Security scientists have disclosed a security vulnerability in the VirusTotal system that could have been potentially weaponized to obtain remote code execution (RCE).
The flaw, now patched, made it doable to “execute instructions remotely within just VirusTotal system and attain obtain to its several scans abilities,” Cysource scientists Shai Alfasi and Marlon Fabiano da Silva mentioned in a report exclusively shared with The Hacker Information.
VirusTotal, component of Google’s Chronicle security subsidiary, is a malware-scanning support that analyzes suspicious data files and URLs and checks for viruses working with far more than 70 3rd-party antivirus products.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The attack technique included the add of a DjVu file by way of the platform’s web consumer interface, using it to result in an exploit for a higher-severity remote code execution flaw in ExifTool, an open-supply utility employed to go through and edit EXIF metadata information in impression and PDF files.
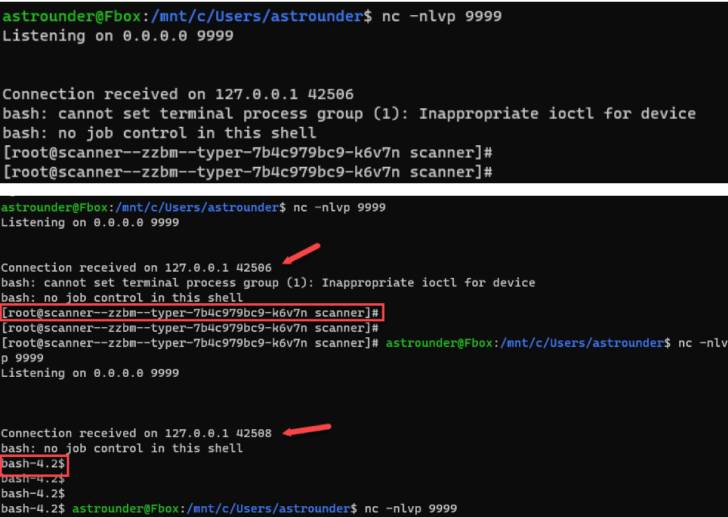
Tracked as CVE-2021-22204 (CVSS score: 7.8), the superior-severity vulnerability in problem is a scenario of arbitrary code execution that occurs from ExifTool’s mishandling of DjVu data files. The issue was patched by its maintainers in a security update launched on April 13, 2021.
A consequence of this kind of an exploitation, the researchers observed, was that it granted accessibility to not only a Google-controlled surroundings, but also to additional than 50 interior hosts with substantial-level privileges.
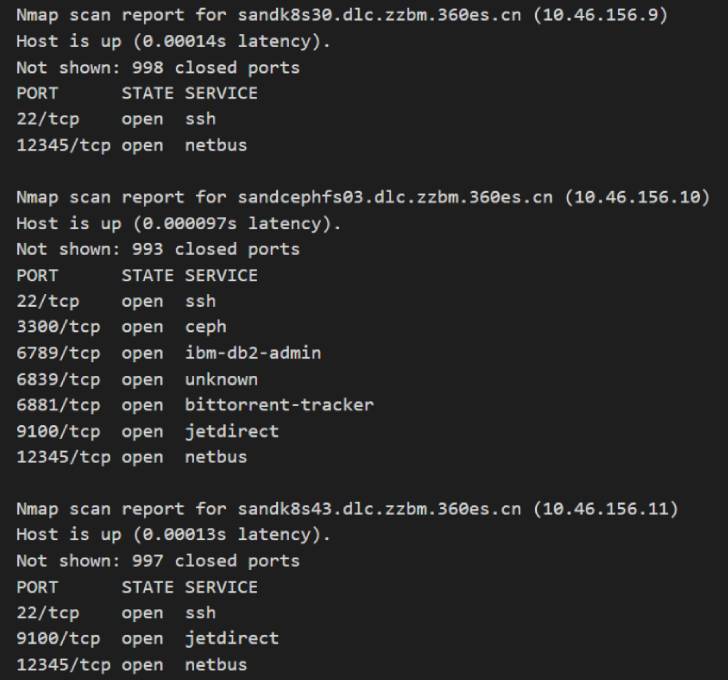
“The exciting element is every time we uploaded a file with a new hash containing a new payload, VirusTotal forwarded the payload to other hosts,” the researchers claimed. “So, not just we experienced an RCE, but also it was forwarded by Google’s servers to Google’s internal network, its clients, and associates.”

Cysource mentioned it responsibly documented the bug by way of Google Vulnerability Reward Plans (VRP) on April 30, 2021, next which the security weak spot was right away rectified.
This is not the initial time the ExifTool flaw emerged as a conduit to attain remote code execution. Past year, GitLab preset a critical flaw (CVE-2021-22205, CVSS score: 10.) connected to an inappropriate validation of person-delivered pictures, leading to arbitrary code execution.
Found this write-up interesting? Abide by THN on Fb, Twitter and LinkedIn to browse far more exceptional content material we article.
Some areas of this article are sourced from:
thehackernews.com


 Kansas Hospital Discloses Data Breach
Kansas Hospital Discloses Data Breach