Phishing attacks are steadily turning into more refined, with cybercriminals investing in new approaches of deceiving victims into revealing delicate information and facts or setting up destructive software. One of the most current developments in phishing is the use of QR codes, CAPTCHAs, and steganography. See how they are carried out and study to detect them.
Quishing
Quishing, a phishing system resulting from the mixture of “QR” and “phishing,” has turn out to be a common weapon for cybercriminals in 2023.
By concealing destructive links inside of QR codes, attackers can evade common spam filters, which are mainly geared towards figuring out text-based mostly phishing makes an attempt. The incapacity of a lot of security tools to decipher the information of QR codes even more can make this approach a go-to option for cybercriminals.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
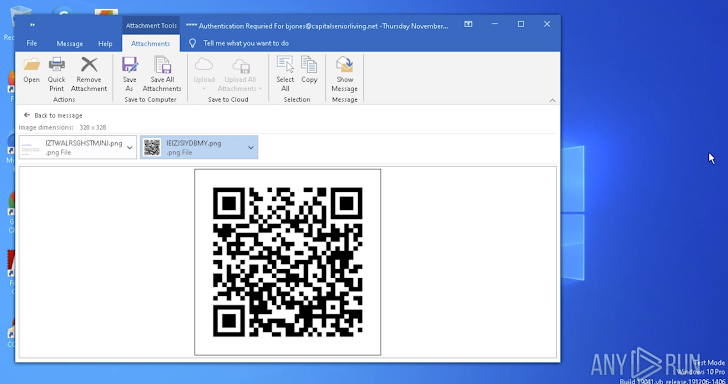 An email that contains a QR code with a malicious website link
An email that contains a QR code with a malicious website link
Analyzing a QR code with an embedded destructive connection in a risk-free surroundings is quick with ANY.Run:
The sandbox will then immediately launch a new job window, allowing you to evaluate the URL discovered inside the QR code.
Black Friday OfferTake advantage of ANY.RUN’s Black Friday Offer you
Invest in an yearly Searcher or Hunter plan membership and get a different for your colleague entirely free of demand. Offered November 20-26.
Get It Now
CAPTCHA-centered attacks
CAPTCHA is a security answer made use of on web-sites to avoid automatic bots from developing pretend accounts or submitting spam. Attackers have managed to exploit this device to their benefit.
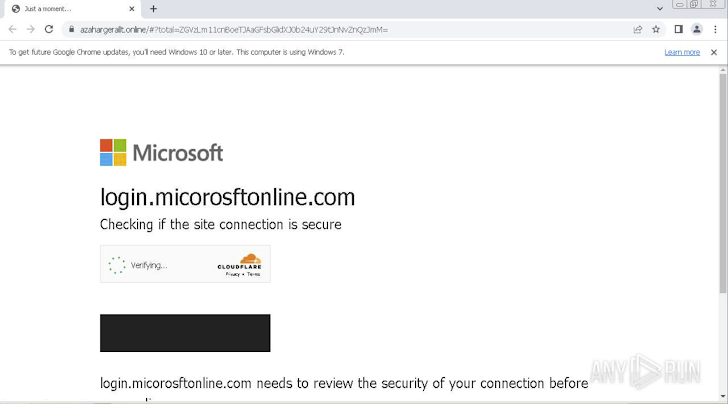 A phishing attack CAPTCHA page shown in the ANY.Operate sandbox
A phishing attack CAPTCHA page shown in the ANY.Operate sandbox
Attackers are more and more using CAPTCHAs to mask credential-harvesting forms on faux websites. By creating hundreds of domain names working with a Randomized Domain Produced Algorithm (RDGA) and utilizing CloudFlare’s CAPTCHAs, they can efficiently conceal these forms from automatic security methods, this kind of as web crawlers, which are not able to bypass the CAPTCHAs.
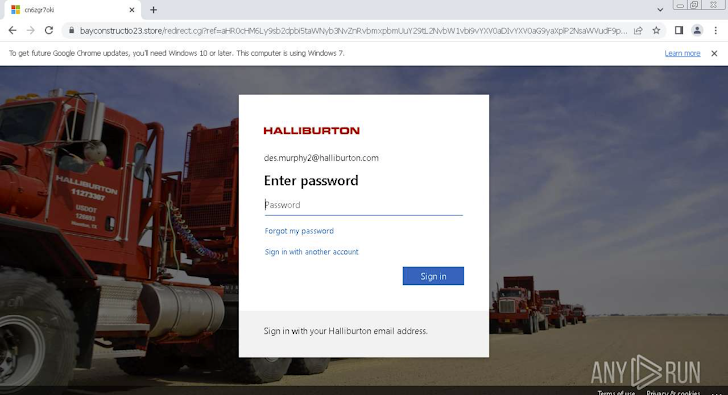 A bogus Halliburton login web site
A bogus Halliburton login web site
The illustration earlier mentioned displays an attack targeting Halliburton Corporation staff members. It initially demands the user to go a CAPTCHA look at and then makes use of a practical Business 365 private login page that is hard to distinguish from the authentic website page.
When the victim enters their login qualifications, they are redirected to a genuine internet site, even though the attackers exfiltrate the credentials to their Command-and-Manage server.
Master far more about CAPTCHA attacks in this post.
Steganography malware strategies
Steganography is the exercise of hiding information inside of diverse media, this kind of as pictures, video clips, or other files.
A usual phishing attack that employs steganography begins with a thoroughly crafted email created to show up authentic. Embedded inside of the email is an attachment, normally a Word document, accompanied by a hyperlink to a file-sharing platform like Dropbox. In the example underneath, you can see a faux email from a Colombian governing administration business.
 A phishing email is typically the to start with stage of an attack
A phishing email is typically the to start with stage of an attack
The unsuspecting user that clicks the backlink inside the document downloads an archive, which includes a VBS script file. Upon execution, the script retrieves an impression file, seemingly harmless but made up of concealed destructive code. At the time executed, the malware infects the victim’s process.
To have an understanding of how steganography attacks are carried out and detected, check out this post.
Expose phishing attacks with ANY.Operate
ANY.Run is a malware evaluation sandbox that is able of detecting a extensive array of phishing practices and permitting buyers take a look at them in detail.
Verify out ANY.RUN’s Black Friday Offer you, readily available November 20-26.

The sandbox offers:
- Entirely interactive Windows 7,9,10,11 digital equipment
- Complete experiences with IOCs and malware configs
- Private investigation of an limitless number of documents and one-way links
Identified this post intriguing? Follow us on Twitter and LinkedIn to examine more special information we post.
Some components of this report are sourced from:
thehackernews.com


 Kinsing Hackers Exploit Apache ActiveMQ Vulnerability to Deploy Linux Rootkits
Kinsing Hackers Exploit Apache ActiveMQ Vulnerability to Deploy Linux Rootkits