Cybersecurity scientists are warning of suspected exploitation of a not too long ago disclosed critical security flaw in the Apache ActiveMQ open up-resource information broker assistance that could result in distant code execution.
“In both cases, the adversary attempted to deploy ransomware binaries on goal devices in an hard work to ransom the victim corporations,” cybersecurity business Swift7 disclosed in a report released Wednesday.
“Primarily based on the ransom observe and offered evidence, we attribute the exercise to the HelloKitty ransomware family members, whose source code was leaked on a discussion board in early Oct.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The intrusions are said to include the exploitation of CVE-2023-46604, a distant code execution vulnerability in Apache ActiveMQ that allows a danger actor to run arbitrary shell instructions.

It’s really worth noting that the vulnerability carries a CVSS score of 10., indicating maximum severity. It has been tackled in ActiveMQ versions 5.15.16, 5.16.7, 5.17.6, or 5.18.3 launched late previous month.
The vulnerability impacts the subsequent versions –
- Apache ActiveMQ 5.18. in advance of 5.18.3
- Apache ActiveMQ 5.17. prior to 5.17.6
- Apache ActiveMQ 5.16. ahead of 5.16.7
- Apache ActiveMQ in advance of 5.15.16
- Apache ActiveMQ Legacy OpenWire Module 5.18. ahead of 5.18.3
- Apache ActiveMQ Legacy OpenWire Module 5.17. just before 5.17.6
- Apache ActiveMQ Legacy OpenWire Module 5.16. just before 5.16.7
- Apache ActiveMQ Legacy OpenWire Module 5.8. before 5.15.16
Since the bugs’ disclosure, a proof-of-concept (PoC) exploit code and further complex particulars have been created publicly out there, with Speedy7 noting that the actions it observed in the two target networks is “very similar to what we would count on from exploitation of CVE-2023-46604.”

Productive exploitation is followed by the adversary trying to load remote binaries named M2.png and M4.png making use of the Windows Installer (msiexec).
Each the MSI data files include a 32-little bit .NET executable named dllloader that, in turn, masses a Base64-encoded payload referred to as EncDLL that capabilities akin to ransomware, hunting and terminating a unique established of processes in advance of commencing the encryption approach and appending the encrypted documents with the “.locked” extension.
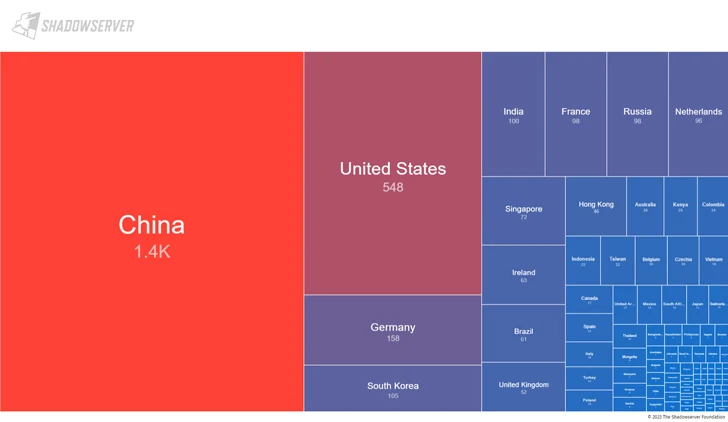 Graphic Source: Shadowserver Foundation
Graphic Source: Shadowserver Foundation
The Shadowserver Basis stated it discovered 3,326 internet-accessible ActiveMQ cases that are susceptible to CVE-2023-46604 as of November 1, 2023. A bulk of the vulnerable servers are found in China, the U.S., Germany, South Korea, and India.
In gentle of the energetic exploitation of the flaw, buyers are advisable to update to the preset version of ActiveMQ as soon as achievable and scan their networks for indicators of compromise.
Found this write-up fascinating? Stick to us on Twitter and LinkedIn to read through a lot more unique written content we publish.
Some parts of this report are sourced from:
thehackernews.com


 Researchers Expose Prolific Puma’s Underground Link Shortening Service
Researchers Expose Prolific Puma’s Underground Link Shortening Service