A new malware campaign has been observed concentrating on Italy with phishing emails built to deploy an facts stealer on compromised Windows methods.
“The data-stealer malware steals sensitive information like technique information, crypto wallet and browser histories, cookies, and credentials of crypto wallets from target devices,” Uptycs security researcher Karthickkumar Kathiresan stated in a report.
Details of the marketing campaign had been initial disclosed by Milan-based IT services company SI.net very last thirty day period.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The multi-stage infection sequence commences with an bill-themed phishing email that contains a link that, when clicked, downloads a password-secured ZIP archive file, which harbors two information: A shortcut (.LNK) file and a batch (.BAT) file.
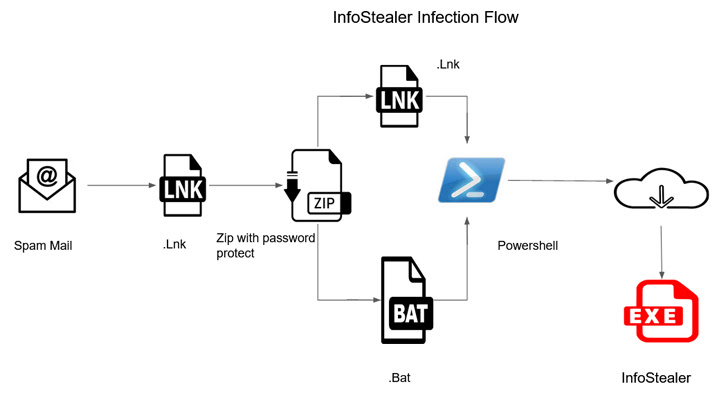
Irrespective of which file is launched, the attack chain stays the similar, as opening the shortcut file fetches the identical batch script created to put in the facts stealer payload from a GitHub repository. This is achieved by leveraging a genuine PowerShell binary that’s also retrieved from GitHub.
Once put in, the C#-based mostly malware gathers process metadata, and information and facts from dozens of web browsers (e.g., cookies, bookmarks, credit cards, downloads, and credentials), as nicely as various cryptocurrency wallets, all of which is transmitted to an actor-controlled domain.
To mitigate this kind of attacks, companies are advised to apply “tight security controls and multi-layered visibility and security options to identify and detect malware.”
Uncovered this article interesting? Follow us on Twitter and LinkedIn to examine extra unique material we post.
Some pieces of this report are sourced from:
thehackernews.com

 Cloud-delivered malware attacks almost tripled in 2022
Cloud-delivered malware attacks almost tripled in 2022