As we are nearing the close of 2022, wanting at the most concerning threats of this turbulent yr in conditions of testing figures delivers a menace-centered standpoint on what triggers cybersecurity groups to test how vulnerable they are to specific threats. These are the threats that have been most tested to validate resilience with the Cymulate security posture administration system between January 1st and December 1st, 2022.
Manjusaka
Date published: August 2022
Reminiscent of Cobalt Strike and Sliver framework (equally commercially produced and created for pink teams but misappropriated and misused by menace actors), this rising attack framework holds the prospective to be greatly used by malicious actors. Penned in Rust and Golang with a Consumer Interface in Easy Chinese (see the workflow diagram beneath), this software is of Chinese origin.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
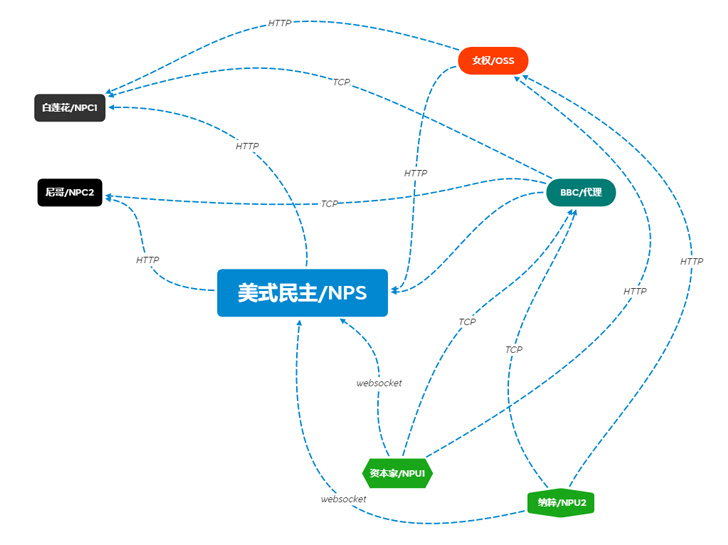
Manjasuka carries Windows and Linux implants in Rust and helps make a prepared-created C2 server freely readily available, with the chance of building custom made implants.
Geopolitical context
Manjasuka was designed for legal use from the get-go, and 2023 could be defined by greater legal utilization of it as it is freely distributed and would lower felony reliance on the misuse of commercially offered simulation and emulation frameworks these kinds of as Cobalt Strike, Sliver, Ninja, Bruce Ratel C4, and many others.
At the time of composing, there was no indicator that the creators of Manjasuka are state-sponsored but, as plainly indicated beneath, China has not been resting this calendar year.
PowerLess Backdoor
Day published: February 2022
Powerless Backdoor is the most common of this 12 months Iran-linked threats, developed to keep away from PowerShell detection. Its abilities contain downloading a browser details stealer and a keylogger, encrypting and decrypting data, executing arbitrary commands, and activating a kill procedure.
Geopolitical context
The quantity of fast threats attributed to Iran has jumped from 8 to 17, more than double of the comparable 2021 period. However, it has slowed noticeably due to the fact the September 14th U.S. Office of the Treasury’s Business office of Overseas Assets Management (OFAC) sanctions versus Iranian cyber actors, trickling down to a solitary attack imputed to Iran considering the fact that then.
The present political tensions in Iran will no doubt impression the frequency of attacks in 2023, but at this phase, it is difficult to assess regardless of whether these will increase or lower.
APT 41 focusing on U.S. Point out Governments
Day released: March 2022
Already flagged as extremely lively in 2021, APT41 is a Chinese point out-sponsored attacker team activity that showed no signal of slowing down in 2022, and investigations into APT41 action uncovered proof of a deliberate campaign targeting U.S. state governments.
APT 41 takes advantage of reconnaissance resources, these as Acunetix, Nmap, SQLmap, OneForAll, subdomain3, subDomainsBrute, and Sublist3r. It also launches a big array of attack styles, this kind of as phishing, watering gap, and source-chain attacks, and exploits numerous vulnerabilities to to begin with compromise their victims. More not too long ago, they have been seen working with the publicly offered tool SQLmap as the initial attack vector to conduct SQL injections on internet sites.
