An Iranian nation-point out threat actor has been joined to a new wave of phishing attacks concentrating on Israel that’s made to deploy an up to date edition of a backdoor identified as PowerLess.
Cybersecurity agency Check Place is monitoring the exercise cluster under its mythical creature manage Educated Manticore, which displays “sturdy overlaps” with a hacking crew regarded as APT35, Charming Kitten, Cobalt Illusion, ITG18, Mint Sandstorm (formerly Phosphorus), TA453, and Yellow Garuda.
“Like a lot of other actors, Educated Manticore has adopted recent tendencies and started applying ISO photographs and quite possibly other archive data files to initiate an infection chains,” the Israeli corporation mentioned in a technical report posted nowadays.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Lively due to the fact at least 2011, APT35 has forged a huge net of targets by leveraging faux social media personas, spear-phishing tactics, and N-working day vulnerabilities in internet-exposed purposes to get preliminary accessibility and drop various payloads, such as ransomware.
The improvement is an indicator that the adversary is continuously refining and retooling its malware arsenal to grow their operation and resist assessment efforts, when also adopting increased solutions to evade detection.
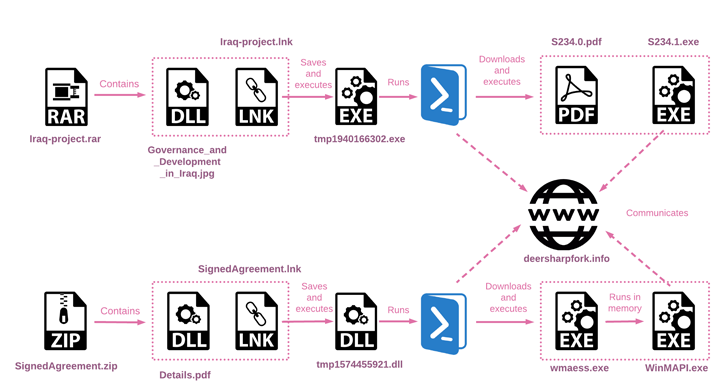
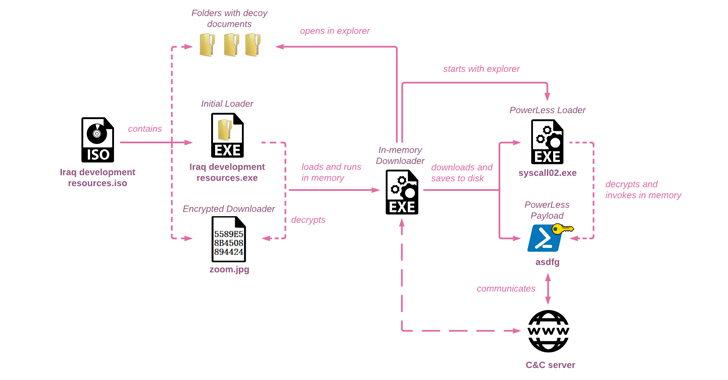
The attack chain documented by Verify Place begins with an ISO disk impression file that tends to make use of Iraq-themed lures to drop a customized in-memory downloader that ultimately launches the PowerLess implant.
The ISO file functions as a conduit to exhibit a decoy document published in Arabic, English, and Hebrew, and purports to function educational material about Iraq from a legit non-income entity identified as the Arab Science and Technology Foundation (ASTF), indicating that the investigation local community may perhaps have been the target of the campaign.
The PowerLess backdoor, formerly spotlighted by Cybereason in February 2022, will come with abilities to steal data from web browsers and applications like Telegram, acquire screenshots, report audio, and log keystrokes.
“While the new PowerLess payload continues to be identical, its loading mechanisms have drastically enhanced, adopting strategies seldom noticed in the wild, these kinds of as applying .NET binary documents created in combined method with assembly code,” Verify Issue said.
“PowerLess [command-and-control] communication to the server is Foundation64-encoded and encrypted after obtaining a important from the server. To mislead researchers, the danger actor actively adds three random letters at the beginning of the encoded blob.”
Future WEBINARZero Believe in + Deception: Understand How to Outsmart Attackers!
Uncover how Deception can detect sophisticated threats, halt lateral motion, and increase your Zero Have faith in strategy. Join our insightful webinar!
Save My Seat!
The cybersecurity business mentioned it also discovered two other archive files made use of as element of a various intrusion established that shares overlaps with the aforementioned attack sequence owing to the use of the very same Iraq-themed PDF file.
More assessment has discovered that the an infection chains arising from these two archive documents culminate in the execution of a PowerShell script that’s engineered to down load two files from a remote server and operate them.
“Educated Manticore continues to evolve, refining earlier observed toolsets and offering mechanisms,” Test Issue reported, including “the actor adopts common developments to stay away from detection” and retains “establishing personalized toolsets making use of superior strategies.”
“Mainly because it is an current edition of formerly reported malware, […] it is crucial to be aware that it may well only signify the early levels of infection, with major fractions of submit-an infection action yet to be seen in the wild.”
Located this report intriguing? Abide by us on Twitter and LinkedIn to examine more special content we submit.
Some areas of this write-up are sourced from:
thehackernews.com

 Modernizing Vulnerability Management: The Move Toward Exposure Management
Modernizing Vulnerability Management: The Move Toward Exposure Management