A new attack process can be utilised to circumvent web application firewalls (WAFs) of a variety of sellers and infiltrate devices, likely enabling attackers to attain obtain to delicate small business and buyer information and facts.
Web application firewalls are a essential line of defense to assist filter, observe, and block HTTP(S) visitors to and from a web application, and safeguard towards attacks this kind of as cross-internet site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The generic bypass “requires appending JSON syntax to SQL injection payloads that a WAF is unable to parse,” Claroty researcher Noam Moshe explained. “Most WAFs will simply detect SQLi attacks, but prepending JSON to SQL syntax still left the WAF blind to these attacks.”
The industrial and IoT cybersecurity business mentioned its approach correctly worked towards WAFs from sellers like Amazon Web Expert services (AWS), Cloudflare, F5, Imperva, and Palo Alto Networks, all of whom have because unveiled updates to guidance JSON syntax through SQL injection inspection.
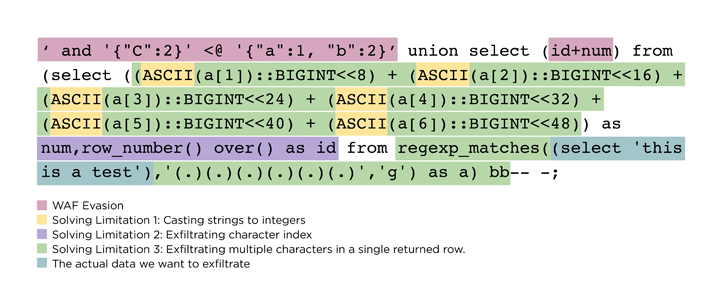
With WAFs performing as a security guardrail versus destructive external HTTP(S) targeted visitors, an attacker with capabilities to get previous the barrier can receive initial entry to a target setting for even more write-up-exploitation.
The bypass system devised by Claroty financial institutions on the deficiency of JSON help for WAFs to craft rogue SQL injection payloads that consist of JSON syntax to skirt the protections.
“Attackers applying this novel approach could access a backend database and use more vulnerabilities and exploits to exfiltrate information by way of both direct obtain to the server or above the cloud,” Moshe explained. “This is a risky bypass, specifically as much more companies continue on to migrate far more business and features to the cloud.”
Identified this write-up exciting? Observe us on Twitter and LinkedIn to read through much more unique articles we submit.
Some areas of this post are sourced from:
thehackernews.com


 Cisco Warns of High-Severity Unpatched Flaw Affecting IP Phones Firmware
Cisco Warns of High-Severity Unpatched Flaw Affecting IP Phones Firmware