Large-profile persons doing the job on Middle Jap affairs at universities and research corporations in Belgium, France, Gaza, Israel, the U.K., and the U.S. have been targeted by an Iranian cyber espionage group termed Intellect Sandstorm due to the fact November 2023.
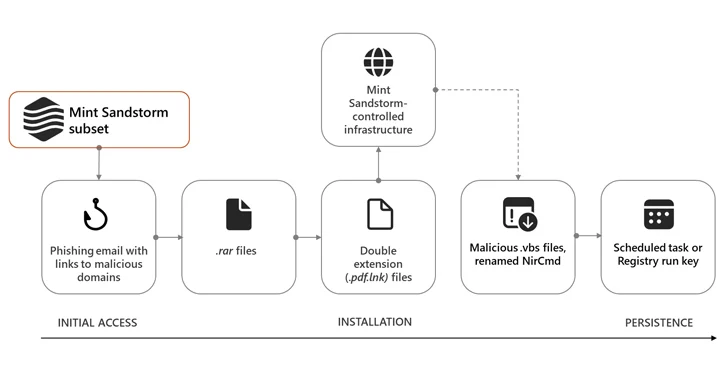
The risk actor “used bespoke phishing lures in an attempt to socially engineer targets into downloading destructive data files,” the Microsoft Threat Intelligence staff explained in a Wednesday evaluation, describing it as a “technically and operationally mature subgroup of Mind Sandstorm.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attacks, in pick conditions, entail the use of a previously undocumented backdoor dubbed MediaPl, indicating ongoing endeavors by Iranian threat actors to refine their article-intrusion tradecraft.
Mint Sandstorm, also recognized as APT35, Charming Kitten, TA453, and Yellow Garuda, is identified for its adept social engineering campaigns, even resorting to legit but compromised accounts to send bespoke phishing e-mail to possible targets. It is assessed to be affiliated with Iran’s Islamic Innovative Guard Corps (IRGC).

The sub-cluster, per Redmond, engages in useful resource-intensive social engineering to solitary out journalists, researchers, professors, and other folks with insights on security and policy issues of desire to Tehran.
The most current intrusion set is characterized by the use of lures pertaining to the Israel-Hamas war, sending innocuous e-mail beneath the guise of journalists and other significant-profile persons to construct rapport with targets and set up a amount of have confidence in prior to making an attempt to supply malware to targets.
Microsoft stated it really is likely the campaign is an work undertaken by the nation-condition risk actor to gather perspectives on gatherings linked to the war.
The use of breached accounts belonging to the people today they sought to impersonate in order to send the email messages is a new Head Sandstorm tactic not seen in advance of, as is its use of the curl command to link to the command-and-handle (C2) infrastructure.
Need to the targets have interaction with the menace actor, they are despatched a observe-up email made up of a destructive connection that points to a RAR archive file, which, when opened, prospects to the retrieval of Visual Simple scripts from the C2 server to persist within the targets’ environments.
The attack chains further more pave the way for tailor made implants like MischiefTut or MediaPl, the previous of which was initially disclosed by Microsoft in October 2023.
Implemented in PowerShell, MischiefTut is a simple backdoor that can run reconnaissance commands, write outputs to a text file, and download more instruments on a compromised technique. The initial recorded use of the malware dates again to late 2022.
MediaPl, on the other hand, masquerades as Windows Media Participant and is designed to transmit encrypted communications to its C2 server and start command(s) it has acquired from the server.

“Mint Sandstorm carries on to boost and modify the tooling employed in targets’ environments, activity that could possibly help the team persist in a compromised setting and far better evade detection,” Microsoft stated.
“The capability to attain and maintain distant accessibility to a target’s technique can permit Mint Sandstorm to carry out a assortment of activities that can adversely impact the confidentiality of a method.”
The disclosure arrives as Dutch newspaper De Volkskrant uncovered before this month that Erik van Sabben, a Dutch engineer recruited by Israel and U.S. intelligence providers, may perhaps have applied a h2o pump to deploy an early variant of the now-notorious Stuxnet malware in an Iranian nuclear facility sometime in 2007.
Discovered this write-up exciting? Observe us on Twitter and LinkedIn to read more unique content we put up.
Some areas of this report are sourced from:
thehackernews.com

 PAX PoS Terminal Flaw Could Allow Attackers to Tamper with Transactions
PAX PoS Terminal Flaw Could Allow Attackers to Tamper with Transactions