Introduction
The modern software supply chain signifies an at any time-evolving risk landscape, with each offer added to the manifest introducing new attack vectors. To fulfill industry requirements, organizations must maintain a fast-paced enhancement procedure whilst remaining up-to-date with the newest security patches. Nevertheless, in apply, developers frequently face a huge sum of security do the job with out apparent prioritization – and skip a considerable portion of the attack area altogether.
The key issue occurs from the detection and prioritization solutions utilised by conventional Static Code Assessment (SCA) applications for vulnerabilities. These approaches lack the organizational-certain context essential to make an informed scoring selection: the rating, even if critical, may well not basically be critical for an corporation since its infrastructure is effective in a exclusive way – impacting the true impression the vulnerability might have.
In other words, considering that these tools depend on a fairly naive methodology to establish a vulnerability’s risk, they close up with largely irrelevant vulnerability scores – producing pinpointing which vulnerabilities to tackle very first significantly more difficult.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Additionally, they do not tackle many source chain attacks, these kinds of as typosquatting, malicious code injection, CI/CD attacks, etcetera. This oversight misleads Software Security (AppSec) teams and builders into concentrating on significantly less critical issues, so delaying the growth course of action and leaving the business susceptible to considerable attack vectors.
Myrror Security develops revolutionary options to these issues by revolutionizing how corporations detect, prioritize and remediate their source chain hazards. Myrror’s system guarantees that AppSec and engineering teams tackle the ideal issues at the appropriate time by employing binary-to-source analysis for just about every 3rd-party deal in the codebase. Contrary to standard SCA tools that assess affect applying edition-degree detection in manifest files, Myrror uses a proprietary reachability vulnerability analysis algorithm. This algorithm identifies which vulnerabilities are basically reachable in creation, as a result enabling Myrror to prioritize security issues precisely.
This Platform Overview will guideline you via the total Myrror consumer journey, from the preliminary SCM integration to the remediation plan generator, and offer a concise overview of the innovations Myrror Security has released to avert alert fatigue, empower your corporation to perform extra proficiently and shield it from the threats of the modern-day application supply chain. To get a personalised demo, take a look at their web-site in this article.
Receiving Began and Set up
Myrror is developed for easy set up on the organization’s current resource code administration platform. When Myrror is connected to your SCM, a discovery course of action of the organization’s dependencies starts. The firm can later on pick out certain repositories for lively vulnerability and source chain attack scanning, giving a prioritized overview of determined hazards.
The Discovery Area
This segment permits you to choose stock of the supply chain risk involved with your codebase and determine the actual menace landscape you happen to be exposed to from your open-supply dependencies.

