A latest IcedID malware attack enabled the menace actor to compromise the Active Directory domain of an unnamed focus on significantly less than 24 hours soon after attaining original access.
“All through the attack, the attacker followed a regime of recon instructions, credential theft, lateral motion by abusing Windows protocols, and executing Cobalt Strike on the recently compromised host,” Cybereason scientists said in a report published this week.
IcedID, also identified by the name BokBot, begun its life as a banking trojan in 2017 in advance of evolving into a dropper for other malware, signing up for the likes of Emotet, TrickBot, Qakbot, Bumblebee, and Raspberry Robin.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Attacks involving the delivery of IcedID have leveraged a assortment of procedures, especially in the wake of Microsoft’s final decision to block macros from Business documents downloaded from the web.
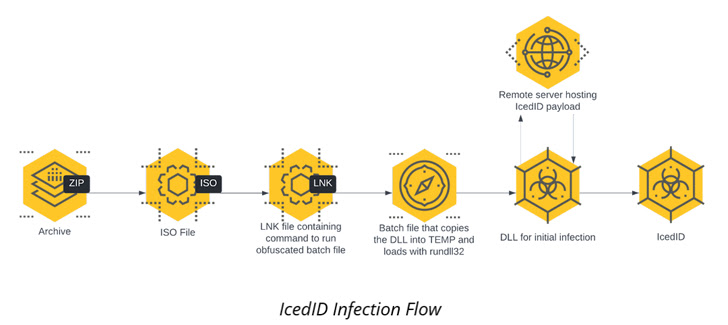
The intrusion comprehensive by Cybereason is no various in that the infection chain begins with an ISO impression file contained in just a ZIP archive that culminates in the execution of the IcedID payload.
The malware then establishes persistence on the host via a scheduled activity and communicates with a distant server to down load added payloads, such as Cobalt Strike Beacon for observe-on reconnaissance action.
It also carries out lateral motion across the network and executes the same Cobalt Strike Beacon in all those workstations, and then proceeds to set up Atera agent, a reputable distant administration device, as a redundant remote access mechanism.
“Utilizing IT applications like this lets attackers to create an more ‘backdoor’ for them selves in the event their first persistence mechanisms are identified and remediated,” the scientists claimed. “These tools are considerably less probable to be detected by antivirus or EDR and are also far more probably to be created off as bogus positives.”
The Cobalt Strike Beacon is more employed as a conduit to obtain a C# device dubbed Rubeus for credential theft, in the long run allowing the menace actor to move laterally to a Windows Server with domain admin privileges.
The elevated permissions are then weaponized to stage a DCSync attack, allowing the adversary to simulate the behavior of a domain controller (DC) and retrieve credentials from other area controllers.
Other applications used as aspect of the attack incorporate a respectable utility named netscan.exe to scan the network for lateral movement as well as the rclone file syncing program to exfiltrate directories of desire to the MEGA cloud storage provider.
The results come as researchers from Staff Cymru drop far more light-weight on the BackConnect (BC) protocol utilised by IcedID to provide additional performance publish compromise, including a VNC module that offers a remote-access channel.
“In the case of BC, there seems to be two operators running the total process inside unique roles,” the scientists observed previous thirty day period, including “a great deal of the action […] takes place throughout the common functioning 7 days.”
The development also follows a report from Proofpoint in November 2022 that a resurgence in Emotet exercise has been joined to the distribution of a new version of IcedID.
Observed this short article appealing? Stick to us on Twitter and LinkedIn to examine a lot more exceptional content we publish.
Some sections of this write-up are sourced from:
thehackernews.com


 Over 100 Siemens PLC Models Found Vulnerable to Firmware Takeover
Over 100 Siemens PLC Models Found Vulnerable to Firmware Takeover