Journey organizations have emerged as the focus on of a hack-for-hire group dubbed Evilnum as section of a broader campaign aimed at lawful and financial investment decision institutions in the Middle East and Europe.
The attacks targeting legislation companies all through 2020 and 2021 included a revamped variant of a malware identified as Janicab that leverages a selection of general public services like YouTube as useless fall resolvers, Kaspersky reported in a technological report printed this week.
Janicab infections comprise a assorted established of victims located in Egypt, Ga, Saudi Arabia, the UAE, and the U.K. The growth marks the to start with time lawful businesses in Saudi Arabia have been specific by this group.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Also tracked as DeathStalker, the threat actor is recognized to deploy backdoors like Janicab, Evilnum, Powersing, and PowerPepper to exfiltrate private corporate information.

“Their interest in accumulating delicate business enterprise data qualified prospects us to imagine that DeathStalker is a group of mercenaries giving hacking-for-employ products and services, or acting as some form of information and facts broker in money circles,” the Russian cybersecurity firm noted in August 2020.
According to ESET, the hacking crew has a sample of harvesting inner company presentations, program licenses, email qualifications, and paperwork that contains buyer lists, investments and buying and selling operations.
Earlier this yr, Zscaler and Proofpoint uncovered fresh attacks orchestrated by Evilnum that have been directed versus companies in the crypto and fintech verticals since late 2021.
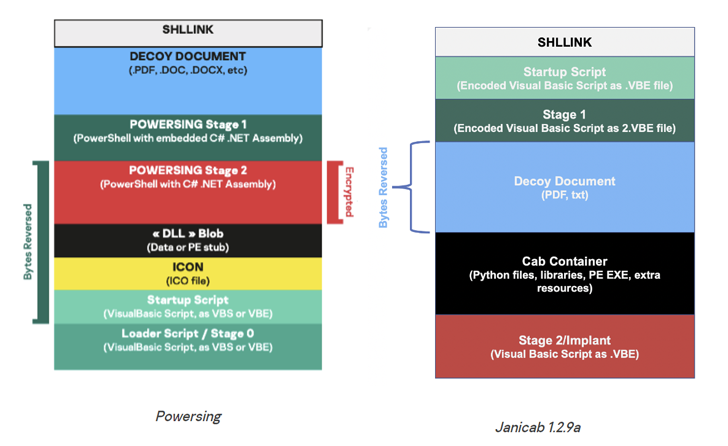
Kaspersky’s examination of the DeathStalker intrusions has discovered the use of an LNK-based dropper embedded inside a ZIP archive for preliminary entry by indicates of a spear-phishing attack.
The entice attachment purports to be a corporate profile document associated to electrical power hydraulics that, when opened, sales opportunities to the deployment of the VBScript-based mostly Janicab implant, which is capable of command execution and deploying additional equipment.
Newer variations of the modular malware have concurrently removed audio recording capabilities and added a keylogger module that shares overlaps with prior Powersing attacks. Other features contain examining for set up antivirus solutions and obtaining a checklist of processes indicating malware evaluation.
The 2021 attacks are also notable for employing unlisted old YouTube links that are utilised to host an encoded string which is deciphered by Janicab to extract the command-and-command (C2) IP tackle for retrieving follow-on commands and exfiltrating knowledge.
“Due to the fact the risk actor makes use of unlisted old YouTube links, the likelihood of acquiring the relevant hyperlinks on YouTube is practically zero,” the researchers stated. “This also efficiently allows the danger actor to reuse C2 infrastructure.”
The conclusions underscore that the danger actor has ongoing to update its malware toolset to sustain stealthiness more than prolonged periods of time.
Apart from software allowlisting and running program hardening, organizations are recommended to watch Internet Explorer processes, due to the fact the browser is utilized in hidden mode to talk with the C2 server.
As lawful and money sectors are a typical goal for the threat actor, the researchers additional theorized that DeathStalker’s clients and operators could be weaponizing the intrusions to keep tabs on lawsuits, blackmail high-profile people, track fiscal assets, and harvest business intelligence about prospective mergers and acquisitions.
Discovered this report interesting? Stick to us on Twitter and LinkedIn to browse a lot more distinctive articles we publish.
Some sections of this short article are sourced from:
thehackernews.com


 Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls