The browser has turn into the main work interface in modern day enterprises. It can be where by staff members develop and interact with facts, and how they accessibility organizational and external SaaS and web applications. As a outcome, the browser is thoroughly specific by adversaries. They search for to steal the info it merchants and use it for destructive accessibility to organizational SaaS apps or the hosting equipment. Moreover, unintended details leakage by means of the browser has come to be a critical problem for companies as well.
Nonetheless, conventional endpoint, network, and knowledge defense answers fall short to shield this critical useful resource against advanced web-borne attacks that consistently increase in sophistication and quantity. This gap leaves companies uncovered to phishing attacks, malicious browser extensions, facts publicity, and data reduction.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This is the challenge LayerX is trying to solve. LayerX has designed a secure company browser extension that can be mounted on any browser. The LayerX extension delivers in depth visibility, continual monitoring, and granular policy enforcement on every function in just the browsing session. Employing proprietary Deep Session Analysis technology, LayerX can mitigate browser details reduction threats, prevent credential theft by phishing sites, identify malicious extensions, and substantially a lot more.
In this system assessment, we are going to stroll you by the entire LayerX user journey, from first installation and configuration to visibility and defense. (to get a personalised demo of Layerx, visit their web site here)
First Installation and Set up
LayerX is developed for effortless set up on prime of the organization’s existing browser infrastructure. The user can distribute it through a group policy, any organization product administration system, or the browser’s administration workspace. For the very last solution, LayerX is not installed on the hosting device. As a substitute, it is sent as element of the browser’s profile, building it a all-natural alternative for the safety of unmanaged gadgets. The set up screen enabled the person to pick out the browsers that are in use in their ecosystem.
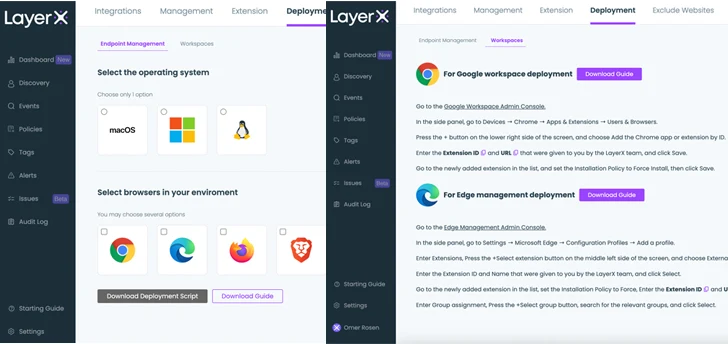 Figure 1: The LayerX installation display screen. Centralized distribution (left), browser administration sign-in (correct)
Figure 1: The LayerX installation display screen. Centralized distribution (left), browser administration sign-in (correct)
The LayerX Dashboard
As soon as the set up is comprehensive, the LayerX dashboard promptly results in being populated with pre-defined procedures, facts on the browsers, consumers, extensions, and web exercise. When the user configures guidelines, the dashboard will show them as perfectly, alongside with their standing, detected risk alerts, and other info aggregations.
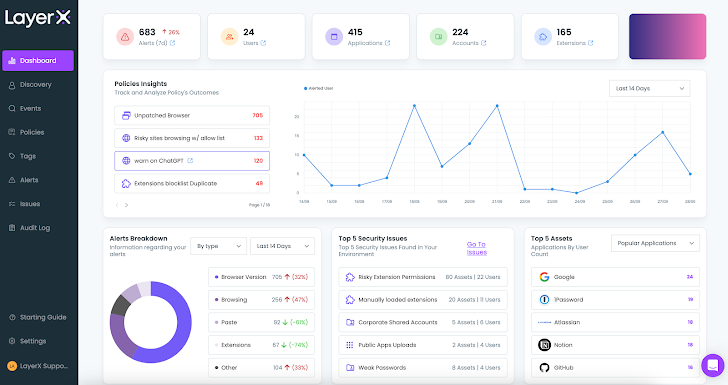 Figure 2: LayerX dashboard
Figure 2: LayerX dashboard
The dashboard gives significant-stage insights into the security posture of the browser ecosystem. For drilling down into particular issues, let’s go on to the Discovery webpage.
Visibility and Discovery of Entities in Searching Sessions
The Discovery website page provides the user with a prosperity of data about five styles of entities:
- Users
- Apps
- Accounts
- Extensions
- Browsers
For example:
- The ‘Apps’ part shows users all the web and SaaS applications the organization’s employees are accessing by their browsers. This involves 100% of the applications in use, irrespective of whether they are sanctioned or private.
