Taiwanese network-attached storage (NAS) devices maker QNAP on Thursday warned its consumers of a contemporary wave of DeadBolt ransomware attacks.
The intrusions are explained to have targeted TS-x51 sequence and TS-x53 series appliances working on QTS 4.3.6 and QTS 4.4.1, according to its solution security incident response staff.
“QNAP urges all NAS buyers to examine and update QTS to the most up-to-date model as shortly as achievable, and keep away from exposing their NAS to the internet,” QNAP reported in an advisory.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This progress marks the 3rd time QNAP units have arrive underneath assault from DeadBolt ransomware given that the start of the calendar year.
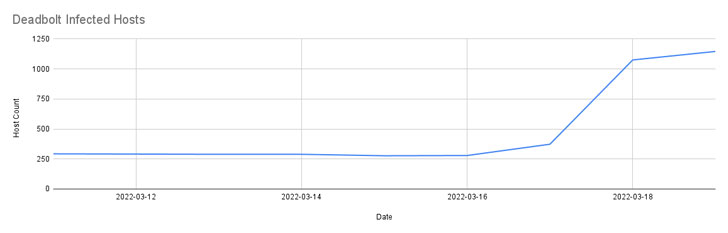
In late January, as a lot of as 4,988 DeadBolt-infected QNAP gadgets have been recognized, prompting the organization to release a forced firmware update. A next uptick in new infections was observed in mid-March.

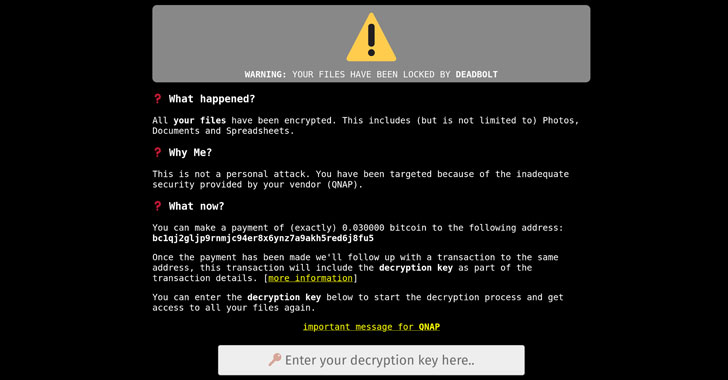
DeadBolt attacks are also notable for the truth that they allegedly leverage zero-day flaws in the software program to attain remote accessibility and encrypt the systems.
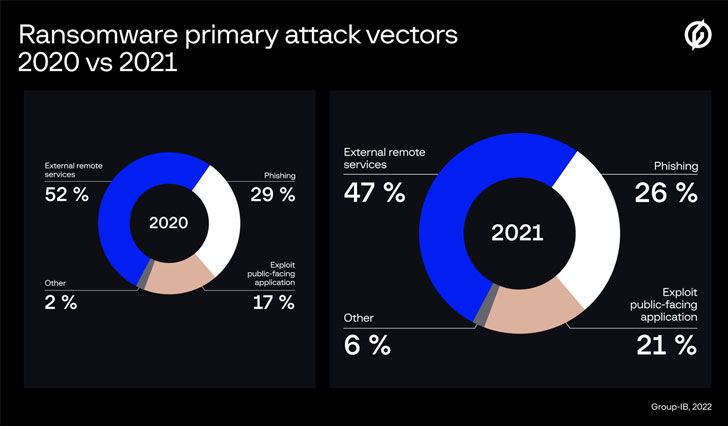
According to a new report released by Team-IB, exploitation of security vulnerabilities in community-struggling with applications emerged as the 3rd most used vector to attain original entry, accounting for 21% of all ransomware attacks investigated by the firm in 2021.
Observed this write-up exciting? Follow THN on Fb, Twitter and LinkedIn to study a lot more unique content material we write-up.
Some parts of this write-up are sourced from:
thehackernews.com

 CISA Issues Emergency Directive for VMware Vulnerabilities
CISA Issues Emergency Directive for VMware Vulnerabilities