Released in 1999, Microsoft Energetic Listing is the default identity and obtain management services in Windows networks, responsible for assigning and enforcing security guidelines for all network endpoints. With it, end users can access many methods throughout networks. As items are inclined to do, times, they are a’changin’ – and a number of a long time again, Microsoft launched Azure Energetic Listing, the cloud-based mostly model of Advert to prolong the Advert paradigm, delivering companies with an Id-as-a-Support (IDaaS) answer across the two the cloud and on-prem apps. (Take note that as of July 11th 2023, this support was renamed to Microsoft Entra ID, but for the sake of simplicity, we will refer to it as Azure Advert in this article)
Each Energetic Directory and Azure Advertisement are critical to the functioning of on-prem, cloud-based, and hybrid ecosystems, participating in a vital purpose in uptime and business enterprise continuity. And with 90% of companies making use of the company for employee authentication, accessibility command and ID management, it has turn out to be the keys to the proverbial castle.
Lively Listing, Actively Problematic
But as central as it is, Active Directory security posture is typically woefully lacking.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Let’s acquire a swift peek at how Lively Directory assigns customers, which will drop some light on why this resource has some shall we say, issues, linked with it.
At the main, what Active Directory does is establish teams that have roles and authorizations linked with them. End users are assigned a username and password, which is then connected to their Active Listing Account Item. Utilizing Lightweight Directory Accessibility Protocol, passwords are verified as accurate or incorrect and the usergroup is also verified. In common, end users are assigned to the Area User group and will be granted obtain to the objects that domain people have authorization to entry. Then there are Admins – these are end users assigned to the Area Admins group. This group is remarkably privileged and is as a result approved to perform any steps in the network.
With these likely potent capabilities, it’s super critical to be certain that Active Directory is managed and configured optimally. Issues like skipped patches, weak access administration and misconfigurations can allow for attackers to accessibility even the most delicate systems, which can have dire implications.
In 2022, our in-house research located that 73% of the prime attack procedures used in the compromising of critical property involved mismanaged or stolen qualifications – and far more than fifty percent of the attacks in companies involve some ingredient of Active Listing compromise. And after they have a foothold in Energetic Directory, attackers can conduct hundreds of distinctive malicious steps like:
- Hiding activity in the network
- Executing destructive code
- Elevating privileges
- Obtaining into the cloud atmosphere to compromise critical belongings
Stage is, if you do not know what is actually taking place in your Energetic Listing, and if you’re lacking the correct procedures and security controls, you happen to be probable leaving the door large open up to attackers.
.ebook-particulars padding: 20px .ebook-picture img border-radius: 5px .xm_container screen: flex align-objects: centre margin: 20px 10px 30px background: #f9fbff color: #160755 padding: 20px border: 2px strong #d9deff border-radius: 10px text-align: still left box-shadow: 5px 5px #e2ebff -webkit-border-top rated-remaining-radius: 15px -moz-border-radius-topleft: 15px -webkit-border-bottom-suitable-radius: 15px -moz-border-radius-bottomright: 15px .ebook-graphic flex: 250pxmargin-ideal: 20px .book-particulars flex: 1 .book-details ul margin: 15px .book-aspects ul li margin-base: 5px @media (max-width: 600px) .xm_container flex-way: column .e book-image margin-correct: margin-base: 20px