- The ‘Accounts’ area reveals the strength of the account’s passwords or any usage of non-company identities. The person also can uncover browsers that are operating out-of-date variations, enforce updates, and acquire visibility into all the unique extensions that are put in on browsers in the ecosystem.
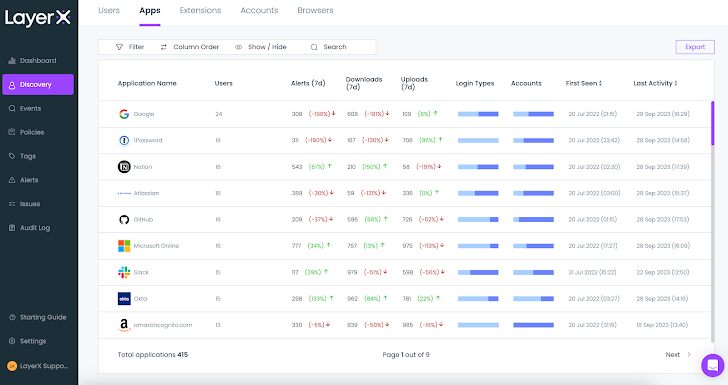 Figure 3: The LayerX Discovery screen, Applications part
Figure 3: The LayerX Discovery screen, Applications part
Proactively Detecting and Resolving Browser Issues
The Discovery process informs the user about several issues, enabling the person to take care of them on the spot. For example, examining the unique extensions may possibly reveal an extension that has critical permissions that could expose it to compromise. In this kind of a case, the extension can simply just be included to a block listing, getting rid of the risk.
Moreover, LayerX presents a dedicated ‘Issues’ tab that aggregates all the results that show a prospective security weak point for each entity kind. For accounts, it could be weak passwords or shared accounts. For purposes, public app uploads or non-SSO corporate applications. And so on.
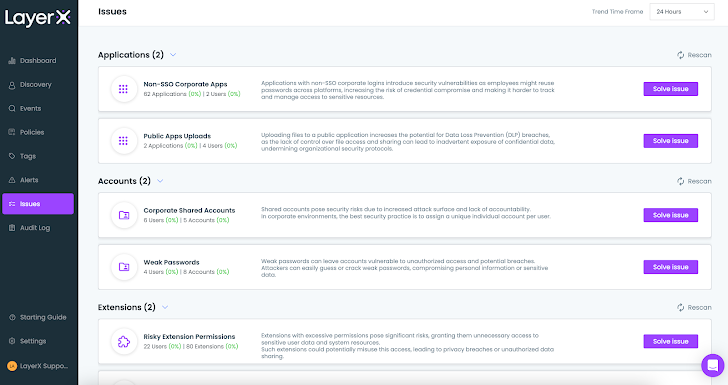 Figure 4: The LayerX Issues display displaying Account and Software issues
Figure 4: The LayerX Issues display displaying Account and Software issues
It is crucial to notice that this is the first time that most of the details shown in the Discovery web page is available for monitoring and examination. Present IT and security products had been not in a position to current it. As such, LayerX addresses a lengthy acknowledged blind place.
Detecting and Resolving Destructive Browser Extensions Risk
One of the most critical and unaddressed threats are destructive browser extensions. These extensions have the energy to compromise browser knowledge, route personnel to malicious web pages, seize session information, and have out numerous other destructive pursuits.
The ‘Extensions’ tab in the Discovery site pinpoints all the extensions that introduce a risk to the atmosphere.
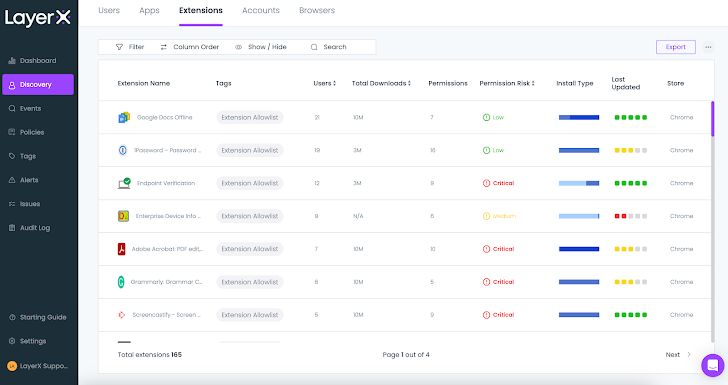 Determine 5: The LayerX Discovery display screen, Extensions tab
Determine 5: The LayerX Discovery display screen, Extensions tab
The ‘Issues’ web page aggregates the risky extensions and delivers a suggestion on how to solve it. This can be done manually or with LayerX’s ‘Automatic Resolve’ possibility.