The Repositories tab exhibits you all the issues in every monitored repository and allows you to select which to keep track of and which to overlook. This will permit you to clear away some sounds connected with repositories that are not in lively use, will before long be deprecated, or are simply just irrelevant. This tab serves as the manage panel over all of your repositories. It enhances the issues display by pointing you towards your most at-risk repositories – making it possible for for a venture- or software-degree “bird’s eye” watch of the threats.
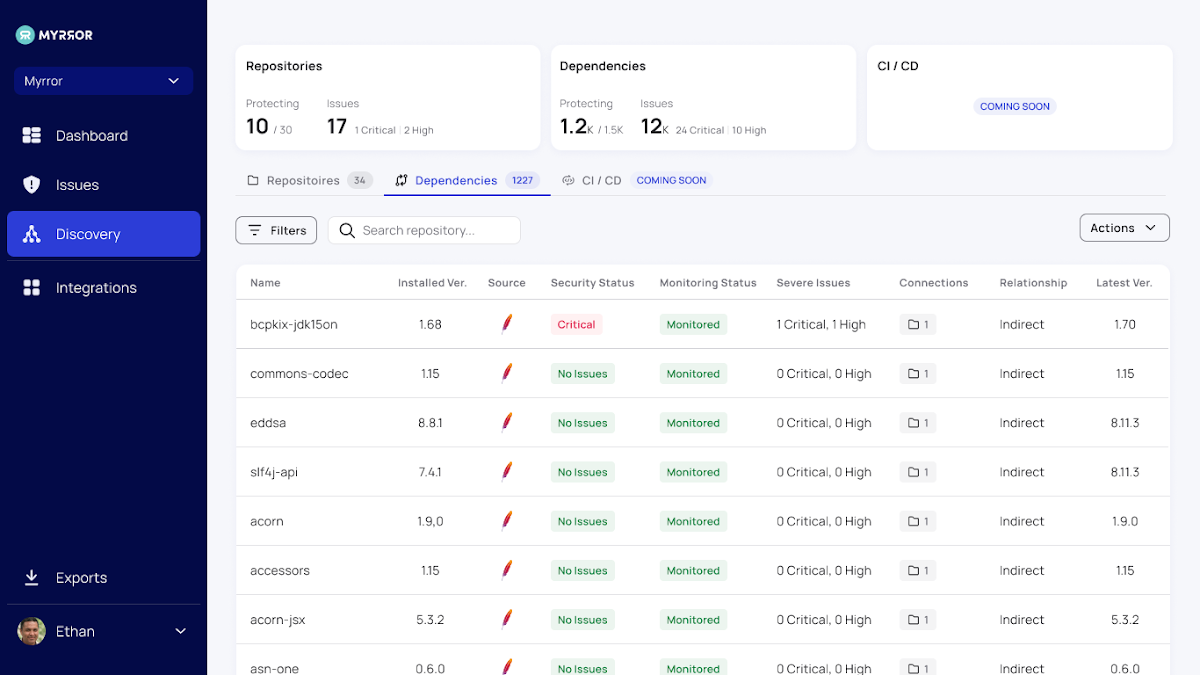
The Dependencies tab aggregates just about every open up-resource dependency in your codebase and results in a graph of all the repositories in which just about every 1 is applied. This vital overview allows you to get a comprehensive photograph of the open up-supply libraries your business relies upon. Irrespective of the immense raise in open-supply repositories in generally each software package project, businesses do not have any regulate about exterior dependencies getting inventory of what is getting applied in your code is the initially step to controlling what is actually happening.
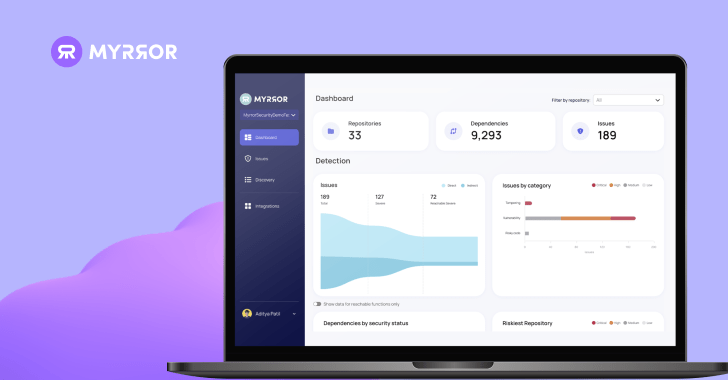
The Myrror Dashboard
After the set up is total and the user chooses the repositories to scan, the Myrror dashboard is populated with details about your repositories, their dependencies, and the issues they incorporate. When the consumer chooses to watch more repositories or join a lot more SCM sources, the dashboard is routinely up-to-date with additional facts about the new codebases.

The dashboard provides higher-amount insights into the issues throughout the complete established of the organization’s codebase, which include:
- Detection Standing
- Issues by classification
- Dependencies with Security Position
- The Riskiest Repository
- Issues per code language,
- Status of Remediation
- Out-of-information Dependencies
- And much more
These charts and graphs generate a thorough and total overview, furnishing businesses with apparent insights into parts necessitating the most perform. Note the repository filter on the prime right – this will allow particular groups to get precise data about their work and the repositories they are in charge of and export only the related info for them.
The Issues Display screen
This is the core of the Myrror Security system. Below, all your issues are prioritized and flagged according to their genuine severity, reachability, and exploitability for a obvious comprehending of what to deal with future. Different parameters are arranged into columns, presenting much more profound insights into each and every specific issue.

Among these parameters, the reachability column sets Myrror apart from classic SCA platforms. It assesses whether or not the issue is actually reachable in manufacturing, which components into the prioritization – guaranteeing reachable vulnerabilities can be tackled initial.
But the system doesn’t prevent at prioritizing vulnerabilities according to reachability – it also considers whether this is a immediate or oblique dependency, no matter if a correct is readily available to remediate the issue, and regardless of whether an exploit has been verified to exist in the wild. All of these parameters enable the system prioritize issues properly and reliably.