Obtain our most up-to-date exploration report, and discover
- How lots of ways it requires for attackers to normally compromise your critical belongings
- Best exposures and hygiene issues that type attack paths
- Vital results connected to attacks across hybrid, on-prem or multi-cloud networks.
Lively Directory Attack Paths
From an attacker’s POV, Lively Directory serves as a terrific possibility for conducting lateral motion, as getting that first access makes it possible for them to move from a low-privileged user to a a lot more worthwhile goal – or even to fully just take above – by exploiting misconfigurations or extremely excessive permissions.
So now let us get a glance into the anatomy of 3 genuine Active Directory attack paths and see how attackers manufactured their way via this natural environment.
Here is an attack route we came throughout in just one of our customer’s atmosphere:
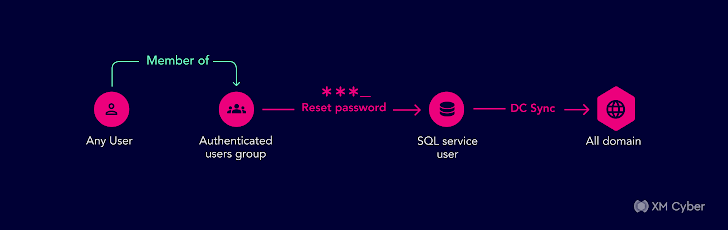
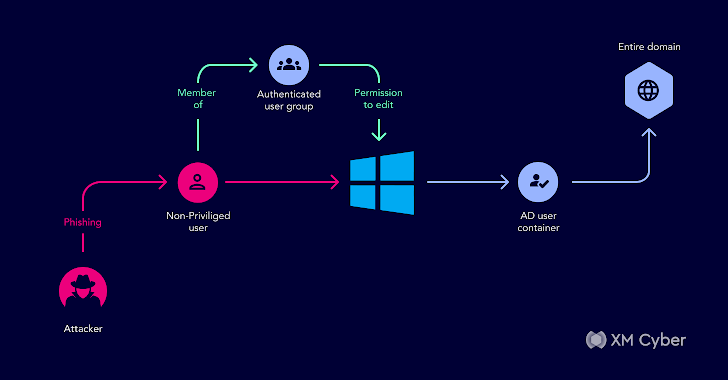
The group was deeply fully commited to hardening their security posture but Active Directory was a blind location. In this circumstance, all authenticated customers – effectively any buyers at all – in the domain had been unintentionally granted the right to reset passwords. So if an attacker took more than just one Energetic Directory person by means of phishing or other social engineering tactics, they could then reset any passwords for other consumers and just take more than any account in the domain.At the time they noticed this, they lastly recognized their Lively Directory security solution essential to amount-up so they locked down and hardened their security tactics.
This is a further a single from one of our customer’s Lively Directory
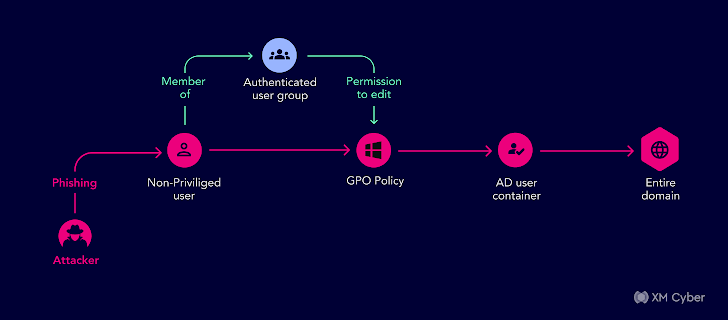
We uncovered an attack path using the authenticated users group with permissions to adjust the GPO policy’s gPCFileSysPath to a route with destructive guidelines.
One of the impacted objects was the Advert Consumer Container, with a boy or girl item that was a person which was element of the Domain Admin team. Any consumer in the area could get Domain Admin permissions — all they required was a person non-privileged person to drop prey to a phishing email to compromise the full domain. This could have led to a entire compromise of their domain.
All set for one additional? Listed here it is:
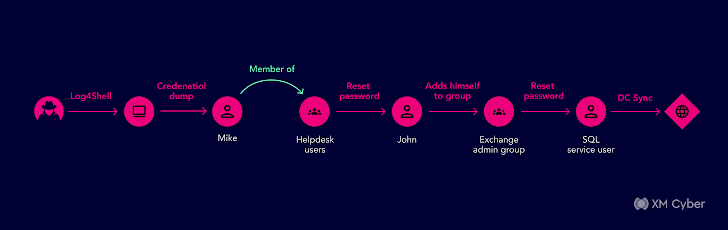
This a single starts off with an attacker infiltrating an business surroundings by using phishing mail that when opened, executed code employing a vulnerability on an unpatched equipment. The next phase exploited the compromised Active Listing user’s community and domain credentials by way of credential dumping techniques. The attacker then experienced the permissions to increase by themselves to a group so they could incorporate the compromised Active Listing consumer to an Energetic Listing helpdesk group.
The helpdesk team had the Energetic Directory permissions to reset other consumers passwords and at this phase, the attacker could reset a password to yet another consumer, preferably an old, out of use admin. Now that they were an admin, they could execute plenty of hazardous things to do in the network, these as jogging destructive code by including a script logon to other users in Energetic Directory.
These are just some relatively uncomplicated techniques attackers make their way throughout Energetic Listing environments. By comprehending these true authentic-entire world attack paths, companies can begin to see what their Active Listing and Advert Azure environments search like from the attacker’s level of view.

Watch on-need How To Prevail over Active Directory Exploits And Avert Attacks to find out:
- How Lively Listing (Advert) exposures merged with other attack tactics form attack paths
- What sort of actions the attacker can complete after they compromise an Ad consumer
- What to do for improved Active Listing Security
Conclusion
Searching at attack paths can support shore up these perhaps challenging environments. By getting a thorough see of the attack paths that exist in Lively Listing across on-prem and cloud environments, organizations can learn how attackers go laterally with a context-dependent understanding of their surroundings – providing them visibility into how issues can merge to aid attacks and impersonate people, escalate privileges, and get obtain to cloud environments.
With this understanding, businesses can prioritize what definitely requirements fixing and harden environments to prevent Active Listing weaknesses from staying leveraged by risk actors.
Found this short article intriguing? Comply with us on Twitter and LinkedIn to study much more unique information we post.
Some components of this posting are sourced from:
thehackernews.com

 New Yashma Ransomware Variant Targets Multiple English-Speaking Countries
New Yashma Ransomware Variant Targets Multiple English-Speaking Countries