Microsoft has warned that adversaries are working with OAuth applications as an automation instrument to deploy digital machines (VMs) for cryptocurrency mining and launch phishing attacks.
“Risk actors compromise user accounts to develop, modify, and grant large privileges to OAuth programs that they can misuse to hide malicious exercise,” the Microsoft Menace Intelligence team reported in an analysis.
“The misuse of OAuth also permits threat actors to preserve entry to purposes even if they eliminate accessibility to the to begin with compromised account.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Approaching WEBINAR Beat AI-Powered Threats with Zero Rely on – Webinar for Security Specialists
Common security steps will not lower it in present-day earth. It truly is time for Zero Rely on Security. Protected your details like by no means prior to.
Be a part of Now
OAuth, quick for Open up Authorization, is an authorization and delegation framework (as opposed to authentication) that supplies programs the capability to securely access info from other sites without having handing in excess of passwords.
In the attacks specific by Microsoft, threat actors have been observed launching phishing or password-spraying attacks in opposition to poorly secured accounts with permissions to build or modify OAuth applications.

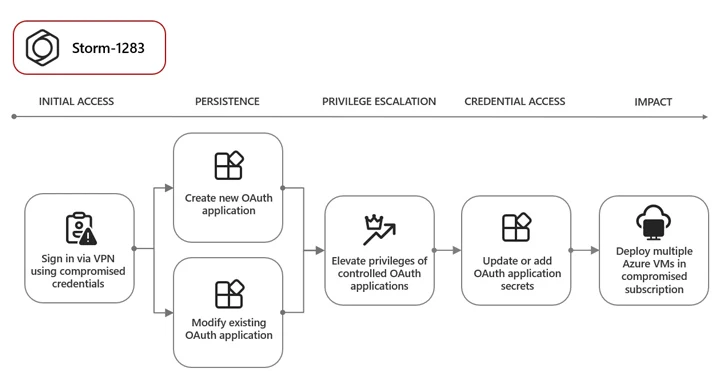
1 these adversary is Storm-1283, which has leveraged a compromised user account to generate an OAuth application and deploy VMs for cryptomining. Moreover, the attackers modified current OAuth apps to the account had entry to by incorporating an excess established of credentials to aid the identical aims.
In yet another instance, an unidentified actor compromised user accounts and produced OAuth programs to maintain persistence and to launch email phishing attacks that make use of an adversary-in-the-middle (AiTM) phishing kit to plunder session cookies from their targets and bypass authentication actions.

“In some scenarios, adhering to the stolen session cookie replay activity, the actor leveraged the compromised consumer account to execute BEC economical fraud reconnaissance by opening email attachments in Microsoft Outlook Web Application (OWA) that comprise specific keywords this kind of as ‘payment’ and ‘invoice,” Microsoft reported.
Other situations detected by the tech huge pursuing the theft of session cookies include the creation of OAuth programs to distribute phishing emails and perform massive-scale spamming action. Microsoft is tracking the latter as Storm-1286.
To mitigate the pitfalls associated with these kinds of attacks, it is encouraged that organizations enforce multi-factor authentication (MFA), empower conditional entry guidelines, and routinely audit applications and consented permissions.
Found this write-up attention-grabbing? Abide by us on Twitter and LinkedIn to study more special content we put up.
Some elements of this report are sourced from:
thehackernews.com

 Major Cyber Attack Paralyzes Kyivstar – Ukraine’s Largest Telecom Operator
Major Cyber Attack Paralyzes Kyivstar – Ukraine’s Largest Telecom Operator