The menace actors driving the Kinsing cryptojacking operation have been spotted exploiting misconfigured and uncovered PostgreSQL servers to receive original obtain to Kubernetes environments.
A next original obtain vector method entails the use of vulnerable images, Sunders Bruskin, security researcher at Microsoft Defender for Cloud, reported in a report past 7 days.
Kinsing has a storied record of targeting containerized environments, usually leveraging misconfigured open up Docker daemon API ports as effectively as abusing recently disclosed exploits to drop cryptocurrency mining program.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The risk actor, in the earlier, has also been found utilizing a rootkit to cover its presence, in addition to terminating and uninstalling competing resource-intense companies and processes.
Now in accordance to Microsoft, misconfigurations in PostgreSQL servers have been co-opted by the Kinsing actor to get an first foothold, with the corporation observing a “massive volume of clusters” infected in this way.
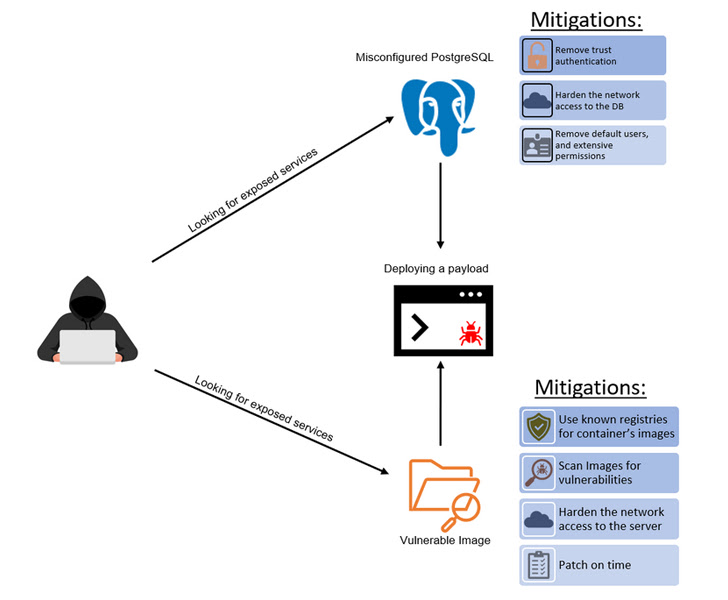
The misconfiguration relates to a trust authentication environment, which could be abused to connect to the servers sans any authentication and obtain code execution must the selection be set up to accept connections from any IP deal with.
“In normal, allowing accessibility to a broad vary of IP addresses is exposing the PostgreSQL container to a opportunity threat,” Bruskin defined.
The different attack vector targets servers with vulnerable variations of PHPUnit, Liferay, WebLogic, and WordPress that are inclined to remote code execution in purchase to operate destructive payloads.
What is actually a lot more, a modern “widespread marketing campaign” associated the attackers scanning for open default WebLogic port 7001, and if found, executing a shell command to start the malware.
“Exposing the cluster to the Internet without correct security steps can depart it open to attack from exterior resources,” Bruskin reported. “In addition, attackers can acquire accessibility to the cluster by having advantage of regarded vulnerabilities in pictures.”
Discovered this write-up attention-grabbing? Observe us on Twitter and LinkedIn to examine much more distinctive content material we post.
Some pieces of this short article are sourced from:
thehackernews.com


 New Study Uncovers Text-to-SQL Model Vulnerabilities Allowing Data Theft and DoS Attacks
New Study Uncovers Text-to-SQL Model Vulnerabilities Allowing Data Theft and DoS Attacks