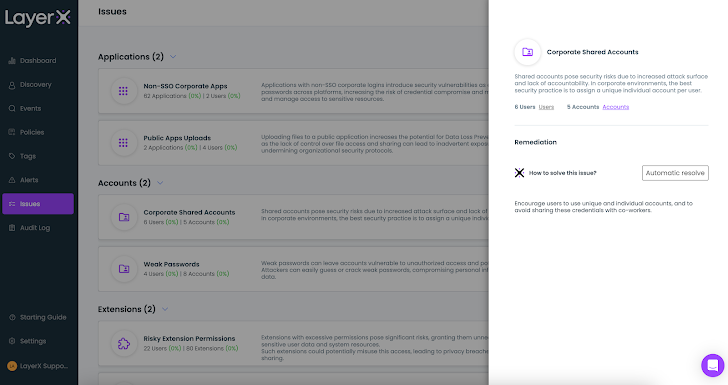 Figure 6: The LayerX Issues display screen displaying guide and automated resolving selections
Figure 6: The LayerX Issues display screen displaying guide and automated resolving selections
Next the discovery and resolution of current risky extensions, the person can proactively mitigate this risk likely forward with a dedicated coverage. Prior to demonstrating how, let us provide insight into LayerX’s coverage configuration function.
LayerX Procedures – How to Address Numerous Browser Security Use Conditions
LayerX insurance policies empower end users to proactively secure from a huge selection of web-borne dangers. Procedures are categorized into distinctive styles (DLP, harmless searching, and so forth.) centered on the risk type they address.
The heart of the policy is the ‘Conditions’ part, in which the consumer decides the disorders that bring about a protecting motion. These circumstances can array from very simple rules to particularly granular combos, enabling laser emphasis enforcement, lower untrue positives and accuracy that are not able to be achieved by other products
Respectively, the ‘Action’ part is also really granular, such as equally straightforward ‘block access’ or ‘prevent upload’ steps, as properly as the skill to surgically disable dangerous elements within just the web web page or pop-up warnings to the searching worker.
LayerX is delivered with a established of default procedures. Buyers can use them as is, modify their ailments and steps, or develop new ones from scratch.
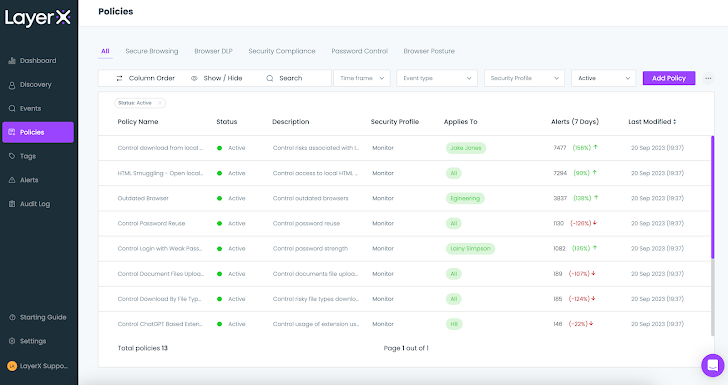 Figure 7: The LayerX Procedures display
Figure 7: The LayerX Procedures display
Let us examine a few insurance policies to illustrate this ability.
A Coverage for Blocking Dangerous Extension Installation
LayerX enables the person to generate a checklist of permitted extensions. This list can then be applied as a affliction parameter to continuously observe and govern this former blind location.
LayerX supplies its people with a large vary of mitigations in opposition to malicious extensions. Customers can outline a blockallow lists to proactively manage which extensions can be put in. In addition LayerX’s granular visibility into all of the extensions’ parts permits buyers to configure policies that can block extensions dependent on their asked for permissions, title, set up form, web retail store and a lot of other people. this is a exclusive functionality that can not be discovered in any endpoint safety or IT administration device.
