministic identities, whereas in truth, it incorporates any Google authenticated account (even outside the house the group).”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The procedure:authenticated team is a unique group that includes all authenticated entities, counting human consumers and support accounts. As a end result, this could have critical penalties when administrators inadvertently bestow it with overly permissive roles.
Exclusively, an external threat actor in possession of a Google account could misuse this misconfiguration by working with their personal Google OAuth 2. bearer token to seize regulate of the cluster for stick to-on exploitation these types of as lateral movement, cryptomining, denial-of-company, and delicate details theft.
To make issues worse, this strategy does not leave a trail in a fashion that can be joined again to the genuine Gmail or Google Workspace account that obtained the OAuth bearer token.
Sys:All has been found to influence numerous corporations, leading to the publicity of many delicate information, these types of as JWT tokens, GCP API keys, AWS keys, Google OAuth credentials, personal keys, and credentials to container registries, the final of which could then be applied to trojanize container photographs.
Next liable disclosure to Google, the business has taken measures to block the binding of the technique:authenticated team to the cluster-admin function in GKE variations 1.28 and afterwards.
“To help safe your clusters towards mass malware attacks that exploit cluster-admin obtain misconfigurations, GKE clusters working edition 1.28 and later on will not likely let you to bind the cluster-admin ClusterRole to the technique:nameless user or to the technique:unauthenticated or technique:authenticated groups,” Google now notes in its documentation.

Google is also recommending end users to not bind the system:authenticated group to any RBAC roles, as effectively as evaluate irrespective of whether the clusters have been sure to the group employing each ClusterRoleBindings and RoleBindings and get rid of unsafe bindings.
Orca has also warned that although there is no general public file of a significant-scale attack using this system, it could be only a matter of time, necessitating that end users consider appropriate methods to secure their cluster obtain controls.
“Even nevertheless this is an improvement, it is important to be aware that this continue to leaves quite a few other roles and permissions that can be assigned to the group,” the corporation claimed.
Observed this posting intriguing? Stick to us on Twitter and LinkedIn to browse far more distinctive articles we publish.
Some sections of this report are sourced from:
thehackernews.com

 What is Nudge Security and How Does it Work?
What is Nudge Security and How Does it Work?