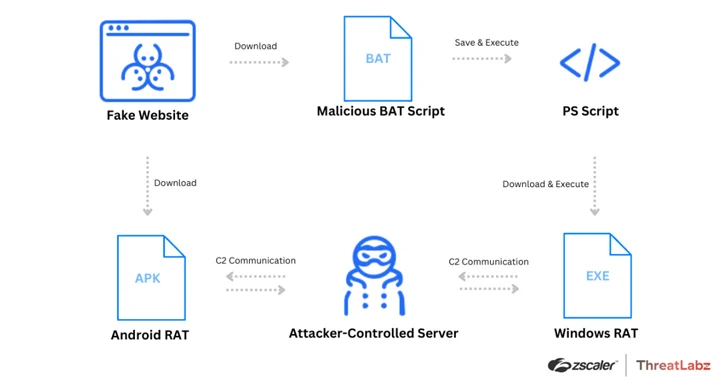
Menace actors have been leveraging bogus internet websites promotion common online video conferencing software these types of as Google Meet up with, Skype, and Zoom to provide a wide variety of malware focusing on both of those Android and Windows people because December 2023.
“The risk actor is distributing Distant Accessibility Trojans (RATs) together with SpyNote RAT for Android platforms, and NjRAT and DCRat for Windows methods,” Zscaler ThreatLabz researchers explained.
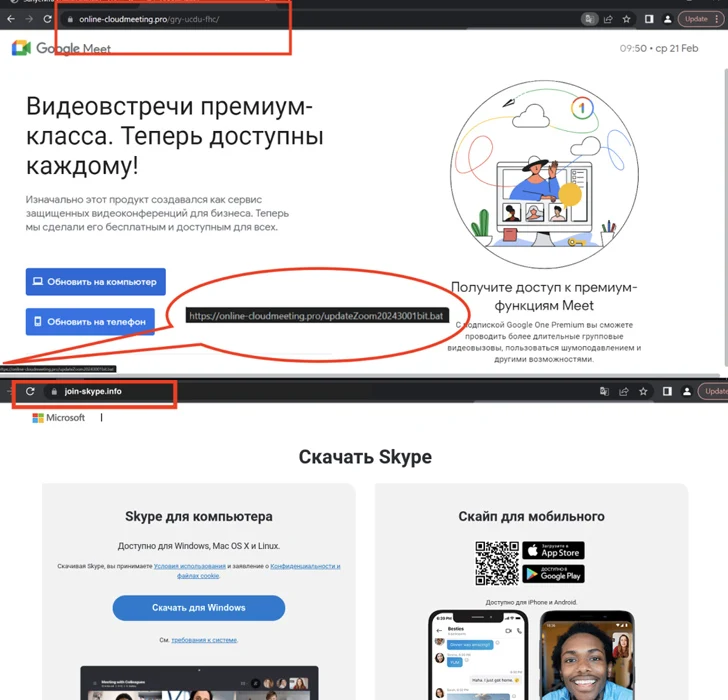
The spoofed internet sites are in Russian and are hosted on domains that carefully resemble their genuine counterparts, indicating that the attackers are using typosquatting methods to entice possible victims into downloading the malware.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

They also arrive with alternatives to obtain the app for Android, iOS, and Windows platforms. Although clicking on the button for Android downloads an APK file, clicking on the Windows app button triggers the download of a batch script.
The malicious batch script is responsible for executing a PowerShell script, which, in switch, downloads and executes the distant obtain trojan.
At present, there is no evidence that the danger actor is concentrating on iOS users, specified that clicking on the button for the iOS application can take the person to the respectable Apple Application Store listing for Skype.
“A risk actor is employing these lures to distribute RATs for Android and Windows, which can steal private details, log keystrokes, and steal data files,” the researchers reported.
The progress will come as the AhnLab Security Intelligence Centre (ASEC) revealed that a new malware dubbed WogRAT focusing on the two Windows and Linux is abusing a no cost on the web notepad platform named aNotepad as a covert vector for hosting and retrieving destructive code.
It’s reported to be active from at the very least late 2022, targeting Asian nations around the world like China, Hong Kong, Japan, and Singapore, between other people. That explained, it can be at present not regarded how the malware is dispersed in the wild.
“When WogRAT is run for the initial time, it collects standard data of the contaminated system and sends them to the C&C server,” ASEC explained. “The malware then supports commands these as executing instructions, sending success, downloading information, and uploading these documents.”
It also coincides with significant-volume phishing strategies orchestrated by a economically enthusiastic cybercriminal actor recognised as TA4903 to steal company qualifications and very likely adhere to them with business email compromise (BEC) attacks. The adversary has been active because at minimum 2019, with the pursuits intensifying write-up mid-2023.
“TA4903 routinely conducts campaigns spoofing numerous U.S. governing administration entities to steal company qualifications,” Proofpoint stated. “The actor also spoofs organizations in a variety of sectors together with construction, finance, health care, food items and beverage, and other individuals.”

Attack chains entail the use of QR codes (aka quishing) for credential phishing as well as relying on the EvilProxy adversary-in-the-center (AiTM) phishing kit to bypass two-factor authentication (2FA) protections.
After a goal mailbox is compromised, the risk actor has been noticed exploring for information and facts suitable to payments, invoices, and financial institution data, with the supreme goal of hijacking current email threads and performing bill fraud.
Phishing campaigns have also functioned as a conduit for other malware family members like DarkGate, Agent Tesla, and Remcos RAT, the final of which leverages steganographic decoys to fall the malware on compromised hosts.
Found this posting exciting? Stick to us on Twitter and LinkedIn to go through much more unique material we article.
Some parts of this post are sourced from:
thehackernews.com

 Hackers Exploit Misconfigured YARN, Docker, Confluence, Redis Servers for Crypto Mining
Hackers Exploit Misconfigured YARN, Docker, Confluence, Redis Servers for Crypto Mining