Security scientists have disclosed numerous architectural vulnerabilities in Siemens SIMATIC and SIPLUS S7-1500 programmable logic controllers (PLCs) that could be exploited by a destructive actor to stealthily install firmware on affected equipment and choose handle of them.
Learned by Red Balloon Security, the issues are tracked as CVE-2022-38773 (CVSS score: 4.6), with the small severity stemming from the prerequisite that exploitation requires bodily tampering of the device.
The flaws “could make it possible for attackers to bypass all guarded boot functions, resulting in persistent arbitrary modification of working code and data,” the organization mentioned. A lot more than 100 versions are prone.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
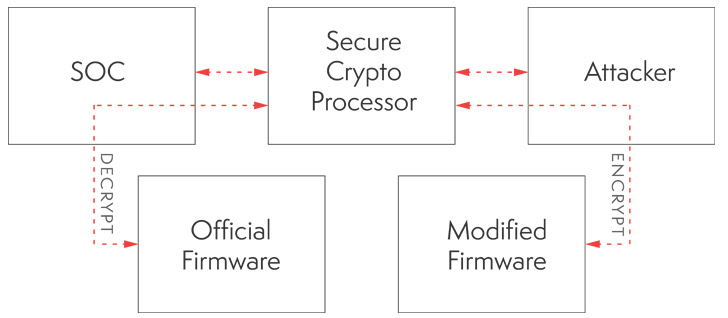
Set otherwise, the weaknesses are the outcome of a absence of uneven signature verifications for firmware at bootup, successfully allowing the attacker to load tainted bootloader and firmware whilst undermining integrity protections.
A far more intense consequence of loading such modified firmware is that it could give the menace actor the capability to persistently execute malicious code and get whole manage of the equipment without having elevating any red flags.
“This discovery has most likely sizeable implications for industrial environments as these unpatchable hardware root-of-rely on vulnerabilities could result in persistent arbitrary modification of S7-1500 working code and facts,” the scientists stated.
Siemens, in an advisory unveiled this week, reported it has no patches prepared but urged consumers to limit bodily access to the influenced PLCs to reliable staff to stay clear of hardware tampering.
The absence of a firmware update is attributed to the point that the cryptographic scheme that undergirds the secured boot functions is baked into a dedicated physical secure aspect chip (called the ATECC108 CryptoAuthentication coprocessor), which decrypts the firmware in memory through startup.
An attacker with physical entry to the gadget could as a result leverage the issues determined in the cryptographic implementation to decrypt the firmware, make unauthorized alterations, and flash the trojanized firmware onto the PLC possibly physically or by exploiting a acknowledged remote code execution flaw.
“The essential vulnerabilities — poor components implementations of the [Root of Trust] making use of committed cryptographic-processor — are unpatchable and can not be fixed by a firmware update considering the fact that the hardware is physically unmodifiable,” the scientists discussed.
However, the German automation big mentioned it is in the process of releasing new components variations for the S7-1500 solution family that appear with a revamped “secure boot system” that resolves the vulnerability.
The conclusions arrive as industrial security agency Claroty final year disclosed a critical flaw impacting Siemens SIMATIC products that could be exploited to retrieve the difficult-coded, world-wide private cryptographic keys and completely compromise the products.
Identified this short article exciting? Abide by us on Twitter and LinkedIn to browse more unique material we submit.
Some sections of this posting are sourced from:
thehackernews.com


 Microsoft’s VALL-E will usher in new era of cyber crime
Microsoft’s VALL-E will usher in new era of cyber crime