A established of novel attack approaches has been shown in opposition to Google Workspace and the Google Cloud System that could be possibly leveraged by threat actors to conduct ransomware, details exfiltration, and password recovery attacks.
“Starting from a one compromised machine, risk actors could development in numerous means: they could go to other cloned machines with GCPW set up, acquire access to the cloud platform with personalized permissions, or decrypt regionally saved passwords to continue their attack further than the Google ecosystem,” Martin Zugec, technical alternatives director at Bitdefender, claimed in a new report.
A prerequisite for these attacks is that the bad actor has currently received entry to a area equipment through other implies, prompting Google to mark the bug as not qualified for fixing “considering that it’s outside of our risk model and the behavior is in line with Chrome’s methods of storing regional knowledge.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Nevertheless, the Romanian cybersecurity firm has warned that threat actors can exploit these kinds of gaps to increase a solitary endpoint compromise to a network-large breach.
The attacks, in a nutshell, rely on an organization’s use of Google Credential Supplier for Windows (GCPW), which presents each cellular gadget administration (MDM) and one indication-on (SSO) abilities.
This allows directors to remotely manage and regulate Windows units inside their Google Workspace environments, as well as enables consumers to obtain their Windows units applying the identical credentials that are utilized to login to their Google accounts.
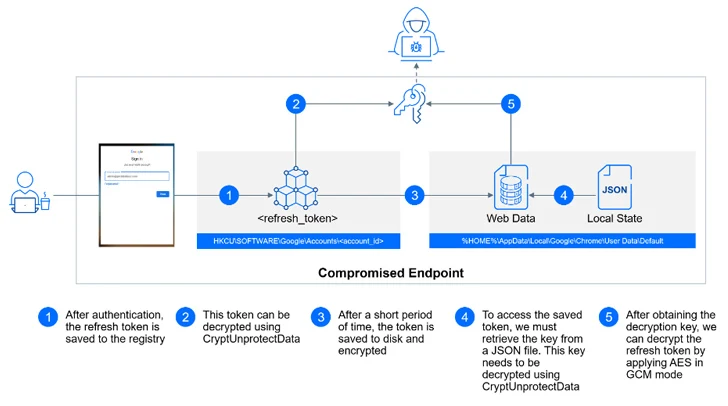
GCPW is made to use a regional privileged service account named Google Accounts and ID Administration (GAIA) to seamlessly facilitate the process in the background by connecting to Google APIs for verifying a user’s credentials through the indication-in move and storing a refresh token to obviate the will need for re-authentication.
With this setup in location, an attacker with entry to a compromised device can extract an account’s refresh OAuth tokens, either from the Windows registry or from the user’s Chrome profile listing, and bypass multi-factor authentication (MFA) protections.
The refresh token is subsequently used to assemble an HTTP Put up ask for to the endpoint “https://www.googleapis[.]com/oauth2/v4/token” to receive an obtain token, which, in flip, can be abused to retrieve, manipulate, or delete delicate facts connected with the Google Account.

A next exploit worries what is known as the Golden Picture lateral motion, which focuses on virtual machine (VM) deployments and requires gain of the point that making a device by cloning another machine with pre-set up GCPW causes the password associated with the GAIA account to be cloned as nicely.
“If you know the password to a area account, and neighborhood accounts on all machines share the similar password, then you know the passwords to all devices,” Zugec spelled out.
“This shared-password challenge is related to obtaining the similar local administrator password on all devices that has been resolved by Microsoft’s Local Administrator Password Solution (LAPS).”
The third attack entails obtain to plaintext qualifications by leveraging the accessibility token acquired using the aforementioned strategy to send out an HTTP GET ask for to an undocumented API endpoint and get keep of the non-public RSA essential that is needed to decrypt the password industry.
“Having access to plaintext credentials, these types of as usernames and passwords, signifies a much more significant threat,” Zugec reported. “This is simply because it enables attackers to straight impersonate reputable consumers and gain unrestricted accessibility to their accounts, most likely top to comprehensive account takeover.”
Uncovered this article appealing? Follow us on Twitter and LinkedIn to go through additional exclusive content we submit.
Some pieces of this report are sourced from:
thehackernews.com


 Russian Hackers Launch ‘Largest Ever Cyber Attack’ on Danish Critical Infrastructure
Russian Hackers Launch ‘Largest Ever Cyber Attack’ on Danish Critical Infrastructure