An unknown risk actor made use of a malicious self-extracting archive (SFX) file in an try to establish persistent backdoor entry to a victim’s environment, new conclusions from CrowdStrike show.
SFX documents are capable of extracting the data contained within them with no the have to have for dedicated computer software to display screen the file contents. It achieves this by which include a decompressor stub, a piece of code that is executed to unpack the archive.
“Even so, SFX archive files can also incorporate hidden malicious features that may well not be immediately noticeable to the file’s recipient, and could be skipped by technology-based detections by itself,” CrowdStrike researcher Jai Minton reported.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
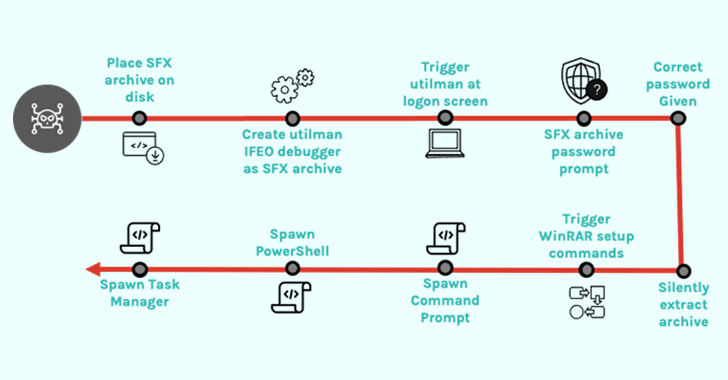
In the circumstance investigated by the cybersecurity organization, compromised qualifications to a process were being applied to operate a authentic Windows accessibility software known as Utility Manager (utilman.exe) and subsequently launch a password-shielded SFX file.
This, in transform, is created doable by configuring a debugger method (yet another executable) in the Windows Registry to a specific plan (in this scenario, utilman.exe) so that the debugger is routinely started out every single time the method is launched.
The abuse of utilman.exe is also noteworthy as it can be released straight from the Windows login screen by utilizing the Windows emblem crucial + U keyboard shortcut, potentially enabling risk actors to configure backdoors by using the Image File Execution Possibilities Registry important.
“Nearer inspection of the SFX archive revealed that it functions as a password-secured backdoor by abusing WinRAR setup selections relatively than made up of any malware,” Minton explained.
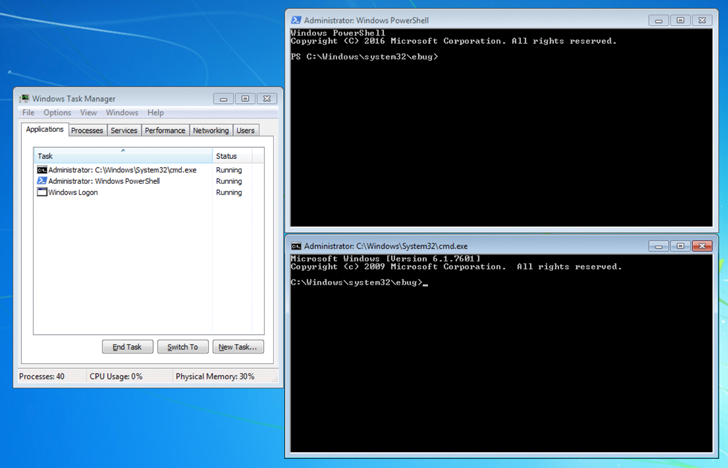
Exclusively, the file is engineered to operate PowerShell (powershell.exe), Command Prompt (cmd.exe), and Undertaking Supervisor (taskmgr.exe) with NT AUTHORITYSYSTEM privileges by giving the correct password to the archive.
“This form of attack is probably to keep on being undetected by classic antivirus software package that is hunting for malware within of an archive (which is frequently also password-protected) rather than the habits from an SFX archive decompressor stub,” Minton additional.
Upcoming WEBINARLearn to Protected the Identification Perimeter – Verified Strategies
Strengthen your company security with our impending qualified-led cybersecurity webinar: Investigate Id Perimeter approaches!
Will not Skip Out – Preserve Your Seat!
This is not the very first time SFX documents have been employed in attacks as a signifies for attackers to stay undetected. In September 2022, Kaspersky disclosed a malware campaign that used inbound links to such password-shielded files to propagate RedLine Stealer.
A thirty day period later, the infamous Emotet botnet was observed sending out an SFX archive that, as soon as opened by a user, would routinely extract a 2nd password-shielded SFX archive, enter the password, and execute its content without having even more consumer interaction applying a batch script.
To mitigate threats posed by this attack vector, it truly is encouraged that SFX archives are analyzed through unarchiving computer software to recognize any prospective scripts or binaries that are set to extract and run on execution.
Found this report fascinating? Observe us on Twitter and LinkedIn to read more exceptional written content we put up.
Some pieces of this post are sourced from:
thehackernews.com

 Google TAG Warns of North Korean-linked ARCHIPELAGO Cyberattacks
Google TAG Warns of North Korean-linked ARCHIPELAGO Cyberattacks