An Iranian-joined threat actor identified as Rocket Kitten has been noticed actively exploiting a not too long ago patched VMware vulnerability to attain first accessibility and deploy the Main Impact penetration tests tool on susceptible systems.
Tracked as CVE-2022-22954 (CVSS rating: 9.8), the critical issue considerations a situation of remote code execution (RCE) vulnerability impacting VMware Workspace Just one Entry and Id Manager.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Even though the issue was patched by the virtualization providers supplier on April 6, 2022, the organization cautioned buyers of verified exploitation of the flaw transpiring in the wild a 7 days later on.
“A destructive actor exploiting this RCE vulnerability potentially gains an unlimited attack surface,” scientists from Morphisec Labs mentioned in a new report. “This implies greatest privileged obtain into any components of the virtualized host and guest ecosystem.”
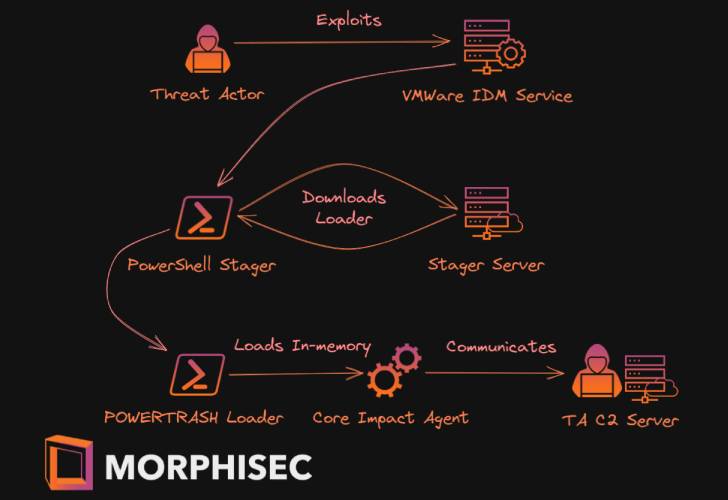
Attack chains exploiting the flaw involve the distribution of a PowerShell-centered stager, which is then employed to down load a following-stage payload called PowerTrash Loader that, in convert, injects the penetration testing tool, Core Affect, into memory for observe-on actions.

“The prevalent use of VMWare identity obtain management blended with the unfettered distant obtain this attack presents is a recipe for devastating breaches throughout industries,” the researchers said.
“VMWare buyers ought to also assessment their VMware architecture to be certain the influenced parts are not unintentionally posted on the internet, which dramatically increases the exploitation risks.”
Discovered this write-up attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to read extra unique written content we article.
Some sections of this short article are sourced from:
thehackernews.com


 Researchers Report Critical RCE Vulnerability in Google’s VirusTotal Platform
Researchers Report Critical RCE Vulnerability in Google’s VirusTotal Platform