The pay out-for every-install (PPI) malware downloader assistance identified as PrivateLoader is currently being applied to distribute a beforehand documented data-stealing malware dubbed RisePro.
Flashpoint noticed the freshly recognized stealer on December 13, 2022, after it found “numerous sets of logs” exfiltrated applying the malware on an illicit cybercrime market named Russian Current market.
A C++-primarily based malware, RisePro is reported to share similarities with yet another facts-thieving malware referred to as Vidar stealer, itself a fork of a stealer codenamed Arkei that emerged in 2018.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“The appearance of the stealer as a payload for a fork out-per-put in company may possibly suggest a menace actor’s self-assurance in the stealer’s qualities,” the menace intelligence firm observed in a publish-up previous 7 days.
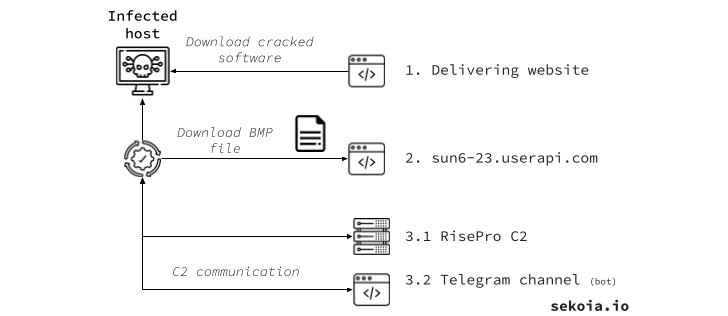
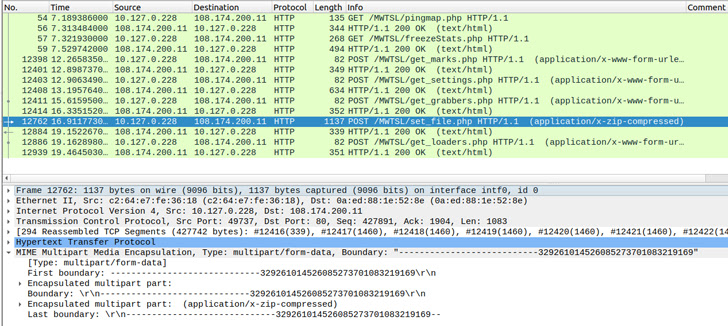
Cybersecurity agency SEKOIA, which released its own analysis of RisePro, further identified partial supply code overlaps with PrivateLoader. This encompasses the string scrambling system, HTTP method and port setup, and the HTTP information obfuscation approach.
PrivateLoader, as the name suggests, is a download provider that enables its subscribers to supply malicious payloads to focus on hosts.
It has been made use of in the past to supply Vidar Stealer, RedLine Stealer, Amadey, DanaBot, and NetDooka, between others, even though masquerading as pirated software hosted on decoy web-sites or compromised WordPress portals that surface prominently on lookup benefits.
RisePro is no distinct from other stealers in that it is really capable of stealing a broad vary of information from as numerous as 36 web browsers, like cookies, passwords, credit rating cards, crypto wallets, as effectively as accumulating information of fascination and loading a lot more payloads.
It is available for sale on Telegram, with the malware’s developer also earning accessible a Telegram channel that permits legal actors to interact with infected systems by furnishing a bot ID established by the stealer and sent to a remote server article a effective breach.
Also element of the malware’s infrastructure is an administration panel hosted at a domain named my-increase[.]cc that lets access to stolen information logs, but only just after signing into an account with a valid established of credentials.
It is really now not distinct if RisePro is authored by the exact set of threat actors behind PrivateLoader, and if it truly is exclusively bundled along with the PPI services.
“PrivateLoader is even now energetic and arrives with a set of new capabilities,” SEKOIA explained. “Similarities among the stealer and PrivateLoader are unable to be overlooked and delivers supplemental insight into the threat actor expansion.”
Observed this post intriguing? Follow us on Twitter and LinkedIn to examine extra exceptional content we post.
Some areas of this report are sourced from:
thehackernews.com

 W4SP Stealer Discovered in Multiple PyPI Packages Under Various Names
W4SP Stealer Discovered in Multiple PyPI Packages Under Various Names