Here is a hard question to answer: ‘How several support accounts do you have in your ecosystem?’. A more challenging one is: ‘Do you know what these accounts are carrying out?’. And the most difficult is likely: ‘If any of your provider account was compromised and applied to access methods would you be ready to detect and prevent that in real-time?’.
Since most identification and security groups would deliver a negative reply, it’s no surprise that one particular of the quick actions present day attackers are carrying out subsequent an initial endpoint compromised is looking down unwatched services accounts. And it is even fewer of a marvel that in most conditions, they would thrive in finding one and leveraging it to unfold inside of the overall natural environment, getting found only when it is way too late – immediately after workstations and server acquired encrypted by ransomware or sensitive data was stolen.
In this write-up, we unfold the factors that have triggered provider accounts to become 1 of the most risky weaknesses in an Energetic Directory surroundings, clarify how this weak spot power fuels ransomware attacks, and eventually, get to know how Silverfort’s unified id security platform allows corporations to conquer what was till now an insolvable security challenge.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Company Accounts: User Accounts That Are Not Related With Any True Human being And Are Utilized For Device-To-Machine Interaction
Person accounts are just one of the vital making blocks in the business surroundings. Intuitively, we associate person accounts with actual people today. Nonetheless, there are also person accounts that are not related with any human remaining. These accounts are established for equipment-to-machine interaction, automation of repetitive tasks, and other assignments that are intended to just take area in the background without the need of human intervention. They are normally regarded as ‘service accounts’ and aside from their dissociation from a serious individual, are equivalent in all facets to the other, ‘people-associated’ user accounts.
These services accounts are established in two major techniques. The first, is an IT personnel that establishes that a certain cleanliness, checking, or any other undertaking would be better accomplished in an automated fashion, rather than handbook way. The second, is in the program of setting up an company computer software on-prem. In that scenario, some provider accounts are designed for each the instruction of the particular application – in the study course of the set up itself – and are tasked with scanning, distributing updates and similar upkeep assignments.
Company Account Security Problems: Invisible, Really Privileged, And Incredibly Challenging To Protect
Let’s comprehend what tends to make services accounts an unattended attack floor:
- Lack of visibility: As peculiar as it could audio, there is no utility in the identity infrastructure that can immediately filter out services accounts from the overall pool of customers. Nor is there any automated documentation procedure in put that suggests a service account’s development.
- Significant access privileges: Given that service accounts are developed for machine-to-device interaction, it goes without expressing that they should have the needed privileges to accessibility all these equipment, indicating that they are an administrative consumer, no different than any IT admin.
- No PAM defense: The common practice is to safe administrative accounts by inserting them in a PAM solution’s vault and rotate their passwords. On the other hand, this technique can’t be applied to provider accounts since their passwords are hardcoded in the scripts that operate their jobs. As these kinds of, any password rotation would invalidate the password in the scripts, protecting against the provider account from accessing its concentrate on source, and subsequently crack any method that relies on the services accounts’ activity.
4 Steps For Extensive Support Account Security
There are countless support accounts in any specified firm. These accounts can turn into higher-risk belongings that, if remaining unchecked, may well enable threats to propagate throughout the network undetected. Test out this Ebook to discover 4 easy techniques to support continue to keep your assistance accounts secure.
Download E book
How Attackers Leverage The Lower-Hanging Fruit Of Services Accounts For Lateral Movement And Ransomware Distribute
Let’s think that a ransomware actor has properly compromised an endpoint (workstation or server are the exact for that issue). This, of training course, is just the to start with action. The following move is to start out scanning the ecosystem to uncover consumer accounts to compromise that would permit the adversary to laterally transfer within the atmosphere and plant the ransomware payload in as several machines as probable.
But what account to pick? The adversary needs an account which is privileged more than enough to accessibility other servers and workstations. But it really should also be an account that can be made use of beneath the radar devoid of drawing unwanted focus.
This is why service accounts are the greatest compromise focus on. Attackers know that there is certainly a excellent opportunity, that no one is looking on this account, or even much better – that no person even understands that this account exists. It may possibly have been designed decades back by an admin that has because remaining the business with out bothering to delete the assistance accounts he produced.
