An Iranian state-of-the-art persistent danger (APT) actor identified as Agrius has been attributed as guiding a established of information wiper attacks aimed at diamond industries in South Africa, Israel, and Hong Kong.
The wiper, codenamed Fantasy by ESET, is believed to have been shipped through a source chain attack targeting an Israeli program suite developer as component of a campaign that started in February 2022.
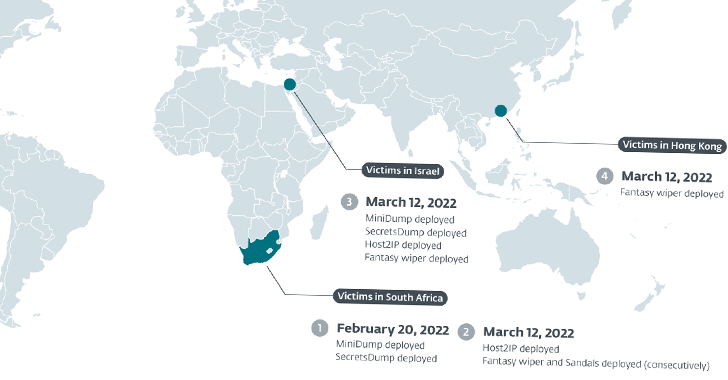
Victims include HR corporations, IT consulting organizations, and a diamond wholesaler in Israel a South African entity doing work in the diamond sector and a jeweller based mostly in Hong Kong.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The Fantasy wiper is crafted on the foundations of the previously claimed Apostle wiper but does not endeavor to masquerade as ransomware, as Apostle originally did, ESET researcher Adam Burgher disclosed in a Thursday assessment. “As a substitute, it goes ideal to perform wiping data.”
Apostle was 1st documented by SentinelOne in May well 2021 as a wiper-turned-ransomware that was deployed in harmful attacks towards Israeli targets.

Agrius, the Iran-aligned group guiding the intrusions, has been lively considering the fact that at least December 2020 and leverages regarded security flaws in internet-going through apps to drop web shells that are, in switch, applied to aid reconnaissance, lateral motion, and the supply of last-stage payloads.
The Slovak cybersecurity company said the initially attack was detected on February 20, 2022, aimed at a South African firm, when the actor deployed credential harvesting tools.
Agrius subsequently initiated the wiping attack through Fantasy on March 12, 2022, ahead of putting other firms in Israel and Hong Kong on the similar day.
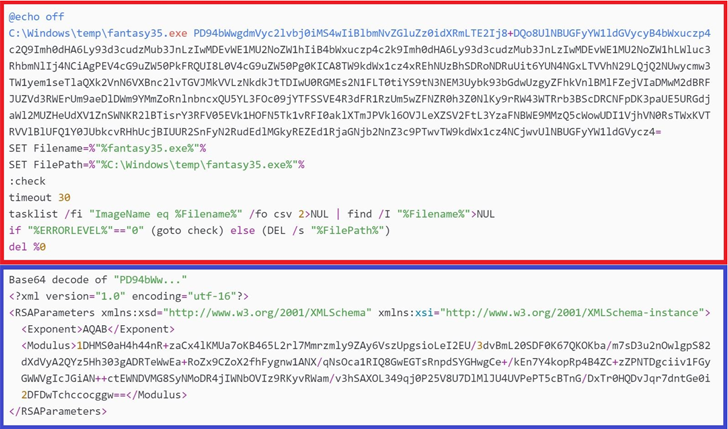
Fantasy is executed by implies of another software referred to as Sandals, a 32-bit Windows executable composed in C#/.NET. It truly is claimed to be deployed on the compromised host by a supply-chain attack utilizing the Israeli developer’s application update mechanism.
This is substantiated by ESET’s evaluation that all victims are prospects of the influenced software developer and that the wiper binary follows a naming conference (“fantasy45.exe” and “fantasy35.exe”) very similar to that of its reputable counterpart.
The wiper, for its element, operates by recursively retrieving the listing listing for every drive, overwriting every file in all those directories with garbage information, assigning a long term timestamp to the documents, and then deleting them.
“This is presumably completed to make recovery and forensic assessment far more hard,” Burgher explained.
In a further endeavor to erase all traces of the activity, Fantasy clears all Windows party logs, recursively purges all documents in the system push, overwrites the system’s Grasp Boot File, self-deletes by itself, and at last reboots the machine.
The campaign, which lasted no extra than a few several hours, was ultimately unsuccessful, with ESET stating that it was able to block the wiper’s execution. The developer of the software package has due to the fact pushed out clear updates to plug the attacks.
The identify of the Israeli business that fell victim to the provide chain attack was not disclosed by ESET, but evidence details to it remaining Rubinstein Application, which marketplaces an company source scheduling (ERP) answer termed Fantasy that is applied for jewelry stock administration.
“Because its discovery in 2021, Agrius has been solely concentrated on damaging operations,” Burgher concluded.
“To that stop, Agrius operators in all probability executed a offer-chain attack by targeting an Israeli software package firm’s computer software updating mechanisms to deploy Fantasy, its most recent wiper, to victims in Israel, Hong Kong, and South Africa.”
Agrius is much from the 1st menace group linked to Iran that has been spotted deploying harmful wiper malware.
The APT33 hacking group (aka Elfin, Holmium, or Refined Kitten), which is suspected of operating at the behest of the Iranian federal government, is claimed to have been driving several attacks that employed the Shamoon wiper versus targets positioned in the Middle East.
Information-wiping malware codenamed ZeroCleare has also been used by Iran-backed threat actors tracked as APT34 (aka Oilrig or Helix Kitten) in attacks directed from organizations from the vitality and industrial sector in the Center East.
Observed this write-up appealing? Follow us on Twitter and LinkedIn to read through much more exceptional written content we post.
Some sections of this write-up are sourced from:
thehackernews.com

 Microsoft Warns Cryptocurrency Firms Against Complex Cyber-Attacks
Microsoft Warns Cryptocurrency Firms Against Complex Cyber-Attacks