An mysterious danger actor is working with a variant of the Yashma ransomware to target many entities in English-talking nations around the world, Bulgaria, China, and Vietnam at minimum considering the fact that June 4, 2023.
Cisco Talos, in a new generate-up, attributed the procedure with reasonable self confidence to an adversary of most likely Vietnamese origin.
“The danger actor works by using an uncommon technique to supply the ransom observe,” security researcher Chetan Raghuprasad claimed. “In its place of embedding the ransom be aware strings in the binary, they down load the ransom be aware from the actor-managed GitHub repository by executing an embedded batch file.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Yashma, 1st described by the BlackBerry exploration and intelligence group in May possibly 2022, is a rebranded edition of a different ransomware strain named Chaos. A thirty day period prior to its emergence, the Chaos ransomware builder was leaked in the wild.
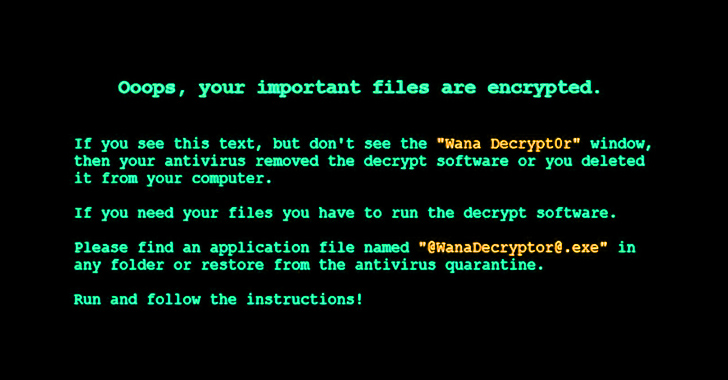
A noteworthy factor of the ransom notice is its resemblance to the properly-regarded WannaCry ransomware, possibly completed so in an attempt to obscure the risk actor’s id and confuse attribution efforts. Although the observe mentions a wallet handle to which the payment is to be built, it would not specify the amount of money.

The disclosure arrives as the cybersecurity company stated that leaks of ransomware resource code and builders are foremost to the acceleration of new ransomware variants, thus resulting in a lot more attacks.
“Ransomware builders typically have a user interface that makes it possible for users to pick the fundamental options and personalize the configurations to establish a new ransomware binary executable without the need of exposing the supply code or needing a compiler installed,” the organization pointed out.
“The availability of these kinds of builders enables newbie actors to produce their very own custom made ransomware variants.”
The improvement also follows a big spike in ransomware attacks, with Malwarebytes recording as a lot of as 1,900 incidents more than the past yr within the U.S., Germany, France, and the U.K., mainly fueled by the “ascension of the Cl0p team – which has properly harnessed zero-working day vulnerabilities to amplify its attacks.”
In a similar report, Akamai found that an improve in the use of zero-day and one particular-day security flaws has resulted in a 143% improve in the variety of ransomware victims in the initially quarter of 2023 in contrast with the very same period past year.

“The Cl0p ransomware group is aggressively creating zero-working day vulnerabilities, rising its victims by 9x yr over calendar year,” the enterprise stated. “Victims of many ransomware attacks were extra than 6x additional probably to working experience the second attack within just 3 months of the first attack.”
But in what is a even further signal of the evolution of the threat landscape, Craze Micro disclosed specifics of a TargetCompany (aka Mallox or Xollam) ransomware attack that utilized an iteration of a fully undetectable (FUD) obfuscator motor identified as BatCloak to infect susceptible techniques with remote obtain trojans like Remcos RAT and preserve a stealthy presence on focused networks.
“Afterward, the Remcos RAT will resume its last regimen as it downloads and deploys the TargetCompany ransomware nonetheless wrapped in an FUD packer,” the business reported.
“The use of FUD malware currently limitations most accessible methods for this reported tactic, even a lot more so for off-the-shelf technologies possible susceptible to other attacks (not just ransomware). This set of packers will possible not be the only kinds being formulated in the around long run.”
Found this post attention-grabbing? Follow us on Twitter and LinkedIn to study more unique information we article.
Some elements of this report are sourced from:
thehackernews.com

 LOLBAS in the Wild: 11 Living-Off-The-Land Binaries Used for Malicious Purposes
LOLBAS in the Wild: 11 Living-Off-The-Land Binaries Used for Malicious Purposes