Support Account Attack Case in point #1: Ransomware Attack Pattern Making use of Compromised Microsoft Exchange Server’s Services Account
The diagram below exhibits a sample attack – 1 of numerous we’ve analyzed in the the latest 12 months – in which the adversary has used a compromised Trade Server’s provider account for the initial aspect its lateral movement, adopted by an more compromise of an admin credentials.
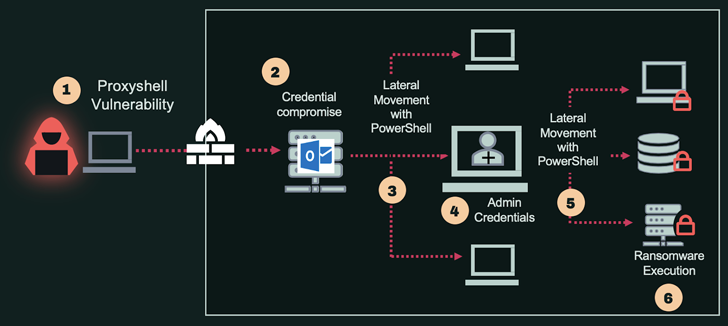
See the facts of just about every phase below:
Company Account Attack Example #2: Lateral Movement in Uber’s Hybrid Atmosphere
The popular attack on Uber that took spot a couple of months back included a substantial use of compromise and use of services account. In that circumstance, it was a services account that has entry to the PAM in place. The attackers found the script with the service account qualifications in a shared network travel and utilized it to extract passwords to multiple sources from the PAM’s vault.
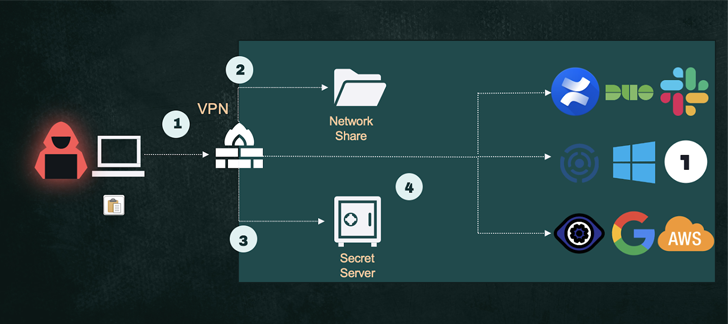
See the aspects of each individual stage below:
Silverfort Automated Discovery, Checking And Security For Company Accounts
Silverfort’s unified id safety system is the 1st resolution that entirely automates the security lifecycle of support account with in the vicinity of-zero effort from the user’s aspect:
Discovery of all provider accounts and mapping of their action
Silverfort’s native integration with Energetic Directory permits it to assess each and every incoming authentication and accessibility endeavor of all person accounts, and very easily detect if an account functions the predictable and repetitive conduct that differentiates provider accounts from conventional customers. Dependent on this analysis, Silverfort generates an output of all the company accounts in the natural environment. What’s more, this discovery goes past just a listing of accounts to also show the account’s privileges, it really is sources and destinations, activity stage and other behavioral attributes.
Continuous risk investigation to disclose if a assistance account displays indications of compromise
Silverfort identifies the baseline habits of just about every support account and repeatedly displays its activity. For a services account, the clearest indicator of compromise is a deviation from its fastened actions, so every time a deviation occurs – these as accessing a new workstation or server, or out of the blue increasing the action quantity – Silverfort’s engine will elevate the account’s risk score.
Lively security with auto-created insurance policies, activated in a one simply click
Silverfort automates the development of an access plan for each and every of the assistance accounts it discovers. This coverage is activated each time the service account deviates from its usual actions (as earlier described) or when its risk degree elevated thanks to detected id threats (Move-the-Hash, Kerberoasting, Move-the-Ticket etc.). The policy can cause both an warn or genuine blocking of the services account access, per the user’s configuration. The only interaction required from the consumer side is click the plan activation button.
Searching for a way to protected your service accounts? Plan a contact with just one of our authorities to learn how Silverfort can help.
Identified this short article exciting? Follow us on Twitter and LinkedIn to read through more distinctive content material we publish.
Some parts of this post are sourced from:
thehackernews.com

 Researchers Uncover 7000 Malicious Open Source Packages
Researchers Uncover 7000 Malicious Open Source Packages