Threat actors are focusing on misconfigured and vulnerable servers jogging Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis products and services as portion of an rising malware campaign developed to supply a cryptocurrency miner and spawn a reverse shell for persistent distant accessibility.
“The attackers leverage these equipment to issue exploit code, getting edge of popular misconfigurations and exploiting an N-day vulnerability, to conduct Remote Code Execution (RCE) attacks and infect new hosts,” Cado security researcher Matt Muir reported in a report shared with The Hacker News.
The exercise has been codenamed Spinning YARN by the cloud security firm, with overlaps to cloud attacks attributed to TeamTNT, WatchDog, and a cluster dubbed Kiss-a-doggy.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
It all starts off with deploying four novel Golang payloads that are able of automating the identification and exploitation of susceptible Confluence, Docker, Hadoop YARN, and Redis hosts. The spreader utilities leverage masscan or pnscan to hunt for these expert services.

“For the Docker compromise, the attackers spawn a container and escape from it onto the fundamental host,” Muir stated.
The preliminary accessibility then paves the way for the deployment of supplemental applications to install rootkits like libprocesshider and diamorphine to conceal destructive procedures, fall the Platypus open-supply reverse shell utility, and in the end start the XMRig miner.
“It truly is obvious that attackers are investing important time into understanding the sorts of web-going through companies deployed in cloud environments, retaining abreast of described vulnerabilities in people services and making use of this knowledge to obtain a foothold in target environments,” the corporation stated.
The enhancement arrives as Uptycs exposed 8220 Gang’s exploitation of regarded security flaws in Apache Log4j (CVE-2021-44228) and Atlassian Confluence Server and Information Center (CVE-2022-26134) as portion of a wave of assaults targeting cloud infrastructure from May possibly 2023 via February 2024.
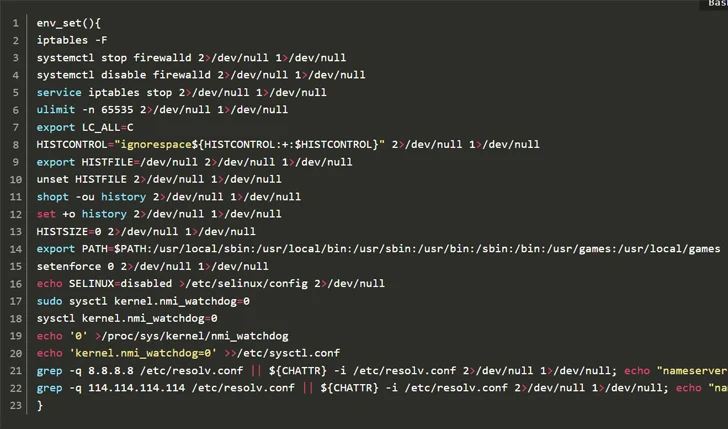
“By leveraging internet scans for vulnerable apps, the group identifies opportunity entry details into cloud techniques, exploiting unpatched vulnerabilities to gain unauthorized entry,” security researchers Tejaswini Sandapolla and Shilpesh Trivedi said.
“After within, they deploy a collection of highly developed evasion methods, demonstrating a profound knowing of how to navigate and manipulate cloud environments to their gain. This involves disabling security enforcement, modifying firewall guidelines, and getting rid of cloud security products and services, thus guaranteeing their destructive functions keep on being undetected.”
The attacks, which one out the two Windows and Linux hosts, purpose to deploy a cryptocurrency miner, but not ahead of taking a series of ways that prioritize stealth and evasion.

It also follows the abuse of cloud products and services principally meant for synthetic intelligence (AI) answers to drop cryptocurrency miners as perfectly as host malware.
“With equally mining and AI requiring accessibility to large amounts of GPU processing energy, you can find a specific diploma of transferability to their base components environments,” HiddenLayer observed very last 12 months.
Cado, in its H2 2023 Cloud Risk Findings Report, noted that danger actors are ever more focusing on cloud solutions that call for professional complex information to exploit, and that cryptojacking is no more time the only motive.
“With the discovery of new Linux variants of ransomware families, these as Abyss Locker, there is a worrying pattern of ransomware on Linux and ESXi techniques,” it mentioned. “Cloud and Linux infrastructure is now subject to a broader wide variety of attacks.”
Found this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to read a lot more unique material we article.
Some areas of this article are sourced from:
thehackernews.com


 Exit Scam: BlackCat Ransomware Group Vanishes After $22 Million Payout
Exit Scam: BlackCat Ransomware Group Vanishes After $22 Million Payout