An Internet Explorer zero-day vulnerability was actively exploited by a North Korean risk actor to goal South Korean users by capitalizing on the recent Itaewon Halloween group crush to trick end users into downloading malware.
The discovery, noted by Google Risk Examination Group scientists Benoît Sevens and Clément Lecigne, is the most recent set of attacks perpetrated by ScarCruft, which is also referred to as APT37, InkySquid, Reaper, and Ricochet Chollima.
“The group has historically concentrated their targeting on South Korean consumers, North Korean defectors, policy makers, journalists, and human rights activists,” TAG reported in a Thursday investigation.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The new findings illustrate the risk actor’s ongoing abuse of Internet Explorer flaws this sort of as CVE-2020-1380 and CVE-2021-26411 to drop backdoors like BLUELIGHT and Dolphin, the latter of which was disclosed by Slovak cybersecurity company ESET late past month.
A different critical device in its arsenal is RokRat, a Windows-based mostly remote entry trojan that will come with a extensive vary of features that allow for it to capture screenshots, log keystrokes, and even harvest Bluetooth machine info.
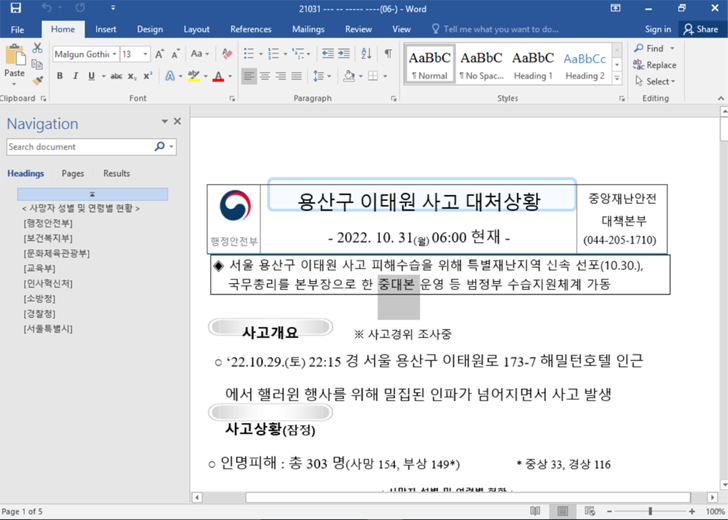
The attack chain observed by Google TAG involves the use of a destructive Microsoft Term document that was uploaded to VirusTotal on Oct 31, 2022. It abuses but a different Internet Explorer zero-working day flaw in the JScript9 JavaScript engine, CVE-2022-41128, that was patched by Microsoft last month.
The file references the Oct 29 incident that took put in the Itaewon community of Seoul and exploits community desire in the tragedy to retrieve an exploit for the vulnerability on opening it. The attack is enabled by the reality that Office renders HTML articles using Internet Explorer.
Prosperous exploitation is followed by the delivery of a shellcode that wipes all traces by clearing the Internet Explorer cache and background as nicely as downloading the future stage payload.
Google TAG explained it could not recover the stick to-on malware utilized in the marketing campaign, despite the fact that it is suspected to have concerned the deployment of RokRat, BLUELIGHT, or Dolphin.
Discovered this short article interesting? Stick to us on Twitter and LinkedIn to study far more unique material we write-up.
Some pieces of this post are sourced from:
thehackernews.com


 Iranian Hackers Strike Diamond Industry with Data-Wiping Malware in Supply-Chain Attack
Iranian Hackers Strike Diamond Industry with Data-Wiping Malware in Supply-Chain Attack