Cybersecurity scientists have uncovered a set of 11 dwelling-off-the-land binaries-and-scripts (LOLBAS) that could be maliciously abused by danger actors to carry out put up-exploitation activities.
“LOLBAS is an attack technique that utilizes binaries and scripts that are now section of the method for destructive reasons,” Pentera security researcher Nir Chako claimed. “This would make it challenging for security groups to distinguish concerning reputable and malicious routines, considering that they are all carried out by reliable technique utilities.”
To that end, the Israeli cybersecurity organization mentioned it uncovered 9 LOLBAS downloaders and three executors that could empower adversaries to down load and execute “additional robust malware” on infected hosts.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This features: MsoHtmEd.exe, Mspub.exe, ProtocolHandler.exe, ConfigSecurityPolicy.exe, InstallUtil.exe, Mshta.exe, Presentationhost.exe, Outlook.exe, MSAccess.exe, scp.exe, and sftp.exe.

“In a entire attack chain, a hacker will use a LOLBAS downloader to down load extra sturdy malware,” Chako claimed. “Then, they will try to execute it in a stealthy way. LOLBAS executors make it possible for attackers to execute their destructive applications as aspect of a genuine wanting method tree on the method.”
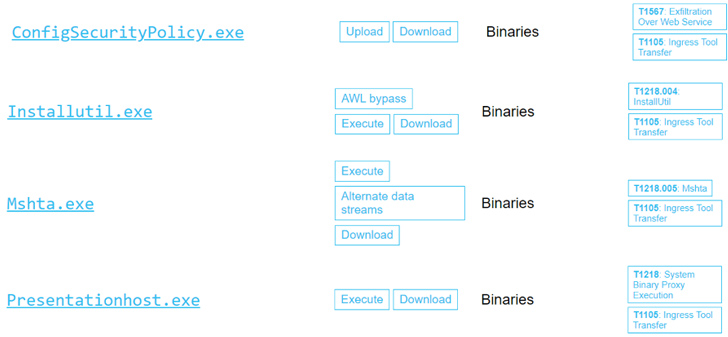
That explained, Pentera famous that attackers could also use other executables from software outdoors of all those linked to Microsoft to reach comparable aims.
The findings come as Vectra disclosed a probable new attack vector that leverages Microsoft Entra ID (formerly Azure Active Directory) cross-tenant synchronization (CTS) aspect to facilitate lateral motion to other tenants assuming a privileged identification has currently been compromised in the cloud natural environment.
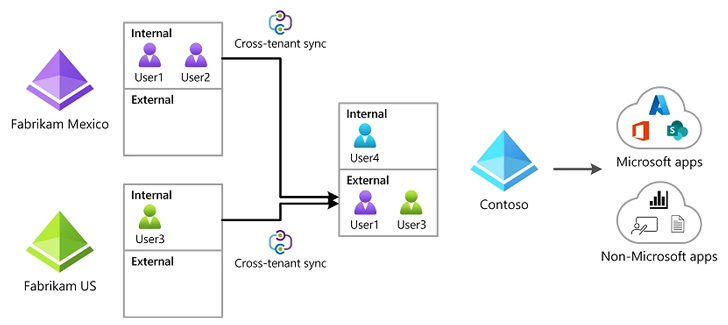
“An attacker working in a compromised natural environment can exploit an present CTS configuration tenant to go laterally from one tenant to a further related tenant,” the company stated. Alternatively, “an attacker operating in a compromised tenant can deploy a rogue Cross Tenant Accessibility configuration to preserve persistent entry.”
Found this post appealing? Observe us on Twitter and LinkedIn to read through additional exclusive content material we article.
Some sections of this posting are sourced from:
thehackernews.com


 New Malware Campaign Targets Inexperienced Cyber Criminals with OpenBullet Configs
New Malware Campaign Targets Inexperienced Cyber Criminals with OpenBullet Configs