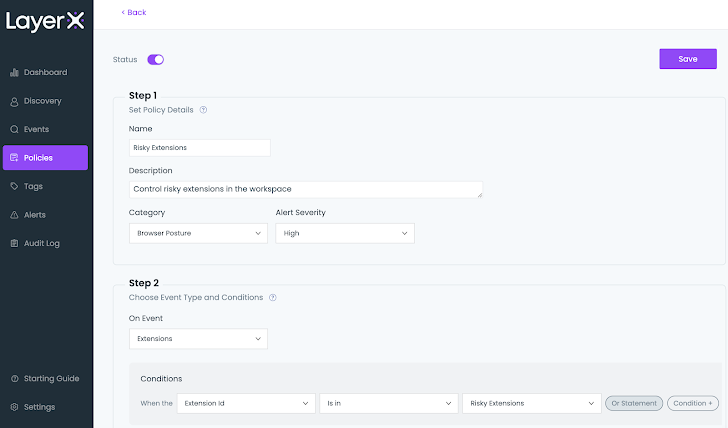 Determine 8: The LayerX Insurance policies monitor, risky extension plan configuration
Determine 8: The LayerX Insurance policies monitor, risky extension plan configuration
The moment activated, any attempt to down load an extension that is not incorporated in the list will result in a protecting motion. The worker will obtain a pop-up informing them that the extension violates the organization’s policy. Based mostly on the motion configured in the coverage, LayerX will either check with the employee to disable the extension or acquire action to automatically deactivate it.
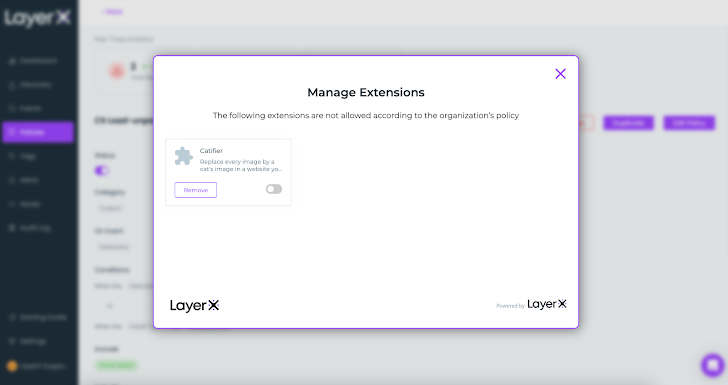 Figure 9: LayerX coverage motion, pop up on dangerous extension installation
Figure 9: LayerX coverage motion, pop up on dangerous extension installation
A Coverage for Preventing Data Leakage through ChatGPT
When ChatGPT is an remarkable efficiency booster, it is critical to ensure that personnel use it in a safe manner and without having exposing delicate knowledge.
The plan underneath demonstrates how this risk can be mitigated. In the ‘Conditions’ part, the consumer defines the focus on web site and which kind of text triggers a protective motion. These original conditions can be refined by incorporating problems that relate to the machine point out (managedunmanaged), the browser type, user id, and a lot more.
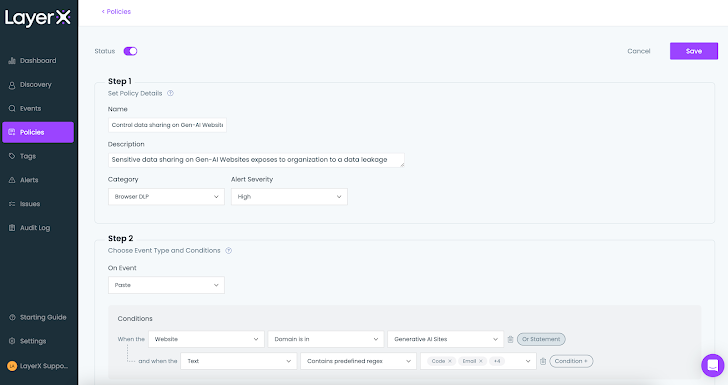 Determine 10: The LayerX policy display screen, setting a ailment throughout policy configuration
Determine 10: The LayerX policy display screen, setting a ailment throughout policy configuration
A policy can induce many actions based on the user’s requirements. The screenshot beneath shows the unique possibilities: checking, popping up an employee warning concept, ‘prevent with bypass’ that enables employees to comprehensive their ChatGPT query pending they can justify it, and the ultimate solution of comprehensive prevention.