You can see all the adhering to pieces of details about each and every vulnerability:
- Severity (having all the above aspects into account)
- Origin
- Reachability
- Dependency File(s)
- Class – Vulnerability / Source Chain Attack (see extra in the Detecting Supply Chain Attacks portion)
- Exploit Availability
- Deal with Availability
- Dependency Romance
- 1st Observed
- Unique Dedicate
Filters (including a repository filter) are offered in this article too, along with an selection to export the desk and obtain insights for report creation. This helps security groups in protecting records in neighborhood storage and generating inner audit stories. These stories, emailed to the consumer, comprise thorough info directly from the system that can be shared with other crew associates and stakeholders.
Observe that there are 3 distinct tabs obtainable on this monitor:
- The “All” tab includes all the issues put together, offering data insights in a single page about the overall supply chain risk landscape – which includes vulnerabilities and attacks.
- The “suggested” tab is made up of the specific issues encouraged for remediation for each severity and reachability – primarily your “go-to” pane when determining what to deal with initial.
- Ultimately, the “Minimal Risk” tab has issues that you can offer with at a later point in time.
Just about every issue also has its in-depth examination, with insights on the impression, scope, and origin of the issues shown on one display screen. This comprehensive overview gives external inbound links to the CVE to learn extra about it, as nicely as facts about the afflicted repositories and a concrete remediation plan to assure swift motion can be taken on just about every issue.
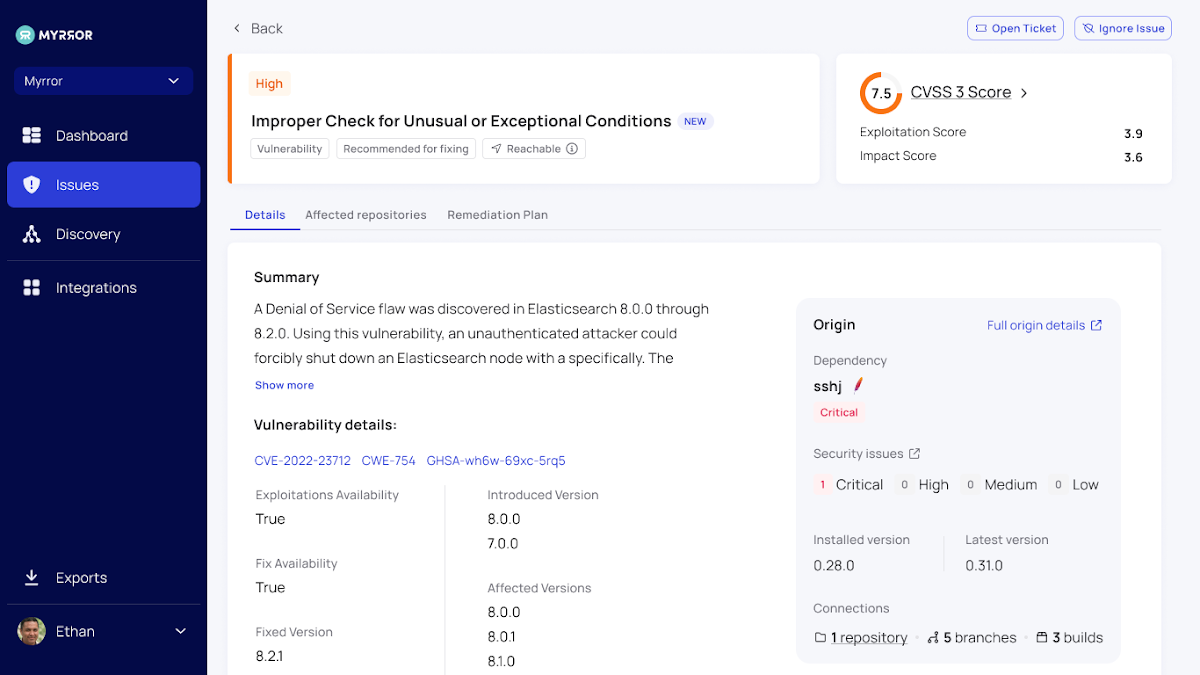
The most important tabs readily available on this monitor are:
- Information – a principal overview of the vulnerability or provide chain attack
- Afflicted Repositories – a list of all repositories that rely on this bundle, making it possible for you to “link the dots” throughout the total monitored codebase
- Remediation Plan – Myrror calculates the exceptional path of remediation, ensuring that the smallest amount of money of newly-launched vulnerabilities stop up in the codebase soon after the remediation system is entire
- Attack Overview (see following part for much more aspects)
Detecting Offer Chain Attacks
Retain in brain that Myrror does more than just detect vulnerabilities – it also detects a variety of forms of offer chain attacks – which include but not constrained to:
- Typosquatting
- Dependency Confusion
- Destructive Code In Repo / Code Injection
- CI/CD Attack
When it detects all those attacks, the detection system and remediation plan may not be as clear-cut as typical vulnerabilities. In those cases, Myrror will demonstrate a additional in-depth examination of the attack, enabling practitioners to grasp the circumstance and pinpoint the concrete hyperlink in the chain that is at fault. See down below for an case in point of Myrror’s evaluation of a code injection attack:

The Remediation Plan Generator
Organizing your remediation attempts commonly requires comprehending the new threats launched throughout patching. In most scenarios, applying a patch outcomes in a new established of vulnerabilities because of to the new dependencies (and their transitive dependencies) it introduces.
