Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to obtain unauthorized obtain to Kubernetes workloads and leverage them for cryptocurrency mining action.
That is in accordance to the Microsoft Danger Intelligence crew, which explained the flaws have been weaponized due to the fact the start out of April 2024.
OpenMetadata is an open up-supply platform that operates as a metadata administration device, featuring a unified remedy for facts asset discovery, observability, and governance.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The flaws in question – all uncovered and credited to security researcher Alvaro Muñoz – are detailed below –
- CVE-2024-28847 (CVSS rating: 8.8) – A Spring Expression Language (SpEL) injection vulnerability in Put /api/v1/gatherings/subscriptions (mounted in version 1.2.4)
- CVE-2024-28848 (CVSS rating: 8.8) – A SpEL injection vulnerability in GET /api/v1/insurance policies/validation/problem/
(fixed in model 1.2.4) - CVE-2024-28253 (CVSS score: 8.8) – A SpEL injection vulnerability in Place /api/v1/insurance policies (fixed in variation 1.3.1)
- CVE-2024-28254 (CVSS rating: 8.8) – A SpEL injection vulnerability in GET /api/v1/gatherings/subscriptions/validation/affliction/
(mounted in variation 1.2.4) - CVE-2024-28255 (CVSS rating: 9.8) – An authentication bypass vulnerability (set in variation 1.2.4)
Successful exploitation of the vulnerabilities could let a menace actor to bypass authentication and obtain distant code execution.

The modus operandi uncovered by Microsoft involves the targeting of internet-exposed OpenMetadata workloads that have been remaining unpatched to gain code execution on the container managing the OpenMetadata impression.
Upon gaining an first foothold, the danger actors have been observed carrying out reconnaissance actions to establish their degree of obtain to the compromised natural environment and acquire facts about the network and components configuration, running system edition, the quantity of energetic end users, and the ecosystem variables.
“This reconnaissance action usually entails making contact with a publicly available service,” security researchers Hagai Ran Kestenberg and Yossi Weizman mentioned.
“In this specific attack, the attackers mail ping requests to domains that conclude with oast[.]me and oast[.]pro, which are involved with Interactsh, an open up-resource software for detecting out-of-band interactions.”
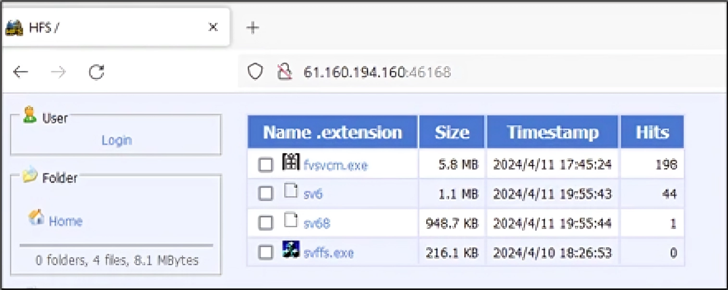
In doing so, the idea is to validate network connectivity from the infiltrated process to attacker-controlled infrastructure without increasing any red flags, thereby supplying menace actors the confidence to set up command-and-command (C2) communications and deploy additional payloads.
The end purpose of the attacks is to retrieve and deploy a Windows or Linux variant of the crypto-mining malware from a distant server located in China, relying on the operating method.
When the miner is released, the preliminary payloads are taken off from the workload, and the attackers initiate a reverse shell for their remote server employing the Netcat device, allowing them to commandeer the program. Persistence is obtained by location cron jobs to operate the malicious code at predefined intervals.
Interestingly, the risk actor also leaves guiding a private notice telling that they are very poor and that they need the dollars to get a vehicle and a suite. “I do not want to do something unlawful,” the notice reads.
OpenMetadata end users are suggested to change to solid authentication procedures, stay away from utilizing default qualifications, and update their pictures to the most up-to-date variation.
“This attack serves as a valuable reminder of why it is essential to keep compliant and operate totally patched workloads in containerized environments,” the scientists stated.
The growth comes as publicly obtainable Redis servers that have the authentication function disabled or have unpatched flaws are getting qualified to put in Metasploit Meterpreter payloads for post-exploitation.

“When Metasploit is mounted, the threat actor can choose management of the contaminated technique and also dominate the internal network of an group applying the a variety of functions made available by the malware,” the AhnLab Security Intelligence Heart (ASEC) stated.
It also follows a report from WithSecure that thorough how look for permissions on Docker directories could be abused to achieve privilege escalation. It truly is worth pointing out that the issue (CVE-2021-41091, CVSS rating: 6.3) was previously flagged by CyberArk in February 2022, and dealt with by Docker in version 20.10.9.
“The placing of the searchable little bit for other end users on /var/lib/docker/ and boy or girl directories can allow for a lower-privileged attacker to get entry to different containers’ filesystems,” WithSecure claimed.
Found this post exciting? Abide by us on Twitter and LinkedIn to examine additional special information we publish.
Some elements of this short article are sourced from:
thehackernews.com


 Malicious Google Ads Pushing Fake IP Scanner Software with Hidden Backdoor
Malicious Google Ads Pushing Fake IP Scanner Software with Hidden Backdoor