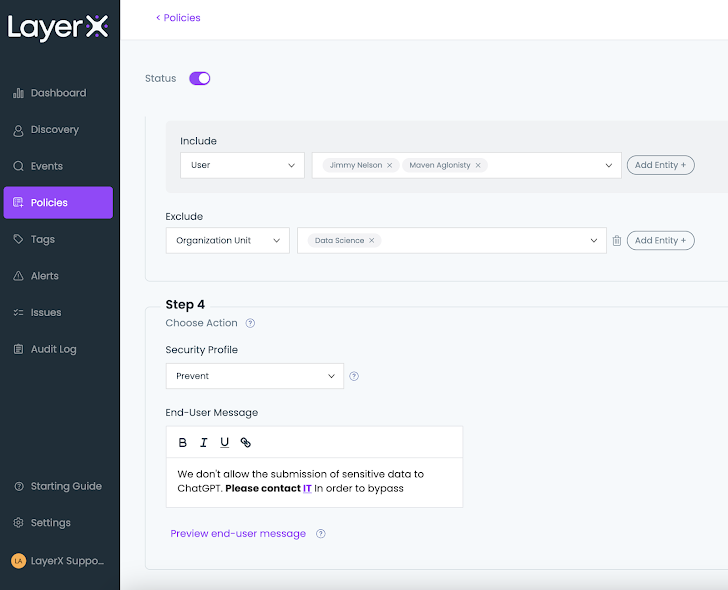 Determine 11: The LayerX policy display screen, setting an action all through coverage configuration
Determine 11: The LayerX policy display screen, setting an action all through coverage configuration
After the plan is configured and enabled, buyers can even now use ChatGPT freely, except delicate details is topic to leakage risk. Any violation of the conditions defined in the plan will trigger the configured defense, as effectively an alert that notifies the admin of the violation and its facts:
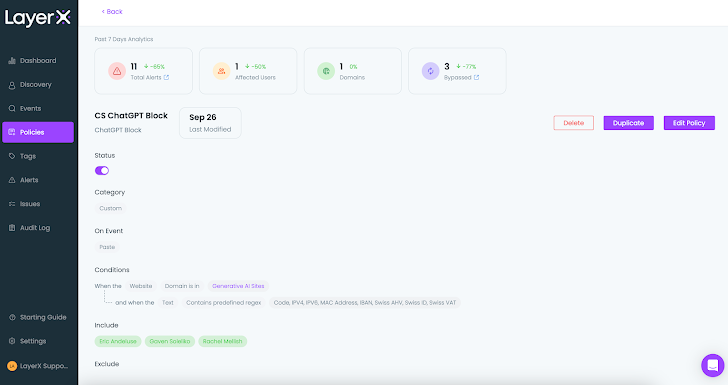 Figure 12: LayerX coverage monitor, a one coverage web page
Figure 12: LayerX coverage monitor, a one coverage web page
A further critical issue LayerX policies allow resolving is Shadow Id. This risk surfaces generally inside sanctioned apps. Suppose the user’s business is applying Google Suite, with personnel accessing it with a company identification. Nevertheless, they also have a particular Google account that introduces a details leakage risk if an worker unintentionally uploads data files with delicate details to their individual drive or email somewhat than to the corporate one particular.
To resolve this obstacle, LayerX permits end users to configure policies that are delicate to the employee’s identity and increase the identity as a problem, jointly with file articles, labeling, and other common DLP attributes. At the time enabled, the policy stops uploading of corporate facts to Google, except if it can be accessed by the user’s company account.
Hardening Defense Against Account Takeover with LayerX as an Extra authentication Factor
LayerX can be integrated with the environment’s cloud Id Company (IdP). In that way, accessibility to the SaaS applications the IDP manages is feasible only from a browser on which the extension is set up. For example, when accessing a SaaS app by way of Okta with no LayerX on the browser, an alert concept is brought on:
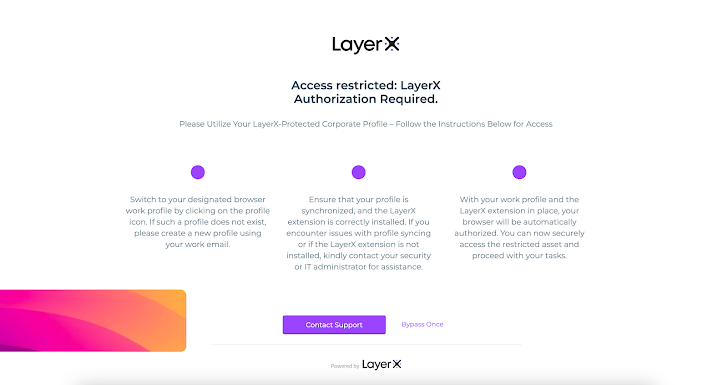 Determine 13: The LayerX obtain restriction pop-up
Determine 13: The LayerX obtain restriction pop-up
LayerX serves in this article as an MFA, but without the need of the intrusive user working experience of the push notification to the employee’s phone. This serves as incredibly powerful mitigation towards malicious obtain that exploits compromised qualifications, due to the fact adversaries will under no circumstances get obtain to SaaS and web methods centered on qualifications by itself.