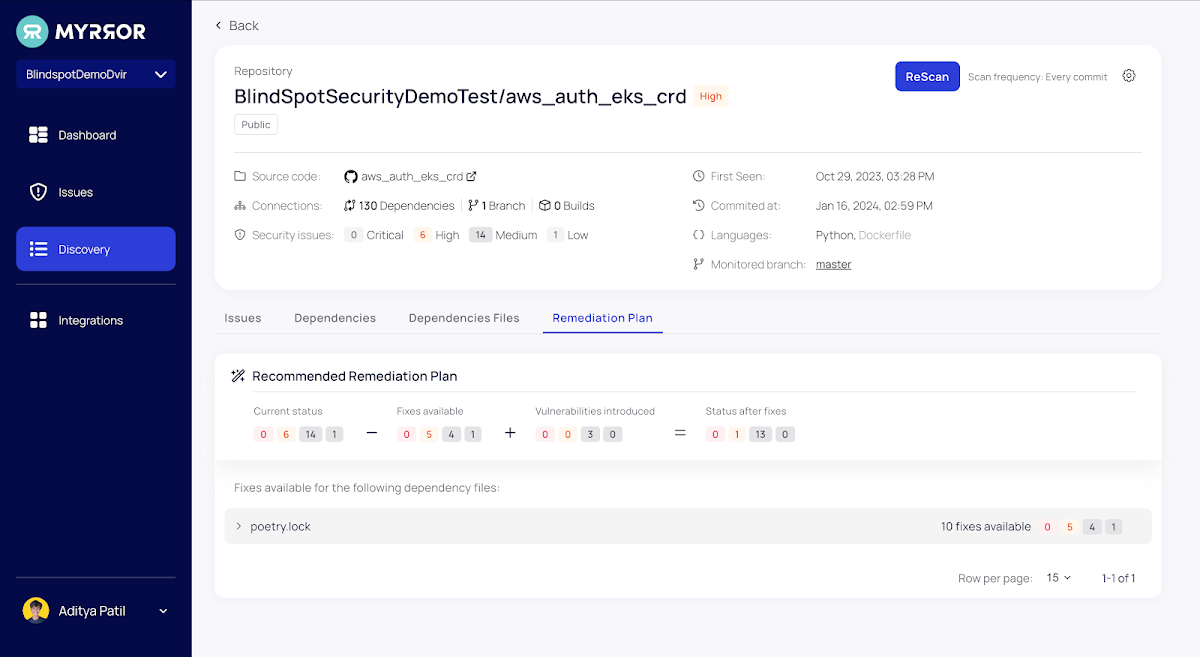
For just about every monitored repository, Myrror simplifies the issue remediation process by mechanically calculating the quantity of fixes obtainable for all the issues, how quite a few new vulnerabilities will be introduced during the remediation course of action, and how many issues will stay at the finish.
Summary
AppSec groups go through from profound inform exhaustion right now, driven by an overwhelming amount of money of security issues and a lack of apparent prioritization of what to work on very first. In addition, most teams are completely unaware of the supply chain attacks they are uncovered to and have no distinct route for detecting them or supplying proper remediation.
Myrror’s Reachability-primarily based prioritization provides a way out of vulnerability hell. At the similar time, their binary-to-source assessment system enables detection of a lot more than just very simple vulnerabilities – and permits you to defend in opposition to a host of supply chain attacks.
You can guide a demo to find out more on their web-site below.
Uncovered this short article attention-grabbing? Abide by us on Twitter and LinkedIn to browse extra special articles we post.
Some components of this report are sourced from:
thehackernews.com

 New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack
New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack