In modern hugely dispersed office, every single worker has the potential to act as their personal CIO, adopting new cloud and SaaS technologies when and anywhere they require. Whilst this has been a critical boon to productivity and innovation in the digital company, it has upended standard strategies to IT security and governance.
Nudge Security is the world’s very first and only answer to handle SaaS security and governance at scale by performing with employees—not in opposition to them. Not like legacy solutions that try to block employees’ accessibility to unsanctioned SaaS applications, Nudge Security assists IT and security leaders adapt and align to the requirements of the small business. The platform orchestrates SaaS administration devoid of sacrificing visibility, centralized governance, or control more than the organization’s cloud and SaaS security posture.
How Nudge Security functions
Nudge Security discovers all SaaS accounts ever designed by any one in your group inside minutes of commencing a cost-free trial, and only demands a single place of integration: read-only API entry to your Microsoft 365 or Google Workspace email company. No endpoint agents, network proxies, browser plugins, app integrations, or other intricate deployment techniques expected.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The patented tactic to SaaS discovery requires benefit of a dependable layout pattern: just about every SaaS service provider works by using email to drive person engagement, making it the fantastic party log to seize new account sign-ups and other security-relevant pursuits. By looking and examining equipment-produced email messages (e.g., [email protected]), Nudge Security builds and updates your stock of SaaS accounts, buyers, and resources, with no you at any time getting to inform it which applications to glance for.
 Stock of SaaS end users and apps
Stock of SaaS end users and apps
Employ SaaS security greatest tactics
Nudge Security not only displays you who has accessibility to what, but it consists of beneficial context on how entry was granted, no matter whether by means of SSO, an OAuth grant, or username and password. Nudge Security also exhibits you which applications and accounts are (and usually are not) enrolled in MFA or SSO so you can very easily monitor progress versus your enrollment initiatives and kick off automated workflows to assist buyers allow MFA for their accounts and enroll apps in SSO.
On top of that, you’ll see a full inventory of all OAuth grants and scopes to have an understanding of in which application-to-app integrations could enable details to be shared beyond what is permissible less than your information governance policy. OAuth risk scores support you quickly establish extremely permissive scopes so you can nudge app people for far more context, or revoke the grant with two clicks.
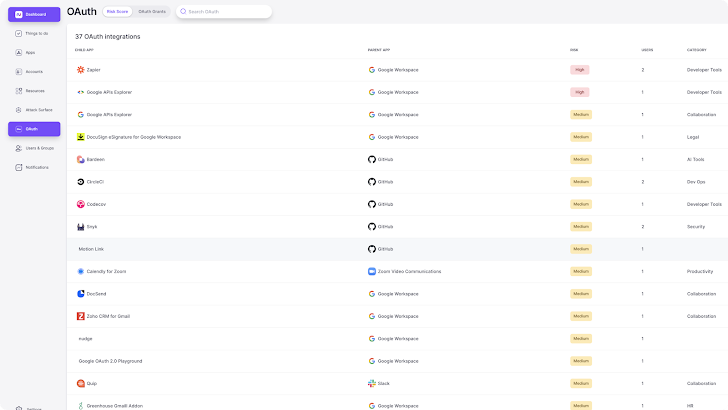 Record of OAuth grants and scopes
Record of OAuth grants and scopes
Watch your SaaS attack surface area
Your fashionable attack surface extends to each and every SaaS application, user id, and OAuth grant applied by your workforce to build your products and run your enterprise. Which is why Nudge Security discovers and screens your overall SaaS attack floor as it alterations, including SaaS apps, cloud infrastructure, developer tools, social media accounts, registered domains and additional. With Nudge Security, you can see all externally struggling with belongings an attacker could see so you can get proactive actions to shield and lessen your attack area.