Checking the Web-borne Threats Landscape from the Alerts Screen
The final LayerX display screen in this overview is the Alerts screen. Every single brought on coverage registers an notify. The Alerts display screen classifies and aggregates the alert by severity (lower, medium, higher, critical) and variety (paste, safe and sound searching, and so forth.), and displays the prime activated insurance policies.
The consumer can use the a variety of filters to look at only alerts inside of a sure timeframe, type, motion variety, or risk level.
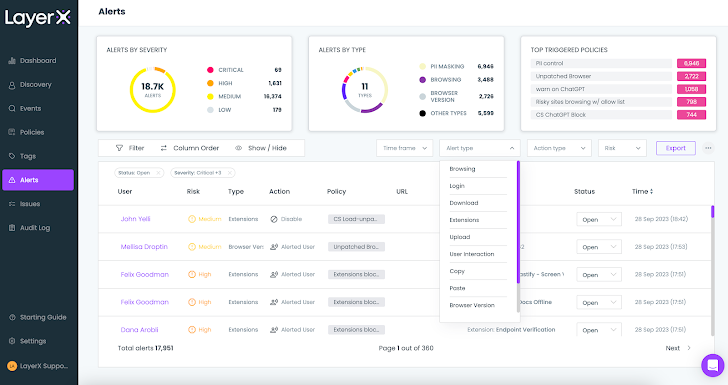 Figure 14: The LayerX accessibility Alerts screen with the Warn Style dropdown
Figure 14: The LayerX accessibility Alerts screen with the Warn Style dropdown
For instance, filtering for the ‘Upload’ variety will present all the policies that had been activated by staff members who uploaded files in an insecure manner. Clicking on ‘Investigate’ reveals the employees’ browsing path and the actual position within just the session that violated the policy.
For illustration, the following celebration journey for a data upload policy reveals that the staff uploaded a file to their personalized Gmail and then switched back again to their perform account. Detecting and blocking this kind of an party is a unique ability that won’t be able to be performed by any CASB or other software-oriented security tool, due to the fact they deficiency the capacity to differentiate among accounts for the same application.
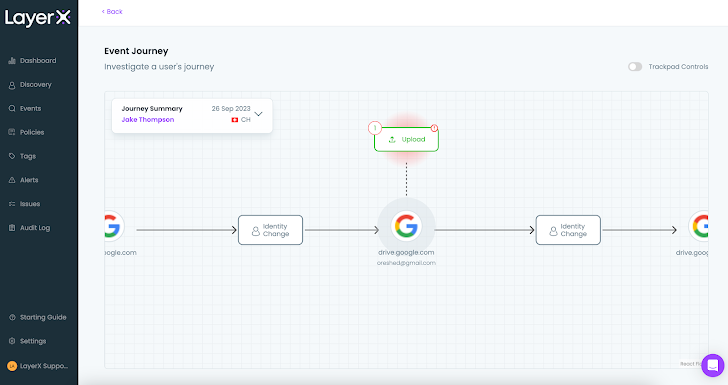 Figure 15: The celebration journey for a induced DLP plan
Figure 15: The celebration journey for a induced DLP plan
Conclusion
The LayerX protected browser extension consolidates protection measures for the complete range of web-borne challenges. Some of these risks are partially dealt with by existing methods, although most were being a comprehensive blind spot, till now.
For corporations that admit the centrality of the browser in their operations, LayerX is an priceless answer, giving a one pane of glass for all the functionalities that mitigate each browser-centered attacks and web-linked data decline.
Check out the LayerX web-site listed here.
Located this article attention-grabbing? Comply with us on Twitter and LinkedIn to go through a lot more special content material we post.
Some pieces of this short article are sourced from:
thehackernews.com

 Iranian Cyber Espionage Group Targets Financial and Government Sectors in Middle East
Iranian Cyber Espionage Group Targets Financial and Government Sectors in Middle East