Chinese-talking folks in Southeast and East Asia are the targets of a new rogue Google Ads marketing campaign that delivers remote accessibility trojans this kind of as FatalRAT to compromised devices.
The attacks contain buying ad slots to surface in Google look for effects that direct end users seeking for well-liked purposes to rogue internet sites hosting trojanized installers, ESET stated in a report published currently. The adverts have because been taken down.
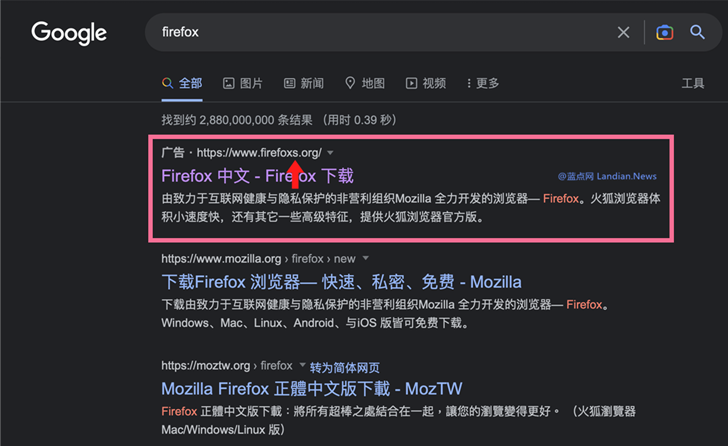
Some of the spoofed purposes incorporate Google Chrome, Mozilla Firefox, Telegram, WhatsApp, LINE, Sign, Skype, Electrum, Sogou Pinyin Technique, Youdao, and WPS Workplace.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The websites and installers downloaded from them are typically in Chinese and in some situations falsely provide Chinese language versions of software that is not accessible in China,” the Slovak cybersecurity agency stated, adding it observed the attacks between August 2022 and January 2023.
A bulk of the victims are found in Taiwan, China, and Hong Kong, followed by Malaysia, Japan, the Philippines, Thailand, Singapore, Indonesia, and Myanmar.
The most crucial part of the attacks is the creation of lookalike internet websites with typosquatted domains to propagate the destructive installer, which, in an try to continue to keep up the ruse, installs the respectable software, but also drops a loader that deploys FatalRAT.
In doing so, it grants the attacker entire command of the victimized personal computer, like executing arbitrary shell instructions, working data files, harvesting details from web browsers, and capturing keystrokes.
“The attackers have expended some effort concerning the domain names utilized for their internet websites, making an attempt to be as very similar to the official names as feasible,” the scientists reported. “The bogus internet websites are, in most instances, equivalent copies of the genuine web-sites.”
The results arrive fewer than a year soon after Development Micro disclosed a Purple Fox marketing campaign that leveraged tainted application offers Adobe, Google Chrome, Telegram, and WhatsApp as an arrival vector to propagate FatalRAT.
They also get there amid a broader abuse of Google Ads to provide a large assortment of malware, or alternatively, take users to credential phishing webpages.
In a associated enhancement, Symantec’s Threat Hunter Crew drop light-weight on yet another malware marketing campaign that targets entities in Taiwan with a formerly undocumented .NET-primarily based implant dubbed Frebniis.
“The method utilised by Frebniis consists of injecting destructive code into the memory of a DLL file (iisfreb.dll) similar to an IIS aspect made use of to troubleshoot and review failed web site requests,” Symantec said.
“This will allow the malware to stealthily keep track of all HTTP requests and identify specifically formatted HTTP requests despatched by the attacker, enabling for remote code execution.”
The cybersecurity organization, which attributed the intrusion to an unidentified actor, stated it truly is at present not identified how accessibility to the Windows equipment running the Internet Details Products and services (IIS) server was received.
Located this posting attention-grabbing? Observe us on Twitter and LinkedIn to browse much more distinctive information we submit.
Some areas of this post are sourced from:
thehackernews.com


