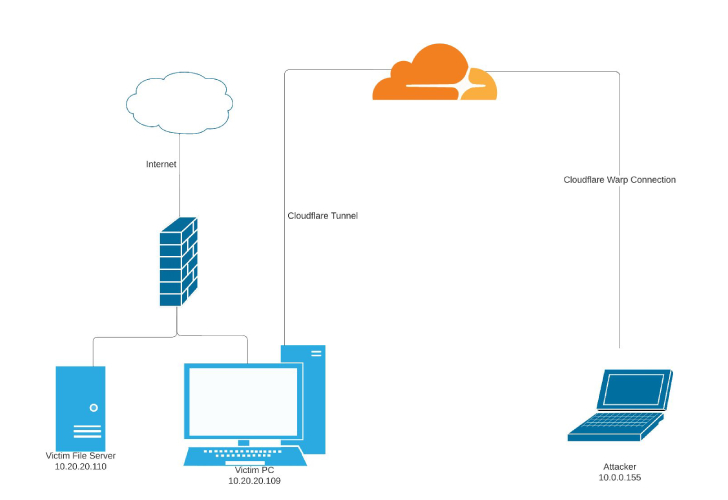
New research has discovered that danger actors are abusing Cloudflare Tunnels to build covert interaction channels from compromised hosts and keep persistent accessibility.
“Cloudflared is functionally extremely very similar to ngrok,” Nic Finn, a senior risk intelligence analyst at GuidePoint Security, explained. “Nevertheless, Cloudflared differs from ngrok in that it presents a lot more usability for free, like the ability to host TCP connectivity about cloudflared.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A command-line instrument for Cloudflare Tunnel, cloudflared lets end users to create protected connections concerning an origin web server and Cloudflare’s closest information centre so as to conceal the web server IP addresses as perfectly as block volumetric distributed denial-of-service (DDoS) and brute-drive login attacks.

For a threat actor with elevated obtain on an contaminated host, this attribute offers a rewarding strategy to established up a foothold by building a token necessary to set up the tunnel from the target device.
“The tunnel updates as before long as the configuration modify is produced in the Cloudflare Dashboard, permitting TAs to empower operation only when they want to conduct activities on the victim machine, then disable features to prevent exposure of their infrastructure,” Finn spelled out.
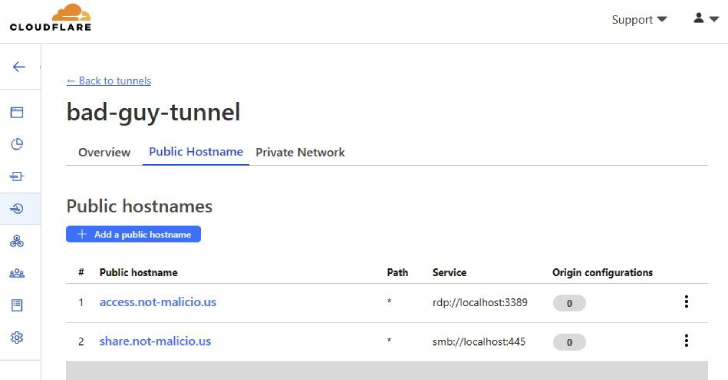
“For instance, the TA could enable RDP connectivity, collect facts from the victim machine, then disable RDP until eventually the subsequent day, therefore decreasing the opportunity of detection or the skill to notice the domain utilized to set up the link.”
Even far more troublingly, the adversary could consider benefit of the tunnel’s Personal Networks performance to stealthily entry an variety of IP addresses (i.e., endpoints within just a nearby network) as if they have been “physically collocated with the target equipment hosting the tunnel.”

That mentioned, the strategy has currently identified takers in the wild. Previously this calendar year, Phylum and Kroll in depth two various software program supply chain attacks targeting the Python Offer Index (PyPI) repository in which fraudulent deals were being noticed downloading cloudflared to remotely access the endpoint by means of a Flask web software.
“Corporations making use of Cloudflare services legitimately could likely limit their expert services to unique data facilities and generate detections for targeted traffic like Cloudflared tunnels that route to anywhere other than their specified info facilities,” Finn reported. “This process may well support in the detection of unauthorized tunnels.”
To recognize feasible misuse of cloudflared, it can be advisable that organizations implement suitable logging mechanisms to check for anomalous instructions, DNS queries, and outbound connections, alongside blocking makes an attempt to down load the executable.
Discovered this short article fascinating? Abide by us on Twitter and LinkedIn to browse a lot more exclusive articles we write-up.
Some areas of this write-up are sourced from:
thehackernews.com

 Understanding Active Directory Attack Paths to Improve Security
Understanding Active Directory Attack Paths to Improve Security