Cybersecurity researchers have uncovered a wide selection of approaches adopted by an highly developed malware downloader called GuLoader to evade security software.
“New shellcode anti-analysis system attempts to thwart researchers and hostile environments by scanning full system memory for any virtual equipment (VM)-associated strings,” CrowdStrike scientists Sarang Sonawane and Donato Onofri mentioned in a technological create-up printed final week.
GuLoader, also called CloudEyE, is a Visual Basic Script (VBS) downloader which is used to distribute remote access trojans on contaminated devices. It was initial detected in the wild in 2019.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In November 2021, a JavaScript malware strain dubbed RATDispenser emerged as a conduit for dropping GuLoader by means of a Base64-encoded VBScript dropper.

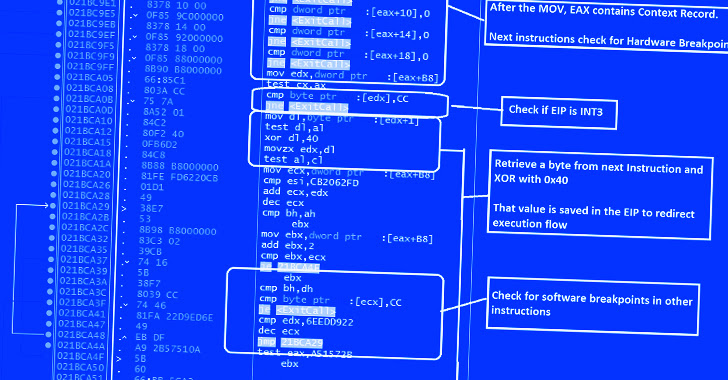
A current GuLoader sample unearthed by CrowdStrike exhibits a 3-stage course of action whereby the VBScript is intended to produce a next-stage that performs anti-investigation checks before injecting shellcode embedded within just the VBScript into memory.
The shellcode, moreover incorporating the very same anti-examination approaches, downloads a remaining payload of the attacker’s alternative from a remote server and executes it on the compromised host.
“The shellcode employs quite a few anti-analysis and anti-debugging tricks at each individual step of execution, throwing an error information if the shellcode detects any identified investigation of debugging mechanisms,” the scientists pointed out.
This involves anti-debugging and anti-disassembling checks to detect the presence of a remote debugger and breakpoints, and if observed, terminate the shellcode. The shellcode also features scans for virtualization software.
An extra ability is what the cybersecurity corporation phone calls a “redundant code injection mechanism” to stay clear of NTDLL.dll hooks applied by endpoint detection and response (EDR) answers.
NTDLL.dll API hooking is a approach applied by anti-malware engines to detect and flag suspicious procedures on Windows by checking the APIs that are known to be abused by menace actors.
In a nutshell, the approach includes utilizing assembly directions to invoke the essential windows API perform to allocate memory (i.e., NtAllocateVirtualMemory) and inject arbitrary shellcode into memory by way of procedure hollowing.
The conclusions from CrowdStrike also arrive as cybersecurity firm Cymulate shown an EDR bypass method recognized as Blindside that will allow for running arbitrary code by working with components breakpoints to generate a “approach with only the NTDLL in a stand-by yourself, unhooked condition.”
“GuLoader continues to be a dangerous threat that is been continually evolving with new methods to evade detection,” the scientists concluded.
Found this report fascinating? Abide by us on Twitter and LinkedIn to read additional exceptional articles we publish.
Some parts of this article are sourced from:
thehackernews.com

 2022 Top Five Immediate Threats in Geopolitical Context
2022 Top Five Immediate Threats in Geopolitical Context