Find all the means MITRE ATT&CK can assist you defend your organization. Develop your security system and policies by creating the most of this significant framework.
What is the MITRE ATT&CK Framework?
MITRE ATT&CK (Adversarial Strategies, Techniques, and Prevalent Knowledge) is a broadly adopted framework and knowledge base that outlines and categorizes the practices, tactics, and treatments (TTPs) applied in cyberattacks. Made by the nonprofit firm MITRE, this framework delivers security gurus with insights and context that can support them understand, determine, and mitigate cyber threats properly.
The approaches and practices in the framework are organized in a dynamic matrix. This makes navigation easy and also gives a holistic check out of the full spectrum of adversary behaviors. As a outcome, the framework is a lot more actionable and usable than if it had been a static listing.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The MITRE ATT&CK Framework can be identified right here: https://attack.mitre.org/
Glance Out: MITRE ATT&CK Framework Biases
According to Etay Maor, Senior Director of Security System at Cato Networks, “The know-how offered in the MITRE ATT&CK framework is derived from genuine-world proof of attackers’ behaviors. This makes it prone to sure biases that security pros need to be knowledgeable of. It is really important to fully grasp these limits.”
- Novelty Bias – Methods or actors that are new or appealing are described, even though procedures that are being employed above and about are not.
- Visibility Bias – Intel report publishers have visibility biases that are based on how they assemble details, resulting in visibility for some tactics and not some others. Additionally, tactics are also considered in a different way in the course of incidents and afterward.
- Producer Bias – Reviews revealed by some corporations may well not mirror the broader marketplace or globe as a total.
- Target Bias – Some target companies are far more possible to report, or to be claimed on, than others.
- Availability Bias – Report authors frequently include strategies that immediately arrive to brain in their reports.
MITRE ATT&CK Defender Use Cases
The MITRE ATT&CK framework helps security pros investigate and evaluate numerous attacks and strategies. This can enable with menace intelligence, detection and analytics, simulations, and evaluation and engineering. The MITRE ATT&CK Navigator is a device that can support investigate and visualize the matrix, boosting the investigation for defensive protection, security preparing, approach frequency, and much more.
Etay Maor provides, “The framework can go as deep as you want it to be or it can be as high level as you want it to be. It can be made use of as a tool to demonstrate the mapping and if we’re superior or negative at certain parts, but it could go as deep as being familiar with the pretty precise procedure and even the line of code that was employed in a distinct attack.”
Below are a couple illustrations of how the framework and the Navigator can be used:
Risk Actor Investigation
Security experts can leverage MITRE ATT&CK to look into distinct risk actors. For illustration, they can drill down into the matrix and find out which techniques are made use of by diverse actors, how they are executed, which equipment they use, and so on. This info aids look into specified attacks. It also expands the researchers’ know-how and way of wondering by introducing them to further modes of procedure attackers just take.
At a bigger degree, the framework can be utilised to response C-degree questions about breaches or danger actors. For instance, if asked- “We consider we may be a target for Iranian nation state threat actors.” The framework permits drilling down into Iranian danger actors like APT33, demonstrating which strategies they use, attack IDs, and a lot more.
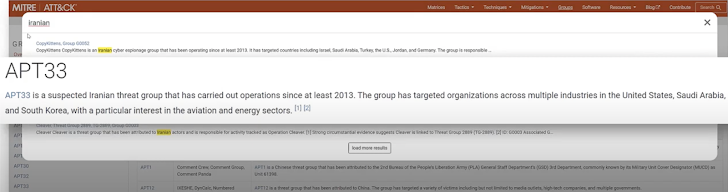
Multiple Menace Actor Assessment
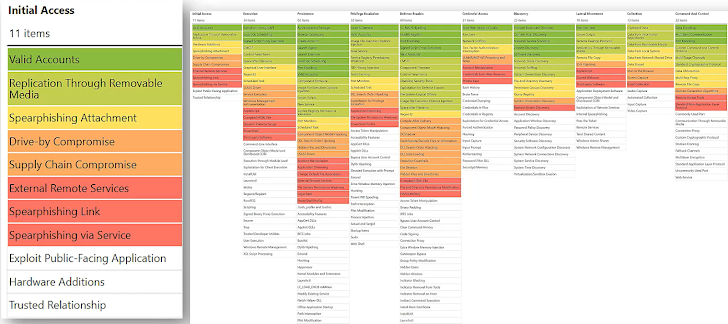
Aside from looking into precise actors, the MITRE ATT&CK framework also makes it possible for analyzing a number of risk actors. For case in point, if a issue is elevated that “Due to new political and armed service situations in Iran we imagine there will be a retaliation in the kind of a cyber attack. What are the common attack practices of Iranian menace actors?”, the framework can be employed to establish widespread ways used by a selection of country-state actors.
Here is what a visualized multiple danger actor evaluation could seem like, with pink and yellow symbolizing strategies utilised by different actors and inexperienced representing an overlap.

Hole Analysis
The MITRE ATT&CK framework also assists review existing gaps in defenses. This enables defenders to identify, visualize and kind which ones the organization does not have coverage for.
This is what it could seem like, with colours made use of for prioritization.
Atomic Screening
Ultimately, the Atomic Crimson Workforce is an open source library of tests mapped to the MITRE ATT&CK framework. These exams can be applied for screening your infrastructure and programs based on the framework, to assist determine and mitigate coverage gaps.
The MITRE CTID (Middle for Risk-Educated Defense)
The MITRE CTID (Centre for Risk-Informed Protection) is an R&D center, funded by personal entities, that collaborates with both of those private sector organizations and nonprofits. Their goal is to revolutionize the solution to adversaries as a result of source pooling and emphasizing proactive incident reaction rather than reactive steps. This mission is pushed by the perception, influenced by John Lambert, that defenders ought to shift from imagining in lists to considering in graphs if they want to conquer attackers’ advantages.
Etay Maor remarks, “This is quite significant. We will need to facilitate collaboration between the Defenders throughout distinct degrees. We’re really passionate about this.”
A significant initiative within this context is the “Attack Movement” challenge. Attack Move tackles the obstacle confronted by defenders, who frequently aim on unique, atomic attacker behaviors. As a substitute, Attack Flow makes use of a new language and equipment to explain the flow of ATT&CK strategies. These techniques are then merged into styles of habits. This tactic permits defenders and leaders to attain a deeper understanding of how adversaries work, so they can refine their tactics accordingly.
You can see right here what an Attack Stream seems like.
With these attack flows, defenders can reply inquiries like:
- What have adversaries been accomplishing?
- How are adversaries changing?
The answers can help them seize, share and examine designs of attack.
Then, they will be capable to reply the most significant issues:
- What is the up coming most very likely detail they will do?
- What have we missed?
CTID invitations the local community to take part in its things to do and lead to its information foundation. You can get hold of them on LinkedIn.
To understand much more about the MITRE ATT&CK framework, view the entire masterclass here.
Uncovered this report intriguing? Follow us on Twitter and LinkedIn to read through extra exceptional content material we publish.
Some areas of this posting are sourced from:
thehackernews.com


 SCARLETEEL Cryptojacking Campaign Exploiting AWS Fargate in Ongoing Campaign
SCARLETEEL Cryptojacking Campaign Exploiting AWS Fargate in Ongoing Campaign