This November, a new subgroup, Earth Longhi, joined the already long checklist of monikers related with APT 41 (ARIUM, Winnti, Direct, WICKED SPIDER, WICKED PANDA, Blackfly, Suckfly, Winnti Umbrella, Double Dragon). Earth Longhi was spotted targeting multiple sectors throughout Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine.
Geopolitical context
According to Microsoft digital Protection Report 2022, “Lots of of the attacks coming from China are driven by its means to find and compile “zero-working day vulnerabilities” – exclusive unpatched holes in program not earlier recognised to the security group. China’s selection of these vulnerabilities appears to have elevated on the heels of a new law requiring entities in China to report vulnerabilities they learn to the govt just before sharing them with other people.”
LoLzarus Phishing Attack on DoD Sector
Day published: February 2022
Dubbed LolZarus, a phishing campaign attempted to entice U.S. defense sector career applicants. This marketing campaign was at first recognized by Qualys Menace Investigation, which attributed it to the North-Korean risk actor Lazarus (AKA Dark Seoul, Labyrinth Chollima, Stardust Chollima, BlueNoroff, and APT 38). Affiliated with North Korea’s Reconnaissance Common Bureau, this group is the two politically and economically enthusiastic and have been greatest known for the higher profile attack on Sondy in 2016 and WannaCry ransomware attack in 2017.
The LolZarus phishing marketing campaign relied on at minimum two destructive paperwork, Lockheed_Martin_JobOpportunities.docx and wage_Lockheed_Martin_task_prospects_confidential.doc, that abused macros with aliases to rename the API applied and relied on ActiveX Frame1_Layout to automatic the attack execution. The macro then loaded the WMVCORE.DLL Windows Media dll file to help deliver the 2nd stage shellcode payload aimed at hijacking manage and connecting with the Command & Manage server.
Geopolitical context
One more two North Korean infamous attacks flagged by CISA this year involve the use of Maui ransomware and action in cryptocurrency theft. Lazarus subgroup BlueNoroff would seem to have branched out of cryptocurrency specialization this calendar year to also target cryptocurrency-linked SWIFT servers and financial institutions. Cymulate connected 7 fast threats with Lazarus given that January 1st, 2022.
Industroyer2
Date revealed: April 2022
Ukraine’s superior-alert condition, thanks to the conflict with Russia, shown its efficacy by thwarting an attempted cyber-bodily attack targeting significant-voltage electrical substations. That attack was dubbed Industroyer2 in memory of the 2016’s Industroyer cyber-attack, seemingly concentrating on Ukraine electric power stations and minimally effective, slicing the electric power in portion of Kyiv for about a person hour.
The degree of Industroyer2 custom made concentrating on integrated statically specified executable file sets of special parameters for specific substations.
Geopolitical context
Ukraine’s cyber-resilience in protecting its critical amenities is sad to say powerless in opposition to kinetic attacks, and Russia appears to have now opted for more traditional military services indicates to demolish ability stations and other civilian amenities. In accordance to ENISA, a aspect-result of the Ukraine-Russia conflict is a recrudescence of cyber threats in opposition to governments, businesses, and critical sectors these kinds of as energy, transport, banking, and electronic infrastructure, in general.
In summary, as of the 5 most relating to threats this 12 months, four have been immediately connected with state-sponsored threat actors and the menace actors at the rear of the fifth a single are unidentified, it appears that geopolitical tensions are at the root of the most burning danger worries for cybersecurity teams.
As point out-sponsored attackers commonly have obtain to cyber assets unattainable by most companies, pre-emptive protection from complicated attacks really should focus on security validation and continuous procedures centered on pinpointing and closing in-context security gaps.
Observe: This short article was penned and contributed by David Klein, Cyber Evangelist at Cymulate.
Uncovered this report fascinating? Adhere to us on Twitter and LinkedIn to read through more exclusive content material we publish.
Some components of this write-up are sourced from:
thehackernews.com

 PrivateLoader PPI Service Found Distributing Info-Stealing RisePro Malware
PrivateLoader PPI Service Found Distributing Info-Stealing RisePro Malware