Fraudulent domains masquerading as Microsoft’s Windows 11 download portal are making an attempt to trick users into deploying trojanized set up information to infect programs with the Vidar info stealer malware.
“The spoofed web pages ended up established to distribute destructive ISO documents which lead to a Vidar details-stealer infection on the endpoint,” Zscaler stated in a report. “These variants of Vidar malware fetch the C2 configuration from attacker-managed social media channels hosted on Telegram and Mastodon network.”
Some of the rogue distribution vector domains, which were being registered previous thirty day period on April 20, consist of ms-gain11[.]com, get11-serv[.]com, and acquire11install[.]com, and ms-groups-application[.]net.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In addition, the cybersecurity company cautioned that the threat actor driving the impersonation campaign is also leveraging backdoored versions of Adobe Photoshop and other genuine application these as Microsoft Groups to deliver Vidar malware.
The ISO file, for its part, contains an executable that is unusually substantial in dimension (around 300MB) in an try to evade detection by security answers and is signed with an expired certificate from Avast that was possible stolen following the latter’s breach in Oct 2019.
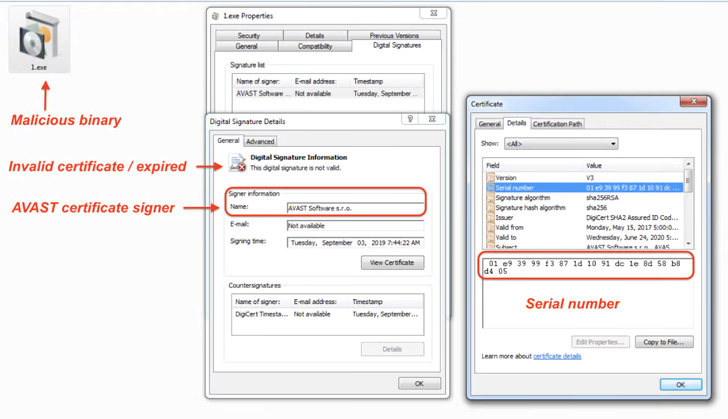
But embedded within just the 330MB binary is a 3.3MB-sized executable that’s the Vidar malware, with the relaxation of the file material padded with 0x10 bytes to artificially inflate the dimensions.
In the next stage of the attack chain, Vidar establishes connections to a distant command-and-manage (C2) server to retrieve reputable DLL information this sort of as sqlite3.dll and vcruntime140.dll to siphon valuable details from compromised devices.

Also noteworthy is the abuse of Mastodon and Telegram by the threat actor to retailer the C2 IP tackle in the description industry of the attacker-managed accounts and communities.
The conclusions incorporate to a record of diverse techniques that have been uncovered in the earlier thirty day period to distribute the Vidar malware, such as Microsoft Compiled HTML Support (CHM) information and a loader referred to as Colibri.
“The danger actors distributing Vidar malware have shown their means to social engineer victims into installing Vidar stealer utilizing themes associated to the latest common software apps,” the researchers reported.
“As usually, end users really should be cautious when downloading computer software applications from the Internet and download computer software only from the formal seller internet websites.”
Discovered this article attention-grabbing? Abide by THN on Facebook, Twitter and LinkedIn to read through a lot more unique information we article.
Some components of this posting are sourced from:
thehackernews.com

 QNAP Urges Users to Update NAS Devices to Prevent Deadbolt Ransomware Attacks
QNAP Urges Users to Update NAS Devices to Prevent Deadbolt Ransomware Attacks