Menace actors making use of hacking instruments from an Israeli surveillanceware seller named QuaDream specific at the very least five associates of civil modern society in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
According to conclusions from a group of researchers from the Citizen Lab, the adware marketing campaign was directed from journalists, political opposition figures, and an NGO worker in 2021. The names of the victims were being not disclosed.
It can be also suspected that the enterprise abused a zero-click exploit dubbed ENDOFDAYS in iOS 14 to deploy spy ware as a zero-working day in model 14.4 and 14.4.2. There is no evidence that the exploit has been applied right after March 2021.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
ENDOFDAYS “appears to make use of invisible iCloud calendar invitations despatched from the spyware’s operator to victims,” the scientists mentioned.
The Microsoft Menace Intelligence team is tracking QuaDream as DEV-0196, describing the cyber mercenary enterprise as a non-public sector offensive actor (PSOA). Even though QuaDream is not directly concerned in focusing on, it is identified to market its “exploitation providers and malware” to authorities shoppers, the tech huge assessed with substantial self esteem.
The malware, named KingsPawn, is made up of a observe agent and the main malware agent, both equally of which are Mach-O documents written in Objective-C and Go, respectively.
Even though the keep an eye on agent is dependable for lowering the forensic footprint of the malware to evade detection, the key agent arrives with capabilities to get gadget facts, cellular and Wi-Fi details, harvest data files, obtain camera in the track record, access site, phone logs, and iOS Keychain, and even crank out an iCloud time-centered just one-time password (TOTP).
Other samples help recording audio from phone phone calls and the microphone, managing queries in SQL databases, and cleaning up forensic trails, this sort of as deleting all calendar activities from two several years prior to the current time. The info is exfiltrated through HTTPS Publish requests.
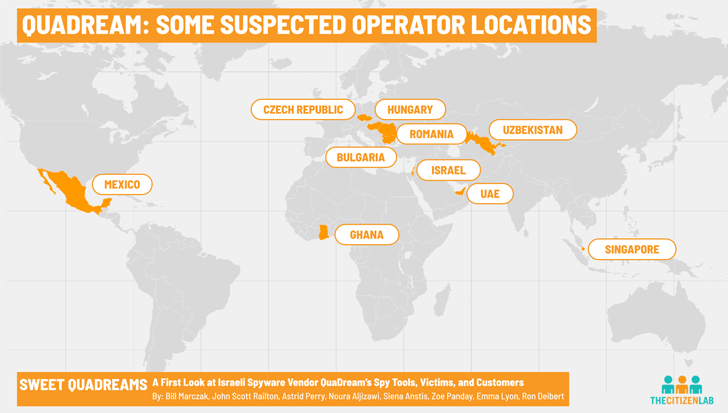
Internet scans carried out by the Citizen Lab reveal that QuaDream’s buyers operated 600 servers from numerous nations around the world all around the world involving late 2021 and early 2023, together with Bulgaria, Czech Republic, Hungary, Romania, Ghana, Israel, Mexico, Singapore, the U.A.E., and Uzbekistan.
Even with makes an attempt created by the spyware to cover its tracks, the interdisciplinary laboratory claimed it was equipped to uncover unspecified traces of what it phone calls the “Ectoplasm Factor” that could be employed to track QuaDream’s toolset in the upcoming.
This is not the initial time QuaDream has captivated notice. In February 2022, Reuters described that the company weaponized the FORCEDENTRY zero-click exploit in iMessage to deploy a spyware option named REIGN.
Then in December 2022, Meta disclosed that it took down a network of 250 phony accounts on Fb and Instagram controlled by QuaDream to infect Android and iOS units and exfiltrate individual knowledge.
Approaching WEBINARLearn to Protected the Identity Perimeter – Confirmed Methods
Strengthen your organization security with our forthcoming qualified-led cybersecurity webinar: Discover Identity Perimeter tactics!
Do not Miss out on Out – Help you save Your Seat!
If something, the enhancement is however one more indication that in spite of the notoriety attracted by NSO Team, commercial spy ware corporations proceed to fly under the radar and build subtle spyware solutions for use by govt shoppers.
“Until the out-of-control proliferation of commercial spyware is efficiently curtailed through systemic government polices, the quantity of abuse situations is probably to carry on to mature, fueled the two by businesses with recognizable names, as properly as some others nevertheless functioning in the shadows,” the Citizen Lab explained.
Contacting the advancement of mercenary spyware companies as a risk to democracy and human legal rights, Microsoft reported combating these kinds of offensive actors needs a “collective energy” and a “multistakeholder collaboration.”
“Furthermore, it is only a make any difference of time right before the use of the tools and technologies they sell spread even even further,” Amy Hogan-Burney, the firm’s associate standard counsel for cybersecurity policy and safety, mentioned.
“This poses real risk to human rights on line, but also to the security and steadiness of the broader online natural environment. The companies they offer have to have cyber mercenaries to stockpile vulnerabilities and search for new approaches to entry networks with no authorization.”
Found this report interesting? Follow us on Twitter and LinkedIn to read a lot more special information we put up.
Some areas of this short article are sourced from:
thehackernews.com


 The Service Accounts Challenge: Can’t See or Secure Them Until It’s Too Late
The Service Accounts Challenge: Can’t See or Secure Them Until It’s Too Late