Malware investigation encompasses a wide vary of routines, which include examining the malware’s network traffic. To be powerful at it, it’s essential to realize the popular challenges and how to overcome them. Right here are a few widespread issues you could face and the instruments you can expect to have to have to address them.
Decrypting HTTPS targeted traffic
Hypertext Transfer Protocol Safe (HTTPS), the protocol for protected on the net interaction, has develop into a tool for malware to conceal their malicious activities. By cloaking details trade involving contaminated equipment and command-and-command (C&C) servers, malware can operate undetected, exfiltrating sensitive info, setting up added payloads, and receiving guidelines from the operators.
However, with the appropriate resource, decrypting HTTPS traffic is an uncomplicated task. For this objective, we can use a person-in-the-center (MITM) proxy. The MITM proxy is effective as an middleman among the customer and the server, intercepting their interaction.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The MITM proxy aids analysts in authentic-time monitoring of the malware’s network targeted visitors, providing them with a clear view of its things to do. Between other items, analysts can access material of ask for and response packets, IPs, and URLs to watch the information of the malware’s conversation and detect stolen data. The device is especially valuable for extracting SSL keys made use of by the malware.
Use scenario
 Information and facts about AxileStealer offered by the ANY.Run sandbox
Information and facts about AxileStealer offered by the ANY.Run sandbox
In this case in point, the initial file, 237.06 KB in sizing, drops AxilStealer’s executable file, 129.54 KB in sizing. As a standard stealer, it gains access to passwords saved in web browsers and commences to transfer them to attackers by way of a Telegram messenger link.
The malicious activity is indicated by the rule “STEALER [ANY.RUN] Try to exfiltrate by way of Telegram”. Thanks to the MITM proxy attribute, the malware’s visitors is decrypted, revealing extra specifics about the incident.
Malware Analysis
Use a MITM proxy and dozens of other advanced attributes for in-depth malware assessment in the ANY.Run sandbox.
Ask for a free demo
Discovering malware’s family
Malware spouse and children identification is a crucial component of any cyber investigation. Yara and Suricata regulations are typically made use of equipment for this task, but their efficiency may be constrained when dealing with malware samples whose servers are no lengthier energetic.
FakeNET delivers a resolution to this challenge by producing a pretend server connection that responds to malware requests. Tricking the malware to send a ask for triggers a Suricata or YARA rule, which properly identifies the malware family members.
Use circumstance
 Inactive servers detected by the ANY.Operate sandbox
Inactive servers detected by the ANY.Operate sandbox
When analyzing this sample, the sandbox details to the fact that the malware’s servers are unresponsive.
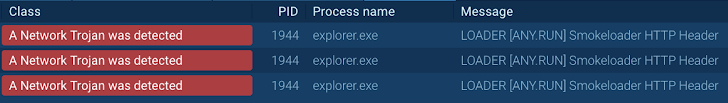 Smoke Loader malware identified making use of FakeNET
Smoke Loader malware identified making use of FakeNET
Nevertheless, right after enabling the FakeNET attribute, the malicious software package immediately sends a ask for to a phony server, triggering the network rule that identifies it as Smoke Loader.
Catching geo-focused and evasive malware
Numerous attacks and phishing strategies emphasis on certain geographic areas or nations around the world. Subsequently, they incorporate mechanisms like IP geolocation, language detection, or website blocking which could restrict analysts’ ability to detect them.
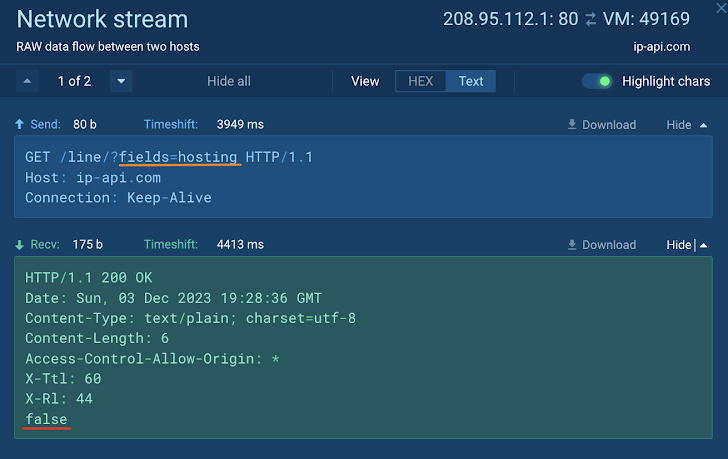
Together with geo-targeting, malware operators may leverage tactics to evade assessment in sandbox environments. A typical approach is to verify whether or not the system is making use of a datacenter IP address. If verified, the destructive software stops execution.
To counter these obstructions, analysts use a household proxy. This nifty resource operates by switching the IP deal with of the analyst’s device or digital equipment to standard users’ household IPs from different sections of the globe.
This attribute empowers experts to bypass geo-restrictions by mimicking neighborhood consumers and review destructive activities without the need of revealing their sandbox ecosystem.
Use scenario
 Smoke Loader malware identified using FakeNET
Smoke Loader malware identified using FakeNET
Right here, Xworm instantaneously checks for a hosting IP tackle as shortly as it is uploaded to a sandbox. But, since the VM has a household proxy, the malware carries on to execute and connects to its command-and-management server.
Try out all of these tools in ANY.Run
Environment up and utilizing every of the aforementioned equipment individually can just take a whole lot of effort and hard work. To accessibility and benefit from all of them with relieve, use the cloud-primarily based ANY.Run sandbox.
The vital aspect of the provider is interactivity, enabling you to properly have interaction with malware and the infected process just like you would on your personal laptop.
You can examine these and many other attributes of ANY.Run, which include personal room for your group, Windows 7, 8, 10, 11 VMs, and API integration fully for totally free.
Just use a 14-day demo, no strings hooked up.
Discovered this short article appealing? Comply with us on Twitter and LinkedIn to read through additional distinctive information we post.
Some elements of this article are sourced from:
thehackernews.com


 Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing
Microsoft Warns of Hackers Exploiting OAuth for Cryptocurrency Mining and Phishing