Nudge Security also presents seller security profiles for every single of your SaaS providers, together with breach record, compliance attestations, information locality, and additional. With this information, you can conduct SaaS seller security assessments a lot more speedily and put together for compliance audits far more simply. And, only Nudge Security shows you the SaaS source chain of your SaaS suppliers, so when breaches of significant profile applications happen you can promptly determine if you are in the blast radius of a third- or fourth-party offer chain attack. You are going to even be alerted if a SaaS service provider you use is breached, or if a SaaS device made use of by one particular of your providers is breached.
 Breach background for your applications and all those utilised by your SaaS suppliers
Breach background for your applications and all those utilised by your SaaS suppliers
Rein in SaaS sprawl without the need of impeding productivity
Investigation displays that limiting employees’ obtain to SaaS apps in an effort and hard work to curb SaaS sprawl qualified prospects to annoyance and shadowy workarounds.
Nudge Security automates worker engagement with timely, beneficial nudges that manual customers and application proprietors toward SaaS security ideal tactics. For case in point, when a new application is found out, you can talk to the user how they will be employing it, or nudge them to use an authorized substitute. You can also nudge end users to request if they are however using a unique app so you can reclaim unused licenses. These automatic touchpoints make it easy to orchestrate SaaS security and governance at scale, driving enhanced IT efficiency.
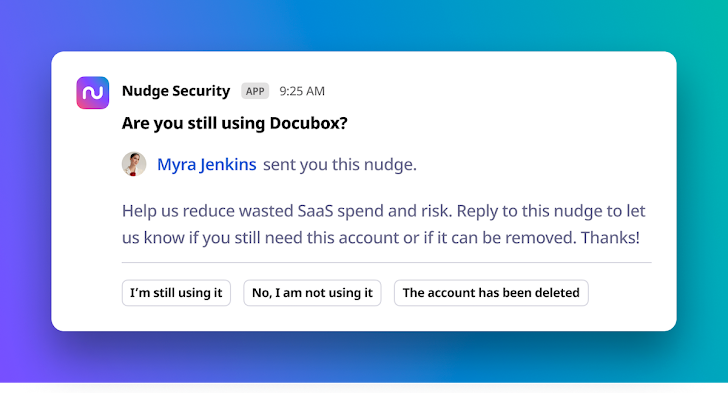 Nudges consumers to uncover out what apps they however want
Nudges consumers to uncover out what apps they however want
Automate your SaaS security efforts.
The past point you need is another security product or service that makes overhead for your team. Our created-in playbooks automate workflows for typical SaaS security jobs, like conducting person obtain reviews, bringing AWS accounts into central governance corporations, offboarding departing staff members, revoking risky OAuth grants, and extra so you can lower time used on monotonous manual responsibilities.
 Playbooks automate widespread SaaS administration tasks
Playbooks automate widespread SaaS administration tasks
Get started with Nudge Security.
To find out your organization’s SaaS footprint and modernize your solution to SaaS security and governance, begin your 14-working day free of charge demo nowadays.
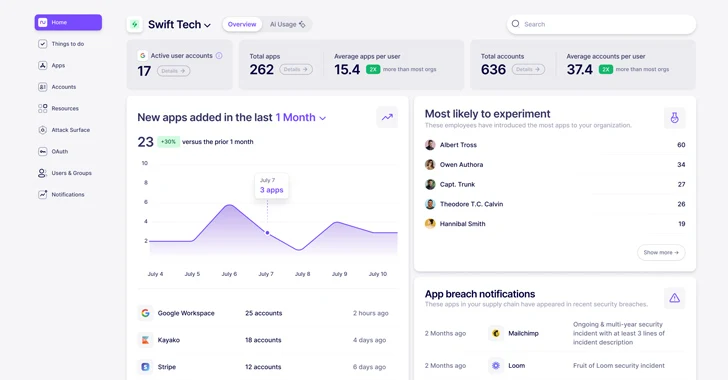
 Your SaaS administration dashboard in Nudge Security
Your SaaS administration dashboard in Nudge Security
Located this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to read through a lot more exceptional content we publish.
Some sections of this article are sourced from:
thehackernews.com

 Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption
Kasseika Ransomware Using BYOVD Trick to Disarms Security Pre-Encryption