Security researchers have disclosed two new vulnerabilities affecting Schneider Electric powered Modicon programmable logic controllers (PLCs) that could allow for for authentication bypass and remote code execution.
The flaws, tracked as CVE-2022-45788 (CVSS score: 7.5) and CVE-2022-45789 (CVSS score: 8.1), are part of a broader assortment of security defects tracked by Forescout as OT:ICEFALL.
Prosperous exploitation of the bugs could enable an adversary to execute unauthorized code, denial-of-services, or disclosure of sensitive facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
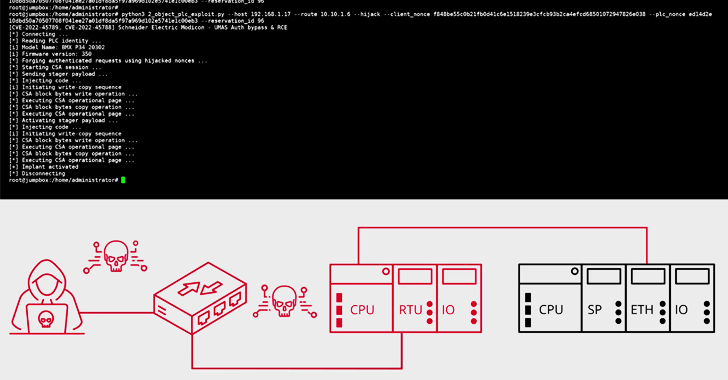
The cybersecurity enterprise reported the shortcomings can be chained by a menace actor with known flaws from other vendors (e.g., CVE-2021-31886) to attain deep lateral motion in operational technology (OT) networks.
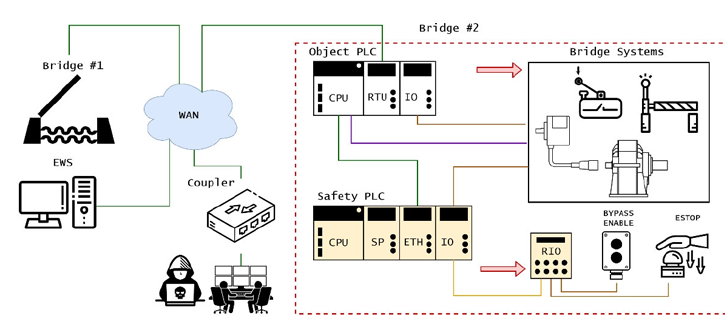
“Deep lateral movement lets attackers gain deep access to industrial manage programs and cross usually missed security perimeters, allowing them to complete very granular and stealthy manipulations as well as override useful and safety restrictions,” Forescout claimed.
A remarkably intricate proof-of-notion (PoC) cyber-physical attack devised by the San Jose-dependent business observed that the flaws could be weaponized to bypass safety guardrails and inflict injury upon a movable bridge infrastructure.
With menace actors concocting innovative malware to disrupt industrial management techniques, the deep lateral movement afforded by these flaws could allow adversaries to use an “uninteresting machine as a staging point for shifting in direction of much more interesting targets.”
The conclusions appear close on the heels of 38 security flaws that have been exposed in wi-fi industrial internet of issues (IIoT) equipment and which could grant an attacker a direct line of access to OT networks, in accordance to cybersecurity organization Otorio.
Taken together, the weaknesses also underscore the serious threats to bodily functions from IoT products, cloud-based mostly administration platforms, and nested OT networks.
Discovered this posting interesting? Adhere to us on Twitter and LinkedIn to go through a lot more exceptional articles we post.
Some sections of this short article are sourced from:
thehackernews.com

 Gatewatcher to begin “aggressive” UK channel partner recruitment drive
Gatewatcher to begin “aggressive” UK channel partner recruitment drive