A menace actor affiliated with Iran’s Ministry of Intelligence and Security (MOIS) has been noticed waging a complex cyber espionage campaign targeting economic, authorities, army, and telecommunications sectors in the Middle East for at least a year.
Israeli cybersecurity company Examine Issue, which discovered the marketing campaign along with Sygnia, is tracking the actor less than the title Scarred Manticore, which is mentioned to intently overlap with an rising cluster dubbed Storm-0861, 1 of the four Iranian groups connected to destructive attacks on the Albanian governing administration previous calendar year.
Victims of the operation span various international locations this sort of as Saudi Arabia, the United Arab Emirates, Jordan, Kuwait, Oman, Iraq, and Israel.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Scarred Manticore also exhibits some diploma of overlap with OilRig, yet another Iranian nation-condition crew that was not long ago attributed to an attack on an unnamed Middle East governing administration between February and September 2023 as component of an eight-month-long campaign.

An additional established of tactical overlaps have been discovered in between the adversary and an intrusion established codenamed ShroudedSnooper by Cisco Talos. Attack chains orchestrated by the danger actor have singled out telecom vendors in the Center East utilizing a stealthy backdoor known as HTTPSnoop.
The activity represented by Scarred Manticore is characterised by the use of a formerly unknown passive malware framework referred to as LIONTAIL that’s installed on Windows servers. The risk actor is considered to be active because at the very least 2019.
“Scarred Manticore has been pursuing superior-worth targets for yrs, making use of a range of IIS-based backdoors to attack Windows servers,” Verify Position researchers explained in a Tuesday evaluation. “These involve a wide variety of customized web shells, customized DLL backdoors, and driver-based implants.”
An highly developed piece of malware, LIONTAIL is a assortment of custom shellcode loaders and memory resident shellcode payloads. A noteworthy ingredient of the framework is a light-weight-however-innovative implant composed in C that allows attackers to execute commands remotely by means of HTTP requests.
The attack sequences entail infiltrating publicly struggling with Windows servers to kick off the malware supply method and systematically harvest delicate facts from contaminated hosts.
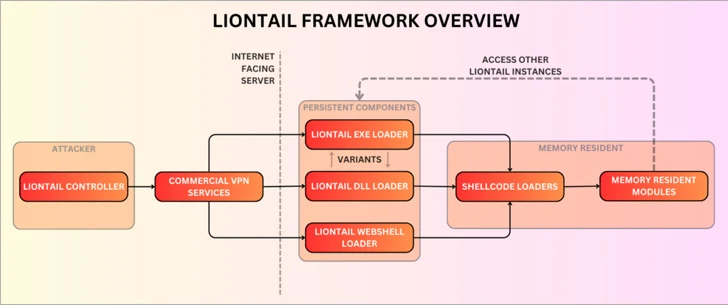
“Instead of making use of the HTTP API, the malware utilizes IOCTLs to interact right with the fundamental HTTP.sys driver,” the scientists claimed, detailing the command-and-command (C2) mechanism.
“This approach is stealthier as it doesn’t involve IIS or HTTP API, which are typically closely monitored by security methods, but is not a clear-cut endeavor given that the IOCTLs for HTTP.sys are undocumented and need further investigate initiatives by the risk actors.”
Also deployed together with LIONTAIL include a variety of web shells and a web forwarder device identified as LIONHEAD, a web forwarder.
Historical exercise of Scarred Manticore implies a continuous evolution of the group’s malware arsenal, what with the menace actor formerly relying on web shells this sort of as Tunna and a bespoke model identified as FOXSHELL for backdoor obtain.

Given that mid-2020, the menace actor is also reported to have utilized a .NET-primarily based passive backdoor referred to as SDD that establishes C2 interaction via an HTTP listener on the contaminated equipment with the final purpose of executing arbitrary commands, uploading and downloading documents, and operating extra .NET assemblies.
The progressive updates to the danger actor’s techniques and resources is typical of innovative persistent risk (APT) teams and demonstrates their means and various skills. This is very best exemplified by Scarred Manticore’s use of a malicious kernel driver identified as WINTAPIX that was uncovered by Fortinet earlier this May possibly.
In a nutshell, WinTapix.sys functions as a loader to execute the upcoming stage of the attack, injecting an embedded shellcode into a acceptable person manner procedure that, in transform, executes an encrypted .NET payload especially designed to concentrate on Microsoft Internet Data Services (IIS) servers.
The focusing on of Israel will come amid the ongoing Israel-Hamas war, prompting low-sophistication hacktivist teams to attack different companies in the place, as effectively as nations like India and Kenya, suggesting country-point out actors’ reliance on information functions aimed at influencing the global perception of the conflict.
“LIONTAIL framework parts share very similar obfuscation and string artifacts with FOXSHELL, SDD backdoor, and WINTAPIX motorists,” Test Issue explained.
“Analyzing the record of their pursuits, it gets evident how far the threat actor has come in strengthening their attacks and maximizing their strategy which depends on passive implants.”
Observed this short article fascinating? Stick to us on Twitter and LinkedIn to examine more distinctive content material we post.
Some components of this write-up are sourced from:
thehackernews.com


 North Korean Hackers Tageting Crypto Experts with KANDYKORN macOS Malware
North Korean Hackers Tageting Crypto Experts with KANDYKORN macOS Malware