The Iranian point out-sponsored danger actor recognized as OilRig deployed 3 distinctive downloader malware all through 2022 to maintain persistent obtain to sufferer companies situated in Israel.
The 3 new downloaders have been named ODAgent, OilCheck, and OilBooster by Slovak cybersecurity firm ESET. The attacks also associated the use of an updated version of a regarded OilRig downloader dubbed SampleCheck5000 (or SC5k).
“These lightweight downloaders […] are noteworthy for employing a person of a number of respectable cloud provider APIs for [command-and-control] conversation and info exfiltration: the Microsoft Graph OneDrive or Outlook APIs, and the Microsoft Business office Trade Web Services (EWS) API,” security scientists Zuzana Hromcová and Adam Burgher mentioned in a report shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
By applying properly-acknowledged cloud support suppliers for command-and-management interaction, the aim is to mix with reliable network traffic and cover up the group’s attack infrastructure.
Some of the targets of the campaign consist of an organization in the health care sector, a manufacturing organization, and a neighborhood governmental group, between some others. All the victims are stated to have been earlier specific by the menace actor.
Forthcoming WEBINAR Beat AI-Powered Threats with Zero Have confidence in – Webinar for Security Experts
Standard security steps will not minimize it in present day earth. It’s time for Zero Have faith in Security. Safe your facts like in no way right before.
Be a part of Now
The exact first entry vector employed to compromise the targets is at present unclear and it is really not known if the attackers managed to keep their foothold in the networks so as to deploy these downloaders at different details of time in 2022.
OilRig, also identified as APT34, Crambus, Cobalt Gypsy, Hazel Sandstorm (previously EUROPIUM), and Helix Kitten, is an Iranian cyber espionage team which is acknowledged to be lively considering the fact that at minimum 2014, applying a extensive array of malware at its disposal to concentrate on entities in the Middle East.

This 12 months by yourself, the hacking crew has been observed leveraging novel malware like MrPerfectionManager, PowerExchange, Solar, Mango, and Menorah.
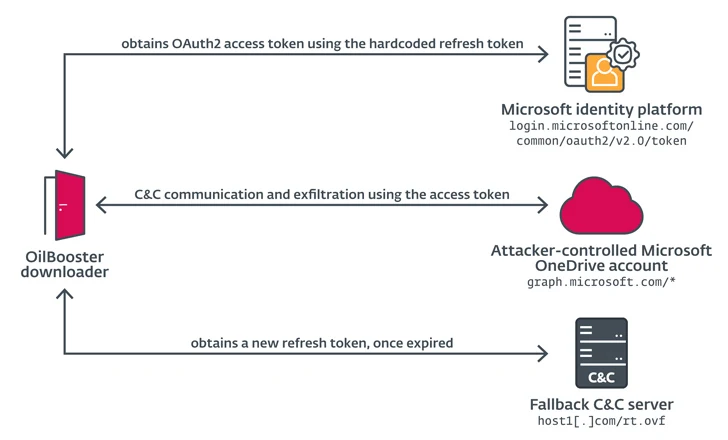
ODAgent, initial detected in February 2022, is a C#/.NET downloader that utilizes Microsoft OneDrive API for command-and-command (C2) communications, permitting the menace actor to down load and execute payloads, and exfiltrate staged files.
SampleCheck5000, on the other hand, is made to interact with a shared Microsoft Exchange mail account to obtain and execute further OilRig tools working with the Office Trade Web Products and services (EWS) API.
OilBooster, in the identical way as ODAgent, makes use of Microsoft OneDrive API for C2, while OilCheck adopts the exact approach as SampleCheck5000 to extract instructions embedded in draft messages. But as an alternative of employing the EWS API, it leverages Microsoft Graph API for network communications.

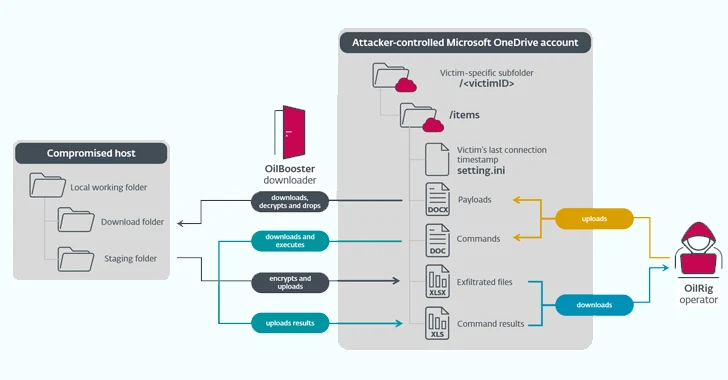
OilBooster is also identical to OilCheck in that it employs the Microsoft Graph API to join to a Microsoft Business office 365 account. What’s different this time around is that the API is utilized to interact with an actor-managed OneDrive account as opposed to an Outlook account in get to fetch instructions and payloads from target-precise folders.
These equipment also share similarities with MrPerfectionManager and PowerExchange backdoors when it will come to making use of email-centered C2 protocols to exfiltrate facts, despite the fact that in the case of the latter, the victimized organization’s Trade Server is made use of to mail messages to the attacker’s email account.
“In all situations, the downloaders use a shared (email or cloud storage) OilRig-operated account to exchange messages with the OilRig operators the exact same account is usually shared by various victims,” the scientists explained.
“The downloaders entry this account to down load commands and added payloads staged by the operators, and to add command output and staged files.”
Discovered this post appealing? Observe us on Twitter and LinkedIn to examine far more distinctive information we write-up.
Some sections of this report are sourced from:
thehackernews.com

 Reimagining Network Pentesting With Automation
Reimagining Network Pentesting With Automation